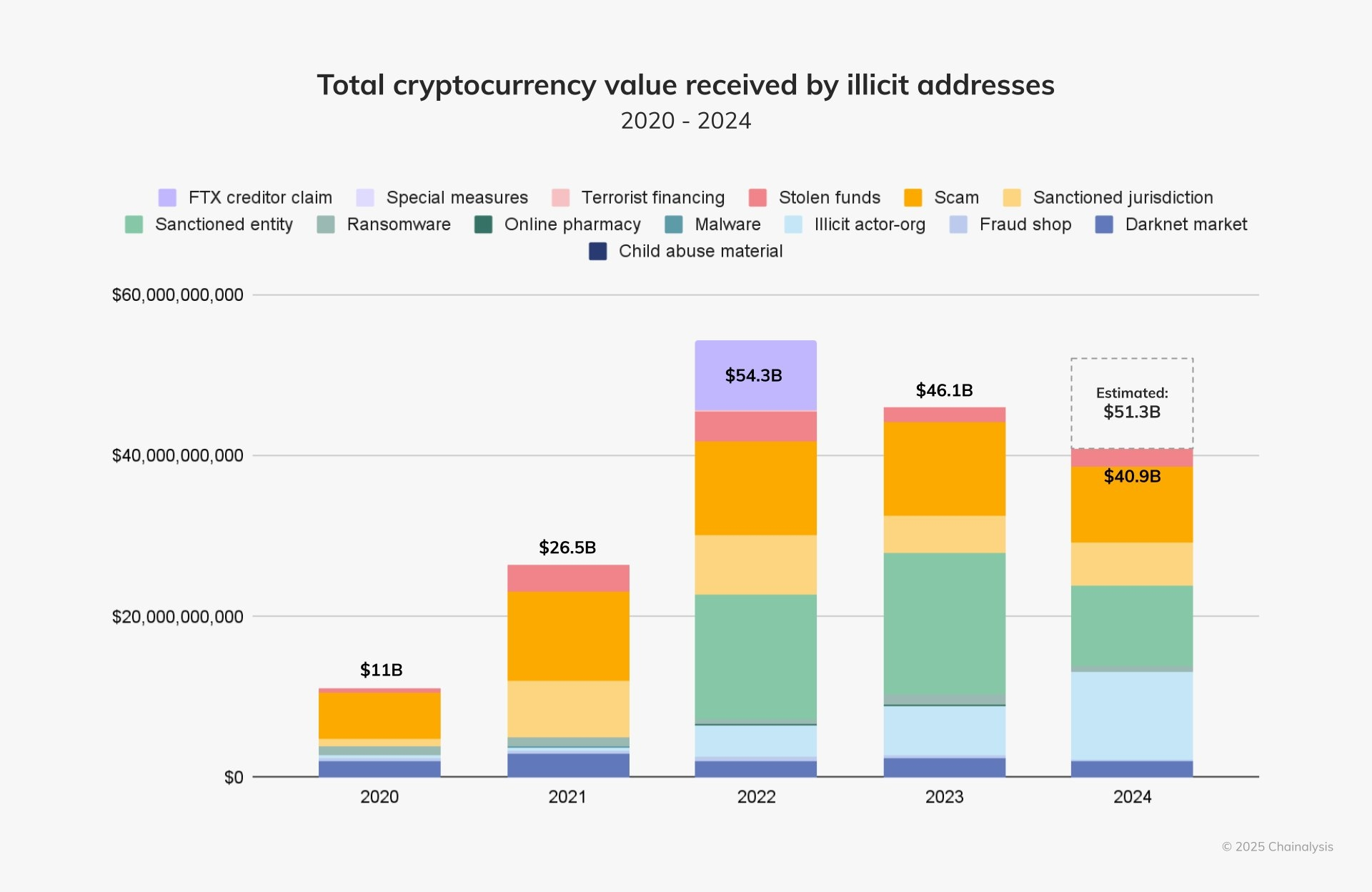
Most people believe that owning a hardware wallet is the final step in crypto security. That assumption is dangerously incomplete. A Ledger can protect you from malware, phishing, and remote attacks. It does nothing against the fastest-growing threat facing crypto holders today: physical coercion.
According to Chainalysis, crypto-related home invasions and physical extortion incidents have increased sharply since 2023. As crypto wealth becomes more visible and more concentrated, attackers no longer need to hack your device. They only need you.
1. The Threat Model Has Changed
Online threats are no longer the primary risk for serious holders. If someone forces you to unlock your wallet under duress, your hardware wallet offers no resistance. At that moment, security becomes psychological, structural, and physical rather than technical.
2. A Decoy Wallet Is Your First Line of Defense
In a worst-case scenario, you need something you can safely give up. A secondary hardware wallet with a completely separate seed phrase, funded with a believable but limited amount, acts as a sacrificial layer. Transaction history, minor assets, and realistic activity make it credible. Its purpose is not storage but deception.

3. Hidden Wallets Add Controlled Disclosure
Some hardware wallets allow the creation of passphrase-protected hidden wallets. One device can therefore contain multiple wallets, only one of which is visible under pressure. This enables staged disclosure, giving you options rather than a single point of failure.
4. Convincing Escalation Preserves the Core
Under coercion, attackers typically escalate until they believe they have extracted everything. A small visible balance followed by a larger decoy balance often satisfies that expectation. What they believe to be your full holdings is not your real portfolio.
5. Your Real Holdings Should Never Touch That Device
Serious holdings should be generated and stored fully offline, using air-gapped devices that never interact with internet-connected hardware. Seed backups should be stored on durable, fireproof, and waterproof metal solutions, never digitally and never on a device used for daily activity.
6. Seed Phrase Obfuscation Removes Single-Point Failure
Splitting a seed phrase across locations, scrambling word order, and separating index information ensures that no single discovery compromises the wallet. Partial information should be useless by design.

7. Reduce Visible Attack Surface
Once the real seed is secured offline, visible devices should contain only decoy wallets. If stolen or forced open, they reveal nothing of value. What cannot be discovered cannot be taken.

8. Physical Security Complements Wallet Security
Home security layers such as silent panic systems, offsite camera storage, and motion alerts reduce response time and increase deterrence. Seed backups should never be stored at your residence.

9. Silence Is the Final Layer
Even the most advanced setup fails if attention is drawn to it. Publicly sharing balances, trades, or security details creates unnecessary risk. Anonymity remains the strongest security primitive.

Final Perspective
If you hold meaningful crypto, your security architecture must be as sophisticated as your investment strategy. Real protection comes from layered deception, offline redundancy, geographic separation, and disciplined silence.
They cannot take what they cannot find, and they will not look for what they do not know exists.
