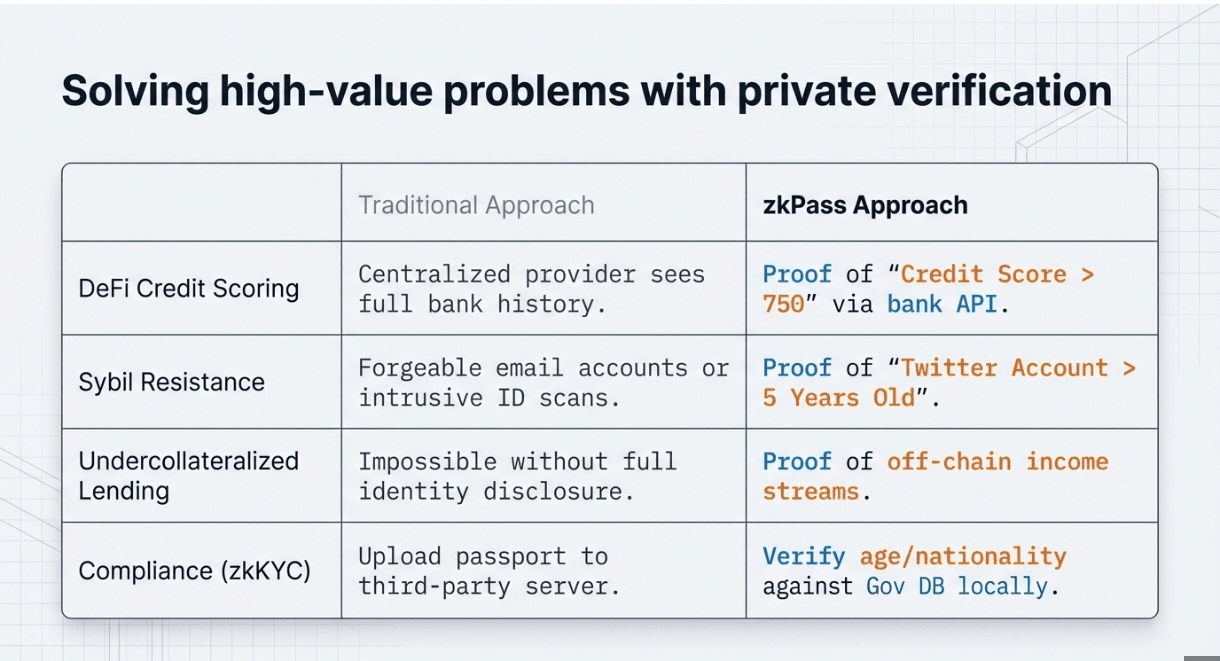
Every click you make online generates data worth thousands of dollars, your credit score, purchase history, social graph, professional credentials. Yet you can't prove you own it without handing over the keys to a third party. The $121 billion digital identity market runs on a complex paradox: to verify you're trustworthy, you must trust someone else with everything.
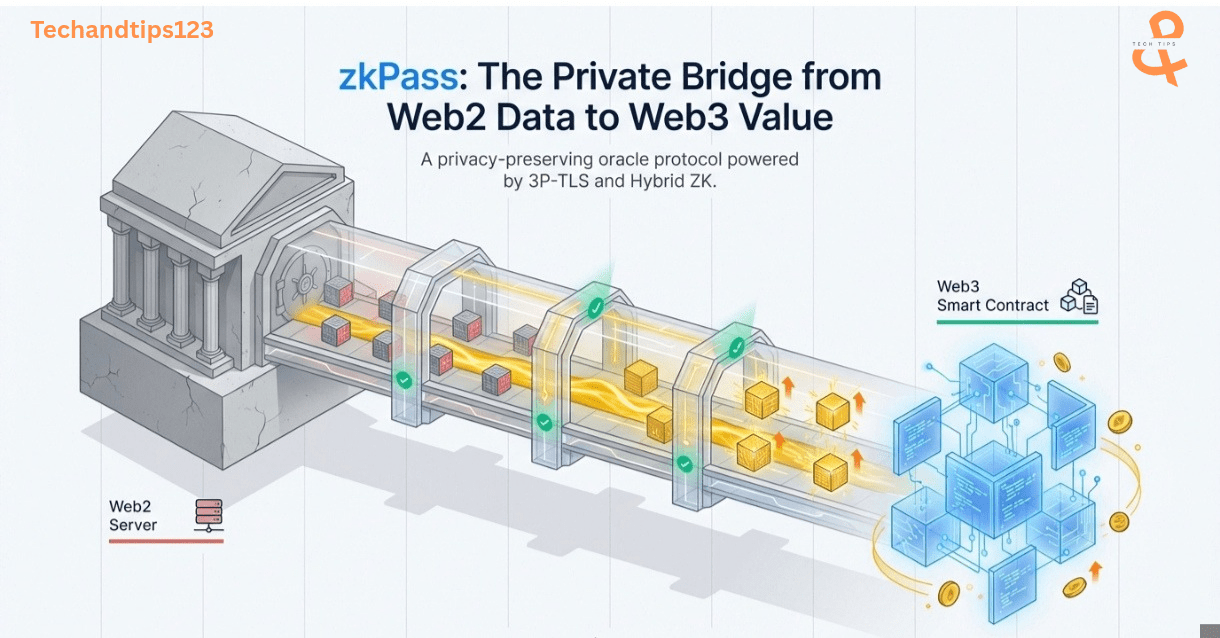
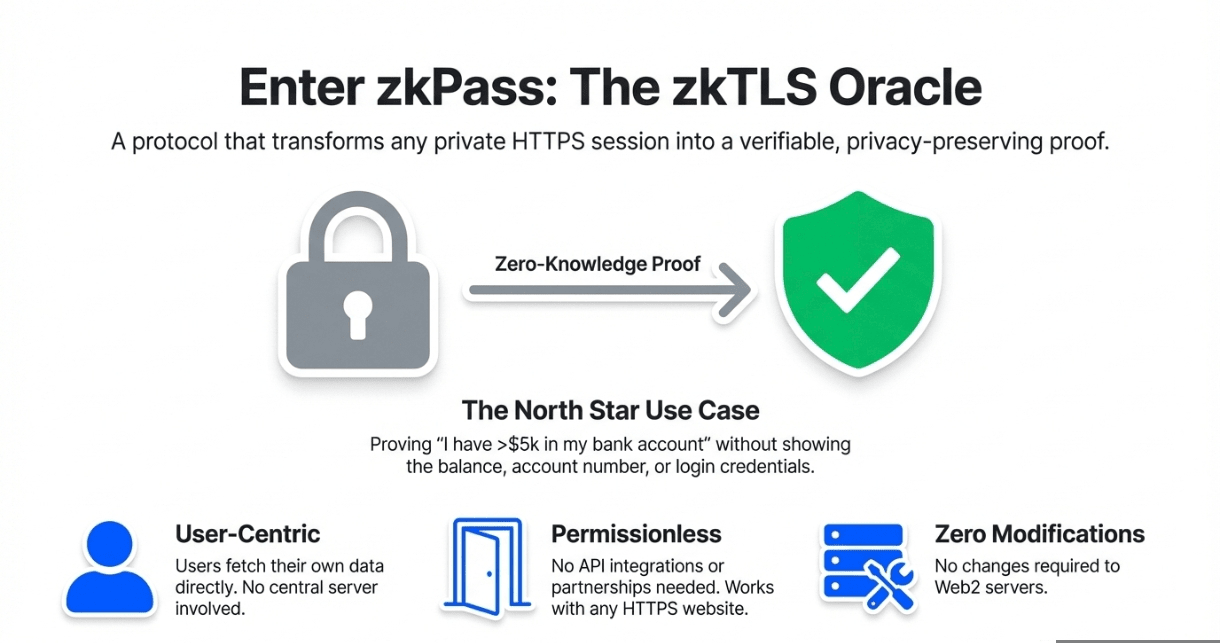
zkPass solves this with a zkTLS oracle protocol. It transforms any HTTPS session,your bank login, LinkedIn profile, Uber ride history,into a verifiable cryptographic proof that lives on-chain. You prove statements about your private data ("I have a credit score above 750" or "I've completed 500 rides") without revealing the underlying information to anyone. No API integrations required. No server modifications needed. Just mathematics.
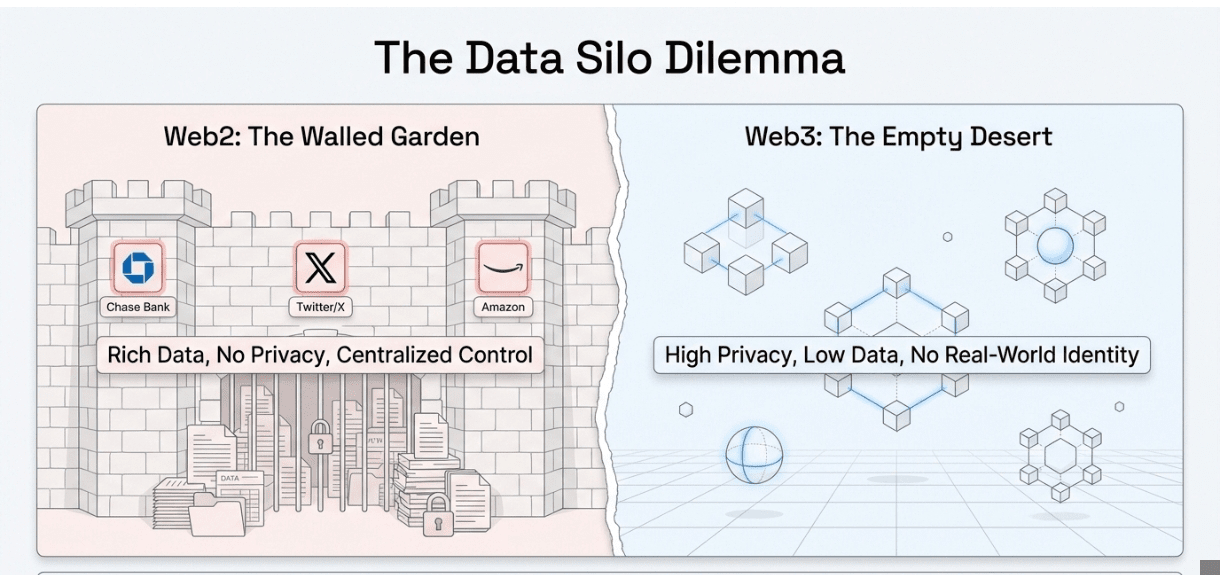
This matters now because Web3 has hit a ceiling. DeFi can't offer undercollateralized loans without KYC. DAOs can't prevent Sybil attacks without doxxing members. Gaming platforms can't verify off-chain achievements. zkPass bridges the $3 trillion Web2 data economy to on-chain applications, turning 200+ data sources,from Binance balances to Duolingo streaks,into privacy-preserving credentials. Since launch, the protocol has generated over 10 million zero-knowledge proofs across 80+ ecosystem integrations, with browser-based proof generation completing in under one second.
▨ The Problem: What's Broken?
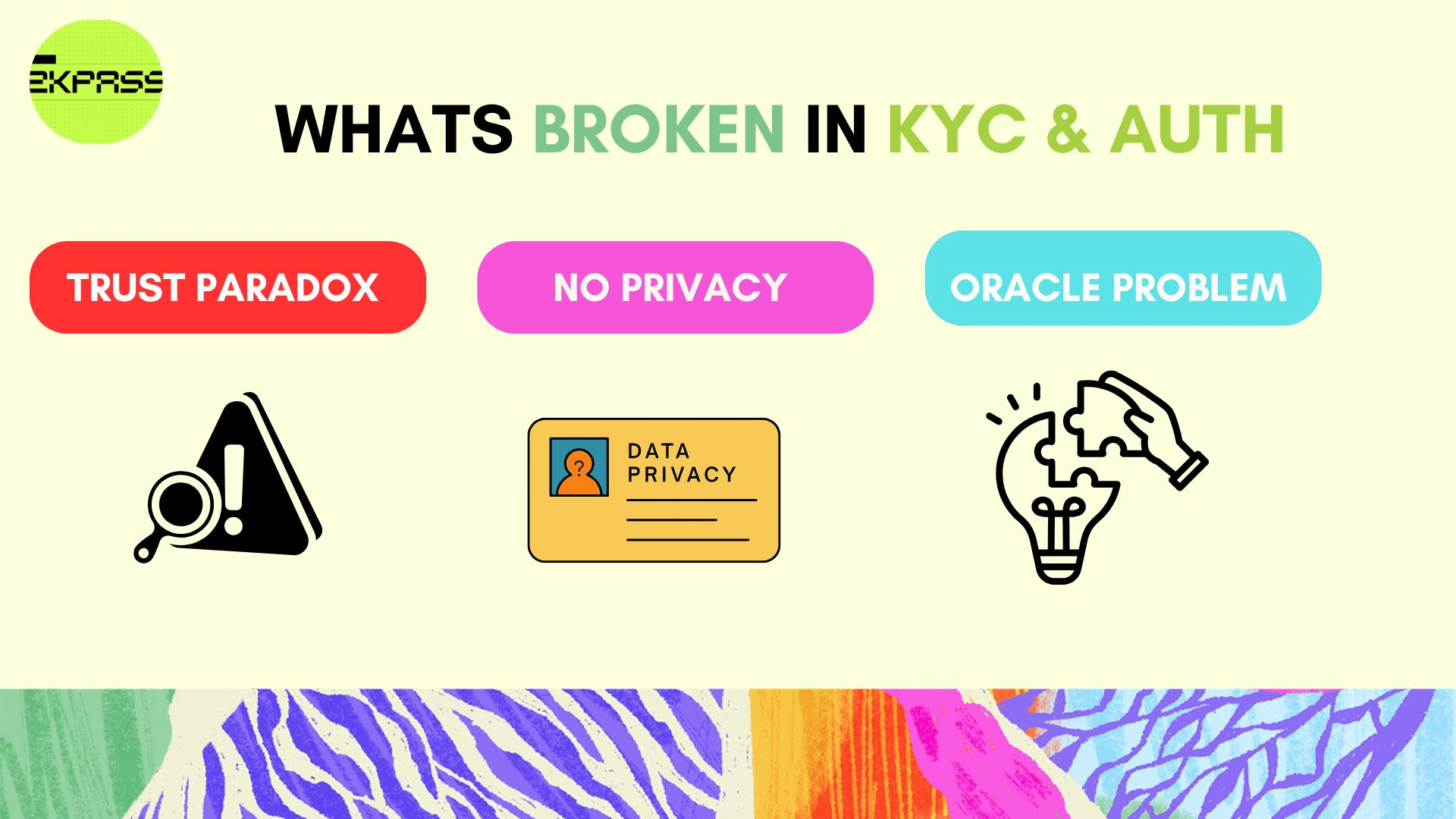
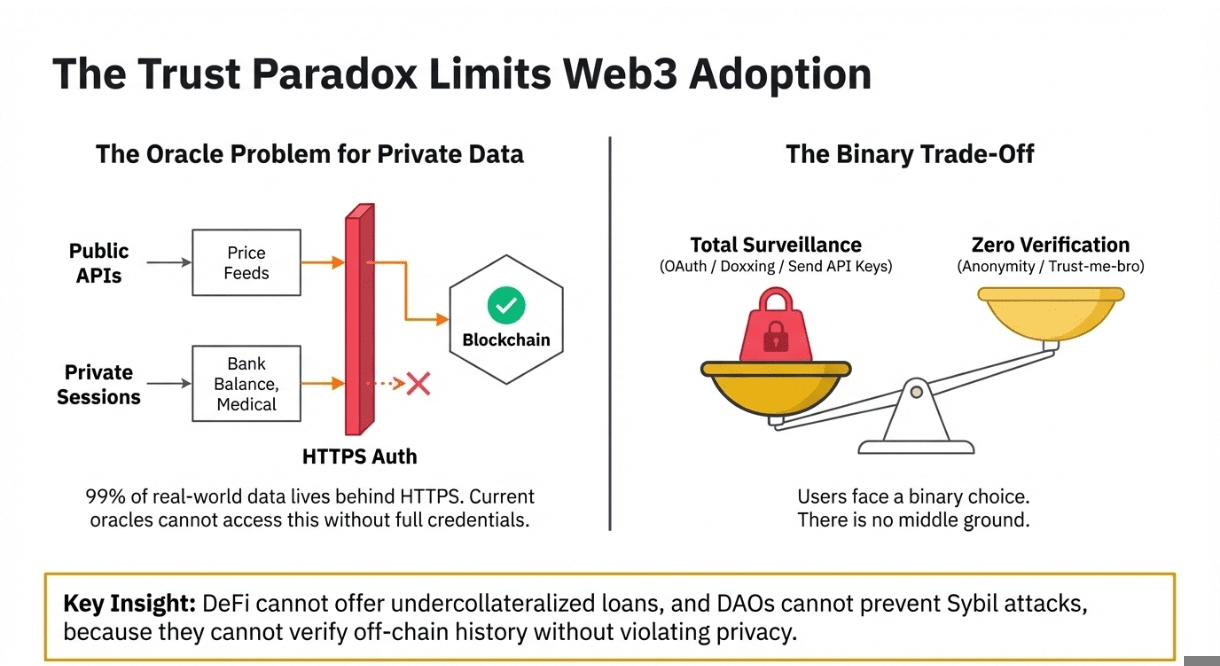
🔹 The Trust Paradox in Data Verification → Web3 applications that need real-world credentials face an impossible choice: accept self-reported data (easily forged) or integrate centralized oracles that see everything. DeFi protocols can't verify credit scores without partnering with data brokers. Airdrops can't confirm Twitter followers without API keys. Every verification introduces a new trusted intermediary, recreating the centralization Web3 was meant to escape.
🔹 Privacy as a Binary Trade → Current solutions force all-or-nothing data exposure. OAuth gives applications full account access just to prove one fact. KYC providers store complete identity documents to verify age. Attestation services see transaction histories to confirm balances. There's no middle ground between zero verification and total surveillance,users either stay anonymous or surrender everything.
🔹 The Oracle Problem for HTTPS Data → Blockchain oracles handle price feeds and public APIs well, but private, authenticated web sessions remain inaccessible. Your bank balance, healthcare records, employment history, and subscription status all live behind HTTPS authentication that oracles can't touch without your credentials. This locks 99% of real-world data out of Web3, limiting applications to on-chain primitives and publicly scraped information.
🔹 Infrastructure Lock-In and Integration Hell → Each data source requires custom API integrations, legal agreements, and server-side modifications. Projects spend months negotiating with platforms like LinkedIn or Coinbase for data access. Rate limits, API changes, and access revocations create fragile dependencies. Developers can't build portable, user-owned credentials,they're stuck begging gatekeepers for permission to access users' own data.
▨ What zkPass Is Doing Differently
zkPass changed the verification model by putting users in control of data fetching and proof generation. Instead of applications requesting data from servers, users retrieve their own private information through standard HTTPS sessions, then generate zero-knowledge proofs about it locally in their browser. The verifying application only sees the proof, never the underlying data.
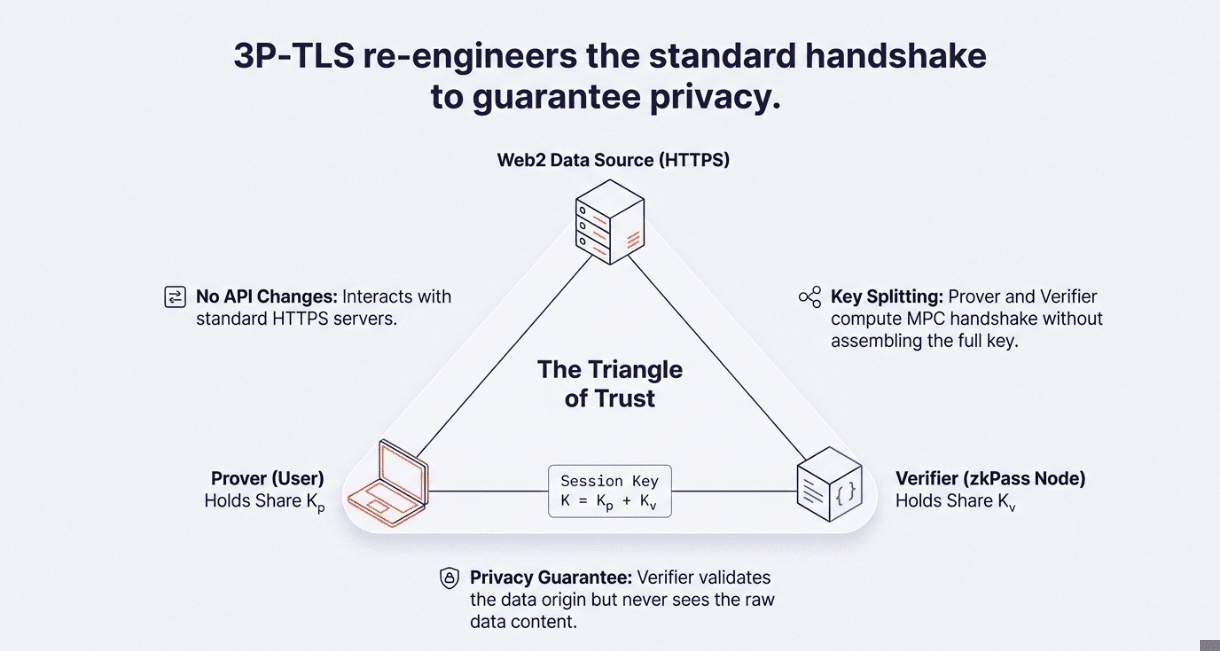
This works through a protocol called three-party TLS (3P-TLS), which extends the normal two-party TLS handshake between your browser and a website to include a third party,the verifier,without giving them decryption access. The protocol splits cryptographic keys using multi-party computation (MPC) so the verifier holds only the session integrity key (which confirms data wasn't tampered with) while the user keeps the encryption key private. After the HTTPS session completes, the user generates a zero-knowledge proof about the recorded data using advanced cryptographic techniques like VOLE-in-the-Head (VOLEitH) and ICP-ZKP.
The genius is in the details. During the 3P-TLS handshake, the Prover (user) commits to their key share before learning the full session key,this prevents them from forging data later. The Verifier reveals their key share and records all traffic, but because they don't have the encryption key, they can't read it. The DataSource (the HTTPS server like your bank or LinkedIn) operates normally with zero modifications required. Once the session ends, the Prover runs a ZK proof circuit over the recorded traffic, creating a commitment like d = commit(m, r) where m is the message and r is randomness. The Verifier validates this commitment without ever learning m.
zkPass operates in Hybrid Mode to handle real-world network constraints. In Proxy Mode, the Verifier acts as a network proxy, recording traffic between Prover and DataSource. In MPC Mode, Prover and Verifier jointly act as the client to the DataSource, splitting the TLS connection. The protocol switches modes automatically when servers block proxy IPs or when network configurations demand different approaches. This adaptability means zkPass works with virtually any HTTPS endpoint,from banking APIs to social platforms to e-commerce sites.
The architecture eliminates three critical setbacks. First, no DataSource integration is needed,if it speaks HTTPS, it works with zkPass. Second, privacy is cryptographically guaranteed rather than policy-based,verifiers mathematically cannot access raw data. Third, proofs are portable and reusable,generate once, verified anywhere on-chain.
▨ Key Components & Features
1️⃣ zkTLS Oracle Protocol
This is the core engine combining 3P-TLS, MPC, and zero-knowledge proofs to turn HTTPS sessions into verifiable credentials. It extends standard TLS with elliptic curve Diffie-Hellman key exchange, oblivious transfer for anti-cheating, and MAC key splitting,allowing integrity verification without decryption. The protocol requires no modifications to existing web servers, making it compatible with 200+ data sources from day one.
2️⃣ TransGate SDK & Developer Tools
The TransGate SDK provides browser-based, mobile-optimized proof generation with sub-second execution times. Developers integrate zkPass into dApps with a few lines of JavaScript, accessing pre-built schemas for common data sources (financial institutions, social platforms, educational credentials, e-commerce). The SDK handles the cryptographic complexity,MPC key generation, proof circuits, on-chain verification,while exposing simple APIs for requesting and validating proofs.
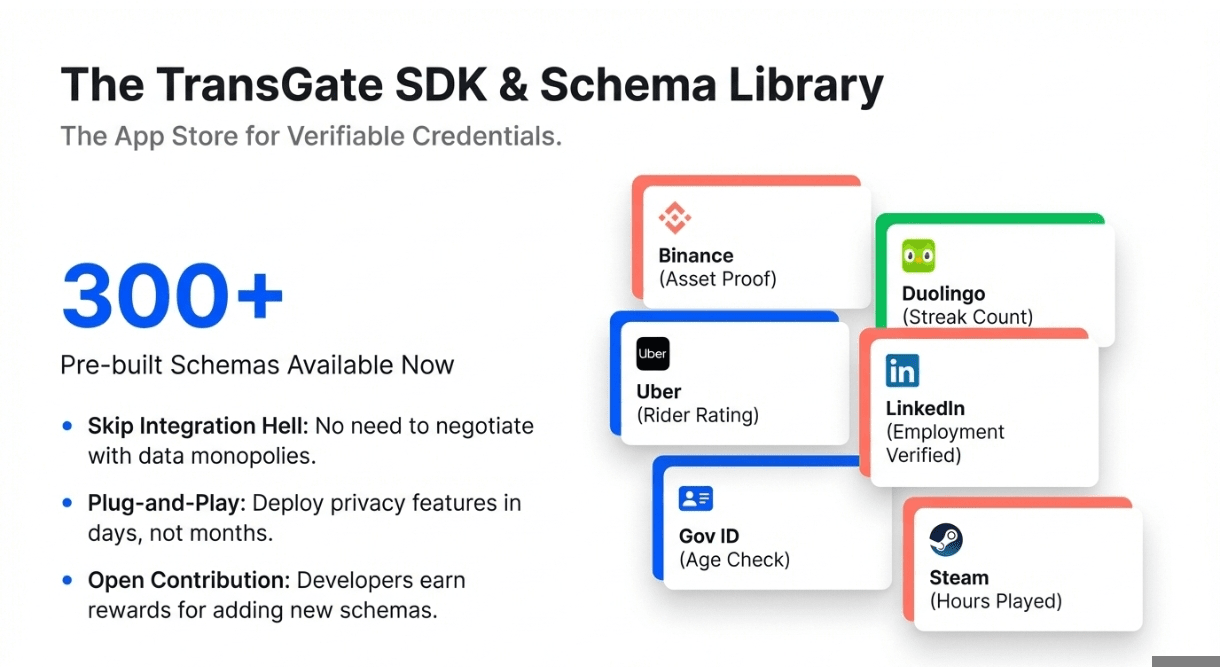
3️⃣ Schema Library (300+ Templates)
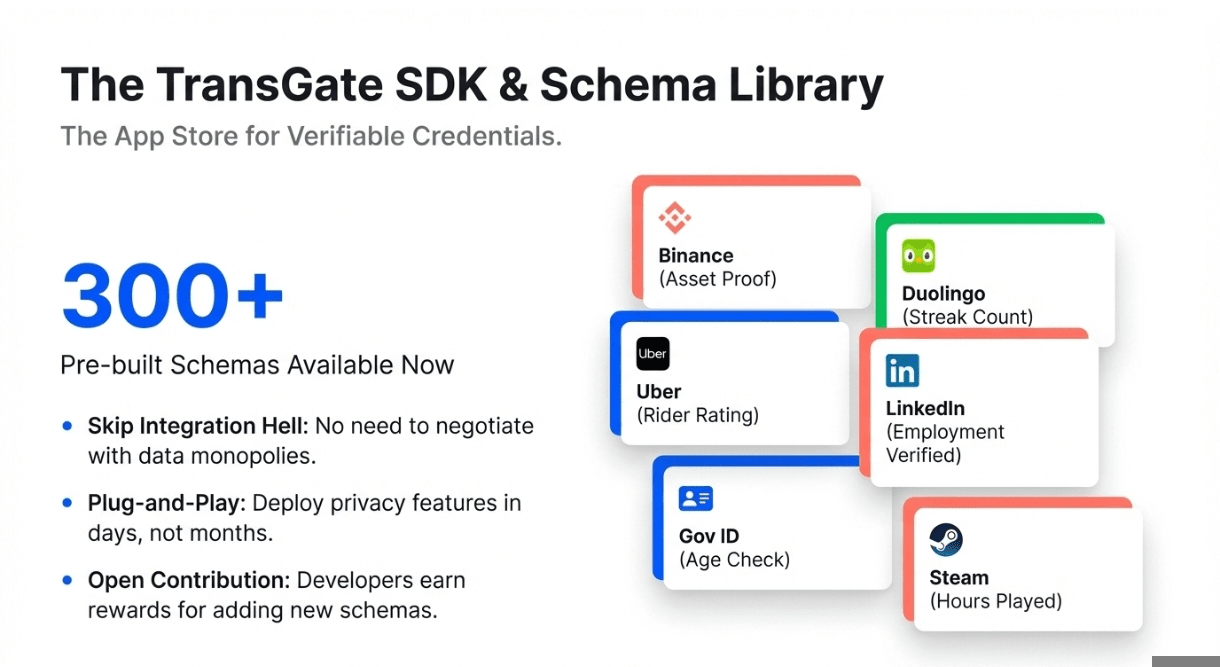
zkPass maintains a growing library of data schemas across financial services, identity verification, social proof, gaming achievements, and educational credentials. Each schema defines extractable fields and provable statements,like "account balance exceeds $10,000" from bank APIs or "follower count above 5,000" from Twitter. Projects contribute new schemas through the ecosystem bounty program, expanding coverage of verifiable Web2 data without central coordination.
4️⃣ Hybrid Proxy/MPC Architecture
The protocol dynamically switches between Proxy Mode and MPC Mode based on network topology and server restrictions. Proxy Mode offers simpler traffic recording when servers accept intermediary IPs. MPC Mode enables direct server connections when proxies are blocked, with both Prover and Verifier jointly establishing the TLS session. This flexibility ensures universal HTTPS compatibility regardless of server policies or network configurations.
5️⃣ VOLEitH Proof System
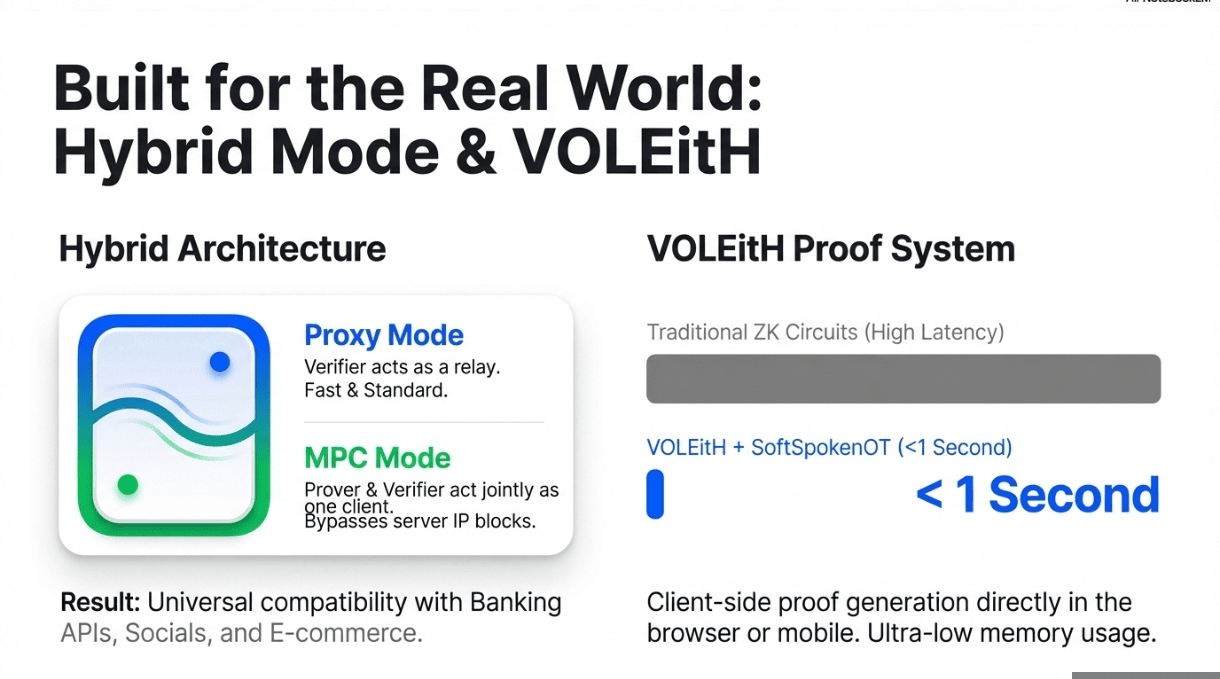
VOLE-in-the-Head (VOLEitH) and SoftSpokenOT form the cryptographic backbone for efficient zero-knowledge proofs. These techniques enable client-side proof generation with low memory consumption and millisecond-level verification,critical for mobile devices and browser environments. The system produces succinct proofs for large-scale data circuits, allowing complex statements about HTTPS responses without revealing content.
6️⃣ Cross-Chain Verification Layer
Built on LayerZero's OFT standard, zkPass proofs verify across Ethereum, BNB Chain, Base, and other EVM chains with deterministic contract addresses. Proofs generated on one chain can be consumed by applications on another, enabling portable credentials for cross-chain DeFi, identity, and reputation systems. The verification layer connects 80+ ecosystem partners spanning DeFi protocols, social graphs, gaming platforms, and AI applications.
▨ How zkPass Works
🔹 Step 1: User Initiates Verification Request
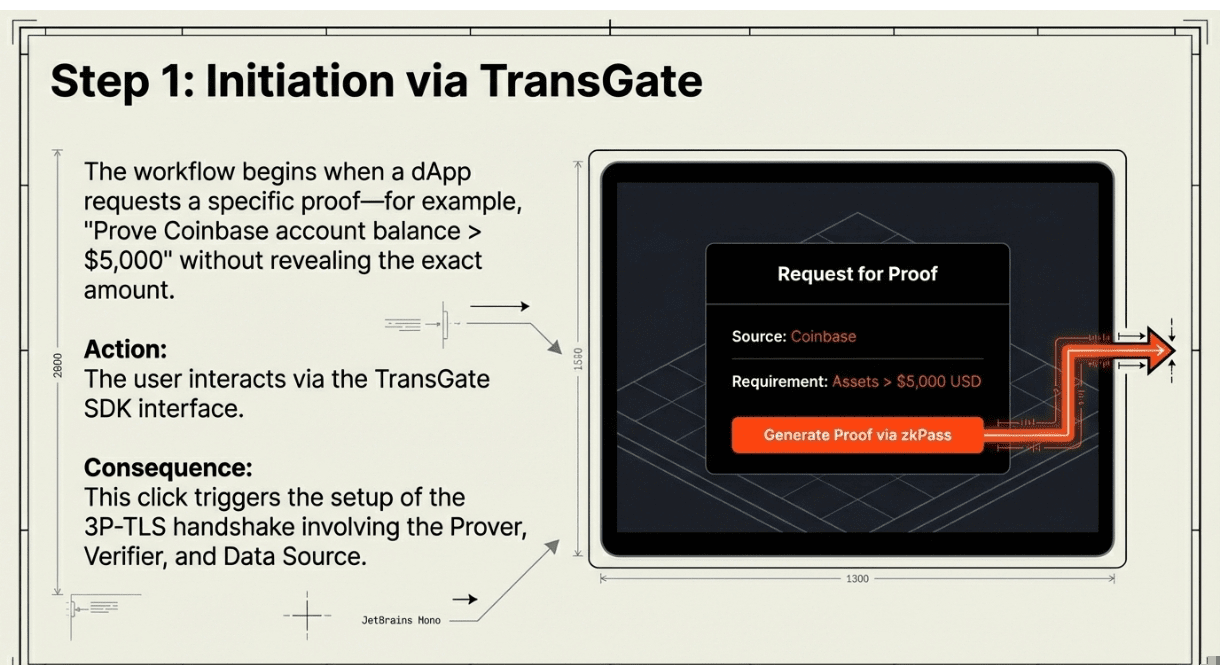
A dApp requests specific proof from the user,for example, "prove your Coinbase account balance exceeds $5,000 without revealing the exact amount." The user clicks through the TransGate SDK interface, which triggers the 3P-TLS handshake among three parties: the user's browser (Prover), the dApp's verification service (Verifier), and the data source server (DataSource, in this case Coinbase's API endpoint).
🔹 Step 2: 3P-TLS Handshake Establishes Split Keys
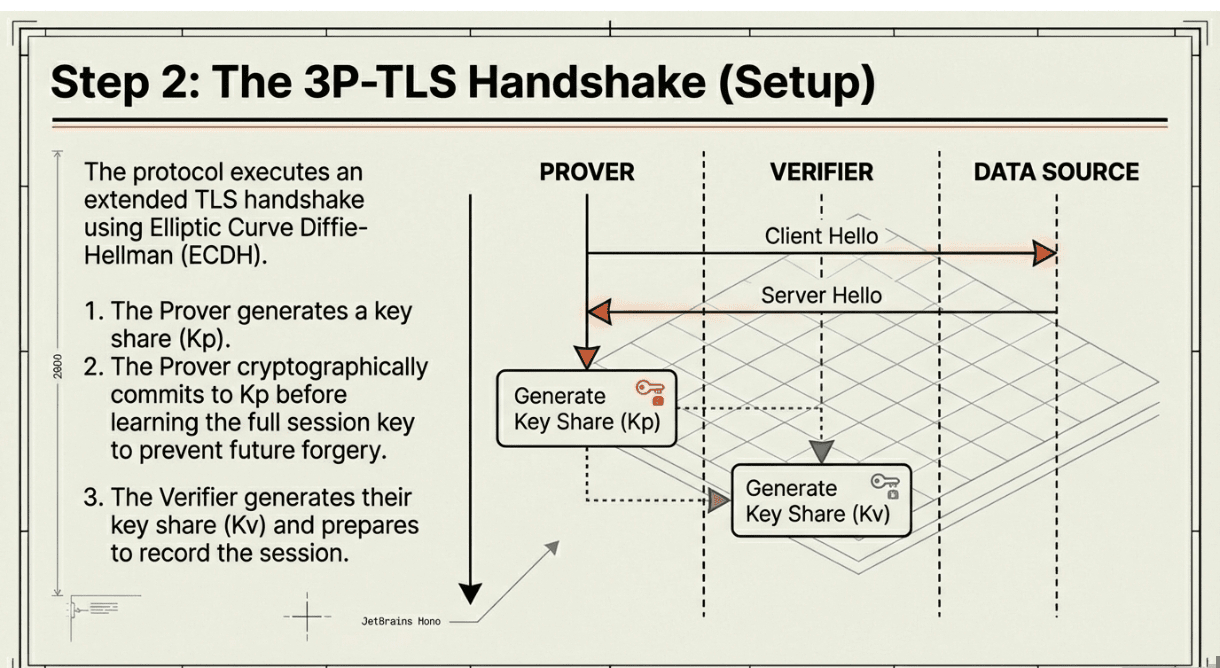
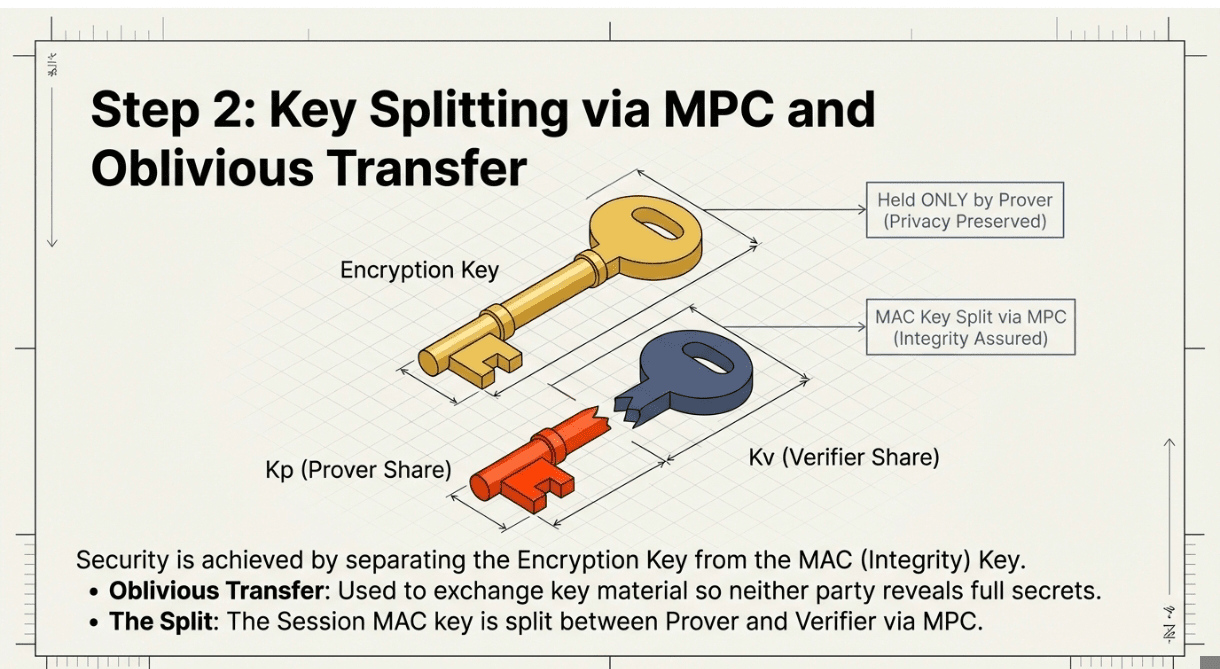
The protocol executes an extended TLS handshake using elliptic curve Diffie-Hellman. The Prover generates their key share K_p and commits to it cryptographically before learning the full session key,this commitment prevents later data forgery. The Verifier simultaneously generates their key share K_v and records a nonce from the DataSource for server authentication. Both parties use oblivious transfer to exchange key material without revealing full secrets. Critically, the session MAC key (for integrity checking) is split between Prover and Verifier via MPC, but only the Prover receives the encryption key.
🔹 Step 3: Data Fetching Through Hybrid Mode
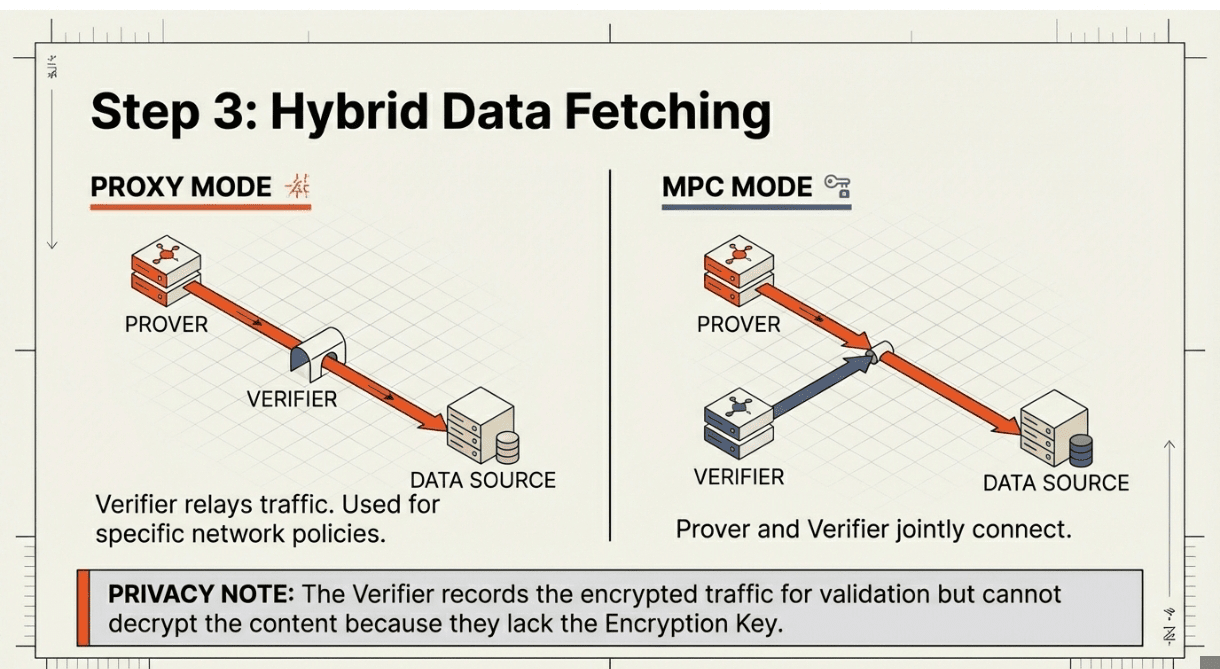
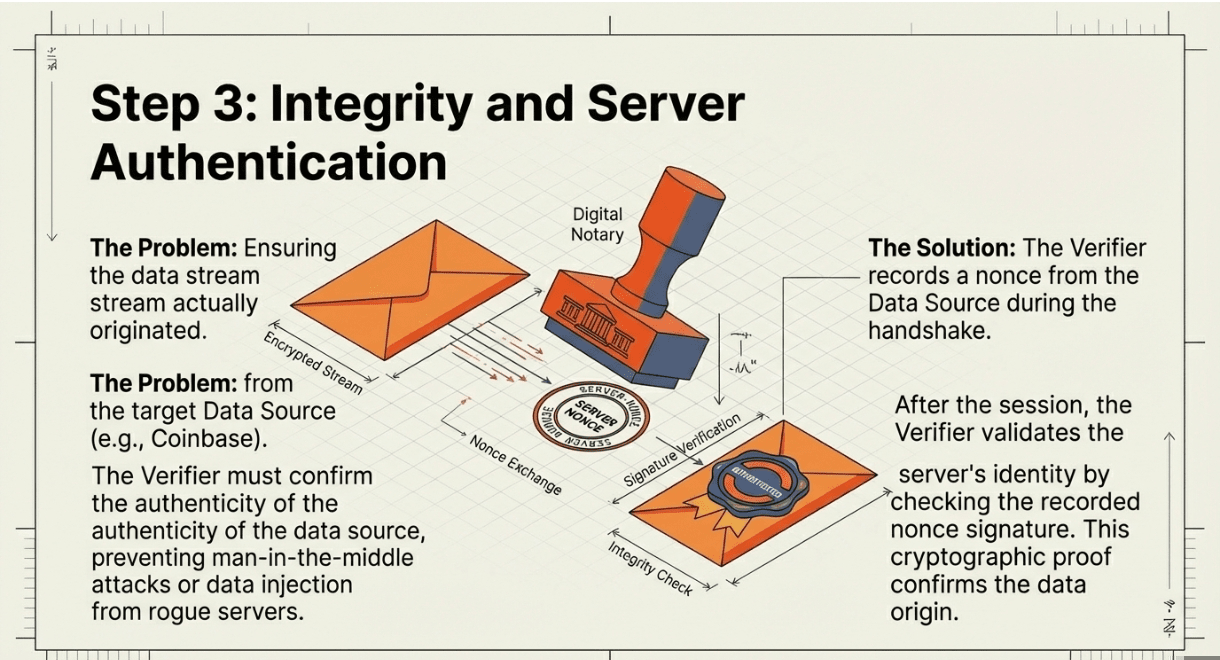
Depending on network conditions and server policies, the protocol operates in Proxy Mode (Verifier relays traffic) or MPC Mode (Prover and Verifier jointly connect). The Prover authenticates to the DataSource using their real credentials,username, password, OAuth token,and fetches the requested data. The Verifier records all encrypted traffic but cannot decrypt it. The DataSource responds normally, unaware that a verification protocol is running. After the session completes, the Verifier validates the server's identity by checking the recorded nonce signature, ensuring the data came from the legitimate source.
🔹 Step 4: Zero-Knowledge Proof Generation
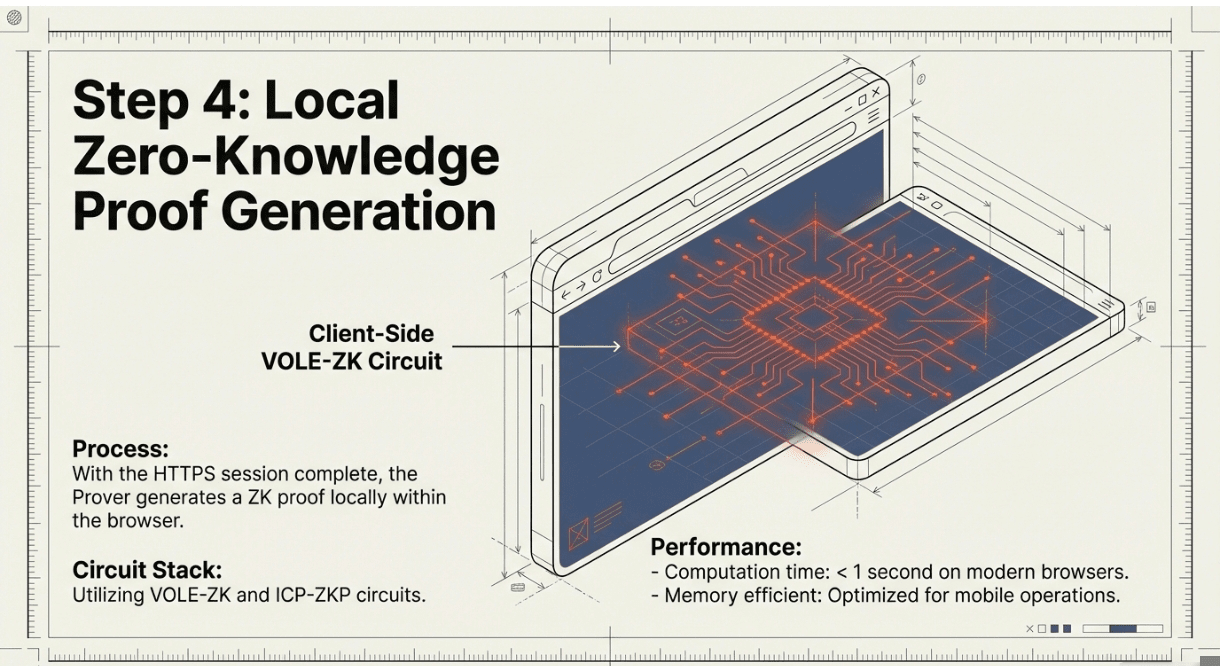
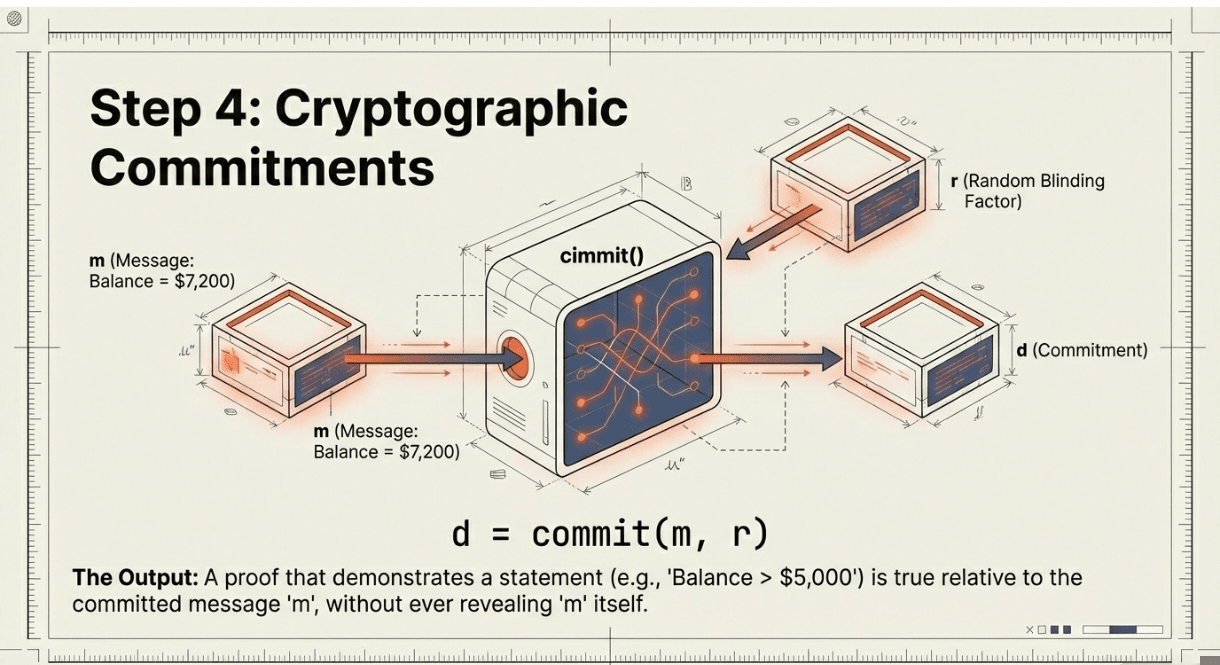
With the HTTPS session complete and traffic recorded, the Prover generates a zero-knowledge proof about the data locally in their browser. Using VOLE-ZK and ICP-ZKP circuits, they create a cryptographic commitment d = commit(m, r) where m represents the message content (like "balance = $7,200") and r is random blinding. The proof demonstrates specific statements,"balance > $5,000" in this example,without revealing the underlying message. The VOLEitH proof system enables this computation in under one second on modern browsers, with memory-efficient operations suitable for mobile devices.
🔹 Step 5: On-Chain Verification and Application Consumption
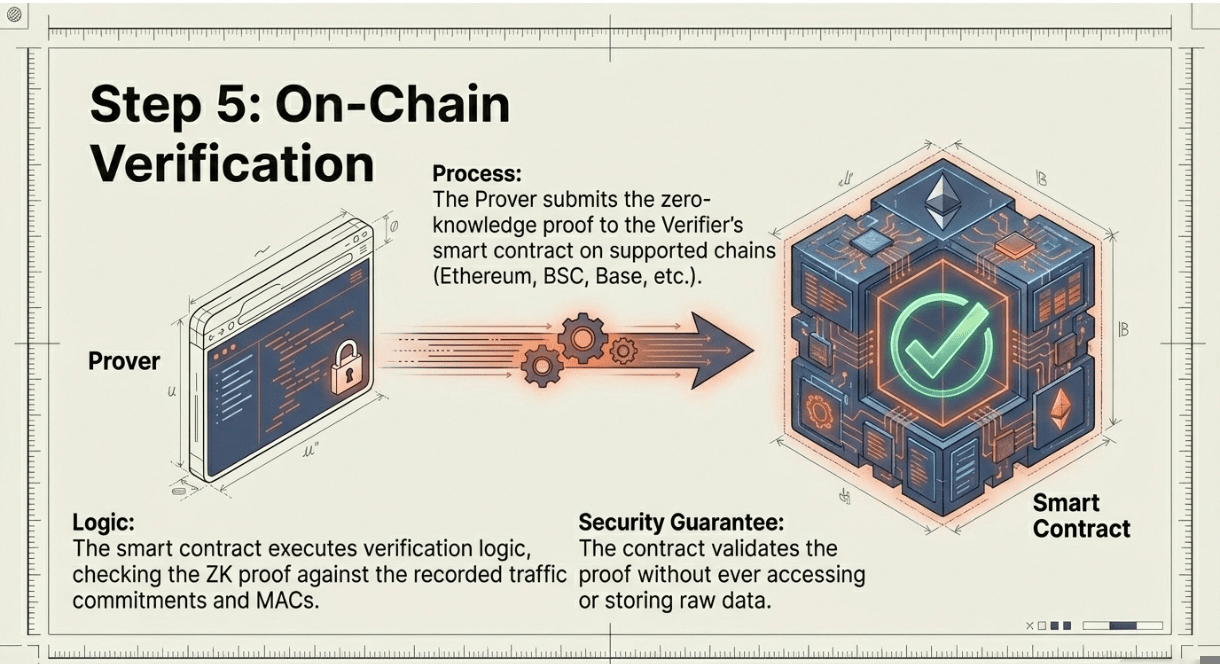
The Prover submits the zero-knowledge proof to the Verifier's smart contract on-chain (Ethereum, BSC, Base, or other supported chains). The contract executes verification logic, checking the cryptographic proof against the recorded traffic and MAC commitments without accessing raw data. If valid, the contract issues an attestation or credential that the dApp can consume,unlocking undercollateralized loans, gated access, airdrop eligibility, or reputation scores.
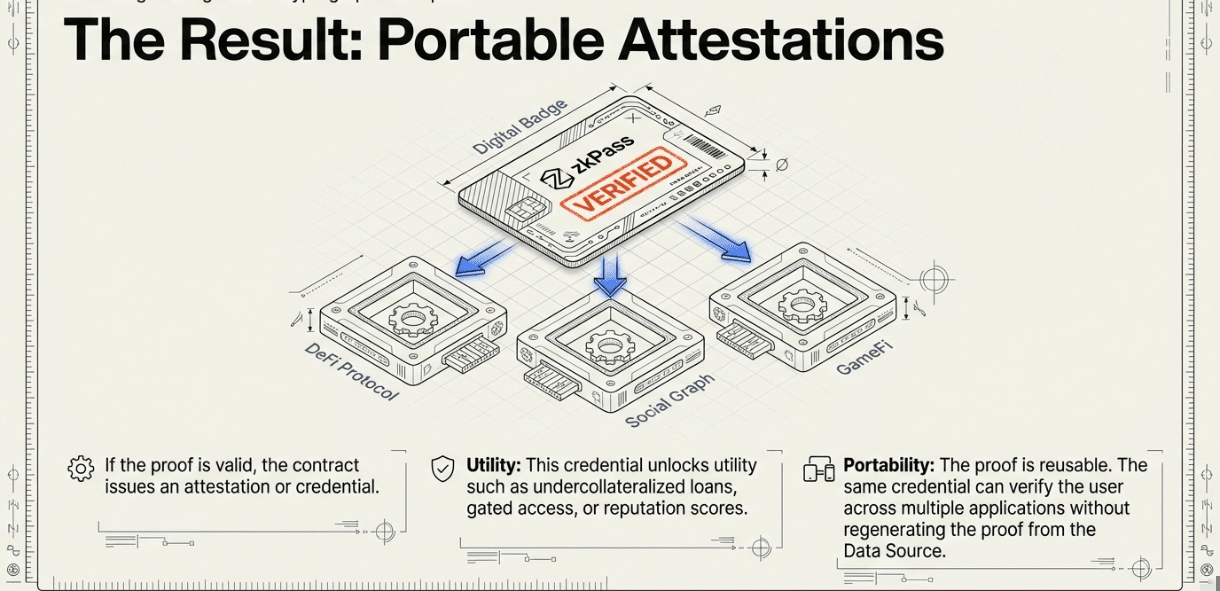
The proof is portable and reusable; the same credential can verify across multiple applications without regenerating from the DataSource.
▨ Value Accrual & Growth Model
✅ Universal Web2-to-Web3 Bridge for Privacy-Preserving Credentials
zkPass addresses demand across DeFi (credit scoring for undercollateralized lending), identity (Sybil-resistant verification without doxxing), gaming (off-chain achievement validation), and compliance (zkKYC for exchanges). With 300+ schemas covering financial, social, educational, and e-commerce data, the protocol unlocks use cases that previously required centralized intermediaries or total data exposure. Partnerships with protocols like Orochi Network (zkDatabase integration), Push Chain (universal privacy dApps), and 80+ ecosystem partners drive adoption across DeFi, AI, and RWA sectors.
✅ Developer Incentives Through Open Schema Contributions
The Verifiable Application Acceleration Program (VAAP) allocated $5.5M to support ecosystem development, funding 1M+ attested users across integrations with platforms like Binance, Coinbase, Duolingo, Uber, and LinkedIn. Developers earn rewards for contributing new schemas, expanding protocol coverage without central bottlenecks. The TransGate SDK reduces integration time from months (traditional API negotiations) to days (schema deployment), accelerating time-to-market for privacy-focused applications.
✅ Network Effects from Reusable, Portable Proofs
Each proof generated strengthens the ecosystem,credentials verified once can be consumed by multiple applications across chains, reducing redundant data fetching and proof generation. As more dApps integrate zkPass verification, the value of holding verifiable credentials increases for users. Protocols building on zkPass (identity layers, lending markets, reputation systems) create demand for proof generation and verification, reinforcing adoption loops. Cross-chain compatibility via LayerZero OFT standard amplifies this effect by enabling credentials to flow seamlessly across Ethereum, BSC, Base, and beyond.
✅ Scalability Through Client-Side Computation and Hybrid Architecture
Unlike oracle models that centralize data fetching, zkPass distributes proof generation to client devices,browsers and mobile apps handle the cryptographic work. This architecture scales horizontally with user adoption rather than requiring centralized infrastructure expansion. The Hybrid Proxy/MPC Mode adapts to diverse network environments and server policies, maintaining universal HTTPS compatibility without service degradation. Sub-second proof generation times (enabled by VOLEitH optimizations) support high-throughput applications like real-time trading verification or instant credential checks.
✅ Flywheel from Integration Density and Data Source Expansion
Initial adoption in high-value verticals (DeFi credit, zkKYC) demonstrates proof-of-concept and attracts adjacent use cases (gaming achievements, social proof, educational credentials). Each new schema increases protocol utility for developers, driving more integrations. More integrations generate more proofs, expanding the on-chain credential graph and attracting additional applications seeking verifiable data. As the schema library grows from 300+ to thousands of data sources, zkPass becomes the default infrastructure for privacy-preserving Web2-Web3 bridges,shifting from niche tool to essential verification layer.
▨ Token Utility & Flywheel
The $ZKP token launched in December 2025 via a $3M IDO, with total supply of 1 billion and 201.7M circulating as of January 2026. Trading at approximately $0.15 with $70-72M daily volume across 10 exchanges, the token is deployed on Ethereum and BSC with cross-chain support via LayerZero OFT standard.
Token Use Cases
Payments: Applications consuming zkPass proofs pay $ZKP for verification services,dApps integrating zkKYC, credit scoring, or Sybil resistance compensate the network for proof validation and on-chain attestation generation.
Rewards: Contributors who expand the schema library, run verification nodes, or participate in ecosystem development earn $ZKP incentives through the VAAP program and ongoing grants, aligning protocol growth with economic value distribution.
Staking: Verifier nodes stake $ZKP to participate in proof validation and attestation issuance, securing the network through economic skin-in-the-game and earning proportional rewards from verification fees.
Governance: Token holders govern protocol parameters like verification fee structures, schema approval processes, cross-chain expansion priorities, and treasury allocation for ecosystem development.
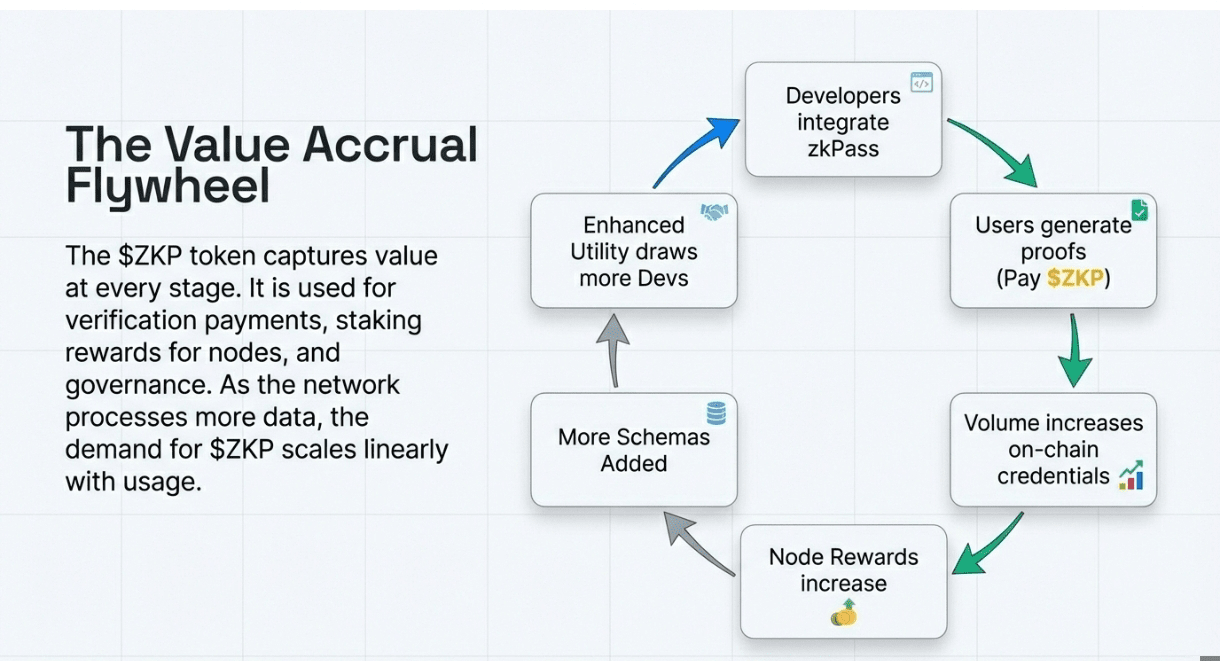
The Protocol Flywheel
zkPass creates a self-reinforcing loop anchored by proof utility and network expansion. As more dApps integrate zkPass verification,DeFi protocols requiring credit scores, DAOs implementing Sybil resistance, gaming platforms validating achievements,demand for proof generation increases. This drives users to create verifiable credentials from their Web2 data, expanding the on-chain credential graph.
Each new schema added to the library (currently 300+ across financial, social, educational, and e-commerce sources) makes the protocol more valuable to developers, accelerating integration. More integrations mean more verification requests, which increase fee revenue for staked verifier nodes. Higher node revenue attracts additional verifiers, improving network decentralization and reliability.
The economic model compounds through reusable credentials,proofs generated once verify across multiple applications and chains. A user proving their Coinbase balance for one DeFi protocol can reuse that credential for airdrops, DAO participation, or social reputation without regenerating from the DataSource. This reduces friction and increases proof consumption, driving verification volumes and fee accumulation.
Token utility grows in parallel, applications pay $ZKP for verifications, nodes stake $ZKP to earn fees, developers receive $ZKP grants for schema contributions, and governance participants direct $ZKP treasury toward high-impact integrations. As the schema library reaches thousands of sources and proof volumes scale from 10 million to billions, zkPass transitions from specialized tool to fundamental infrastructure for privacy-preserving credentials,capturing value from the entire flow of Web2 data into Web3 applications.