
🌱 Opening Thought: Architecture Is Destiny
Many blockchains fail not because of bad ideas…
…but because of bad architecture 😅
The Dusk Foundation approached blockchain design differently:
• Privacy first
• Finality guaranteed
• Regulation supported
• Zero-knowledge everywhere
Everything in Dusk Network flows from this architectural mindset, clearly documented in the protocol design .
🏗️ The Two-Layer Design Philosophy
Dusk Network is built around two tightly connected layers:
🔹 1. Native Asset Layer (DUSK Layer)
• Handles staking
• Pays transaction fees
• Secures consensus
• Powers validator incentives
🔹 2. General Compute Layer
• Smart contracts
• Confidential applications
• Zero-knowledge verification
• Privacy-preserving logic
👉 Same state space.
👉 Different responsibilities.
👉 Clean separation = fewer exploits.
This dual-layer approach avoids congestion and keeps privacy logic native, not bolted on.
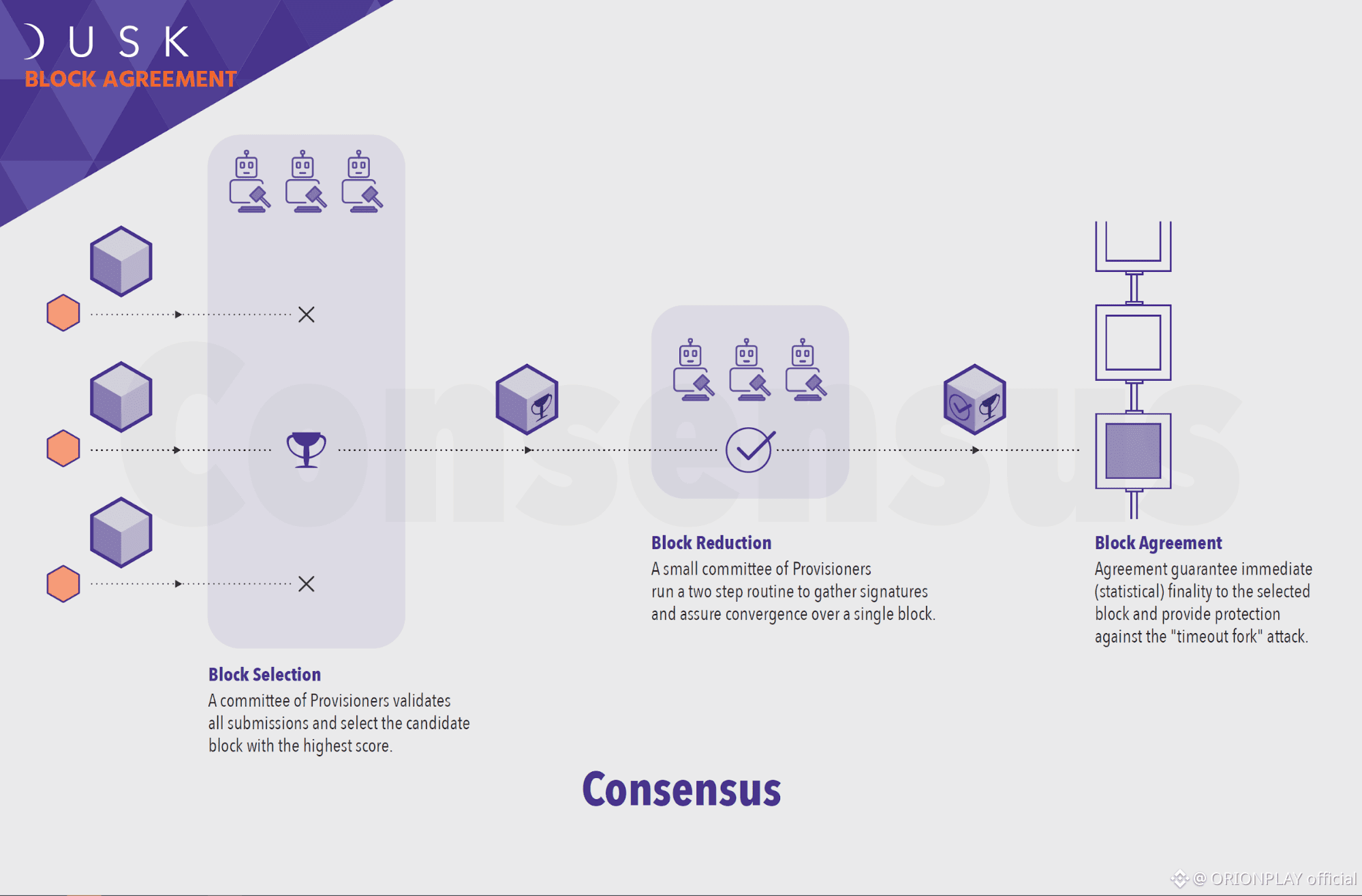
⚖️ Consensus Architecture: Why SBA Replaces Traditional PoS
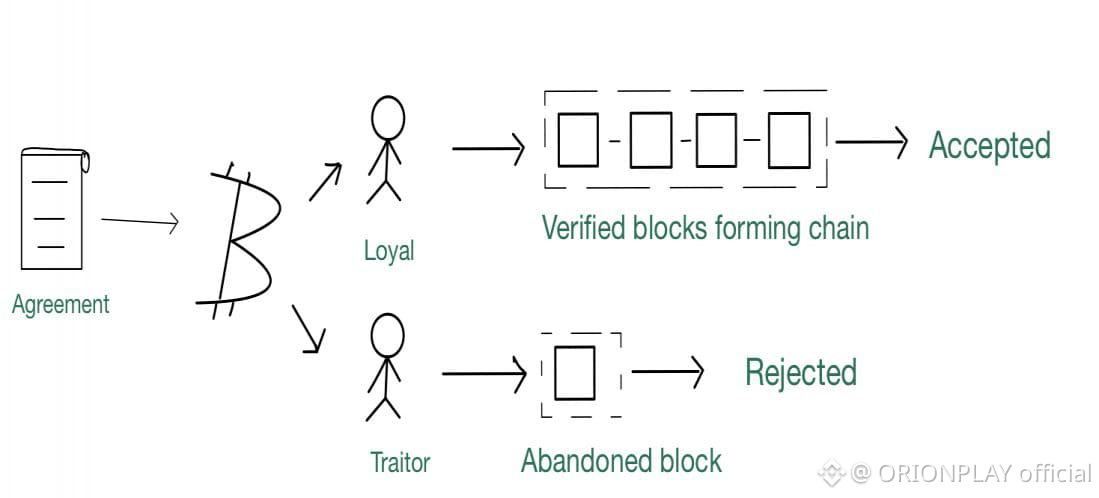
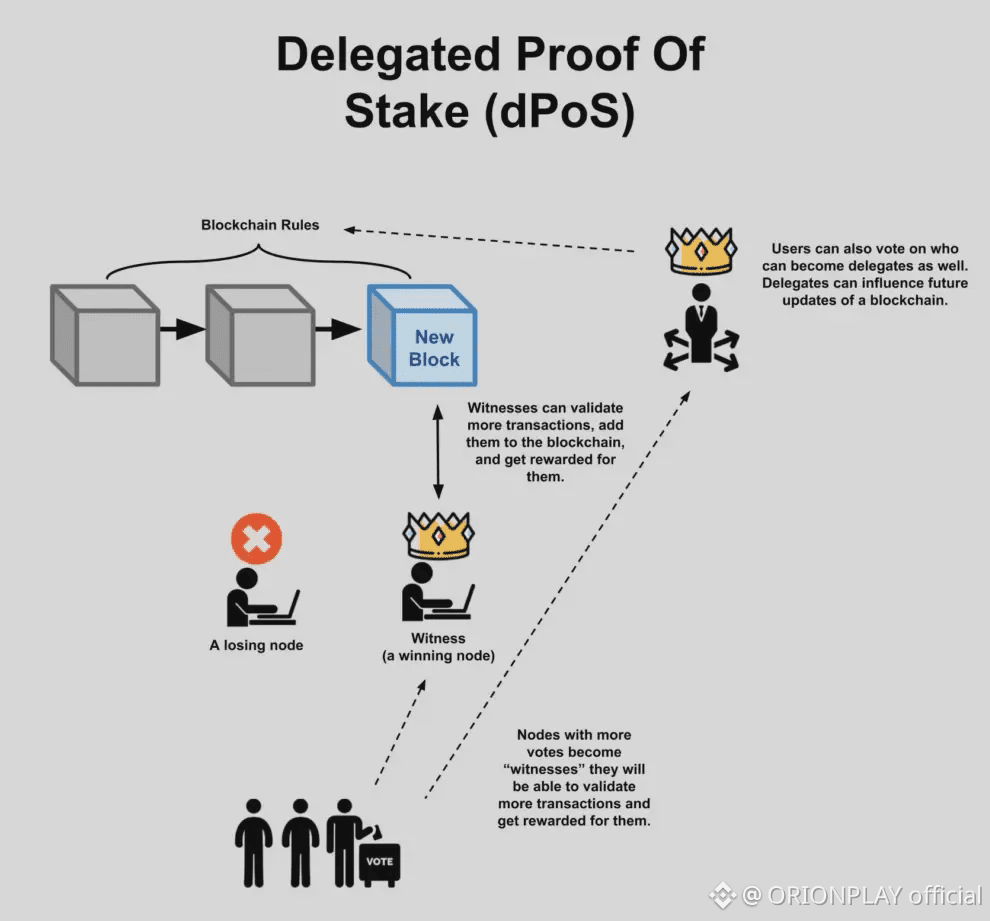
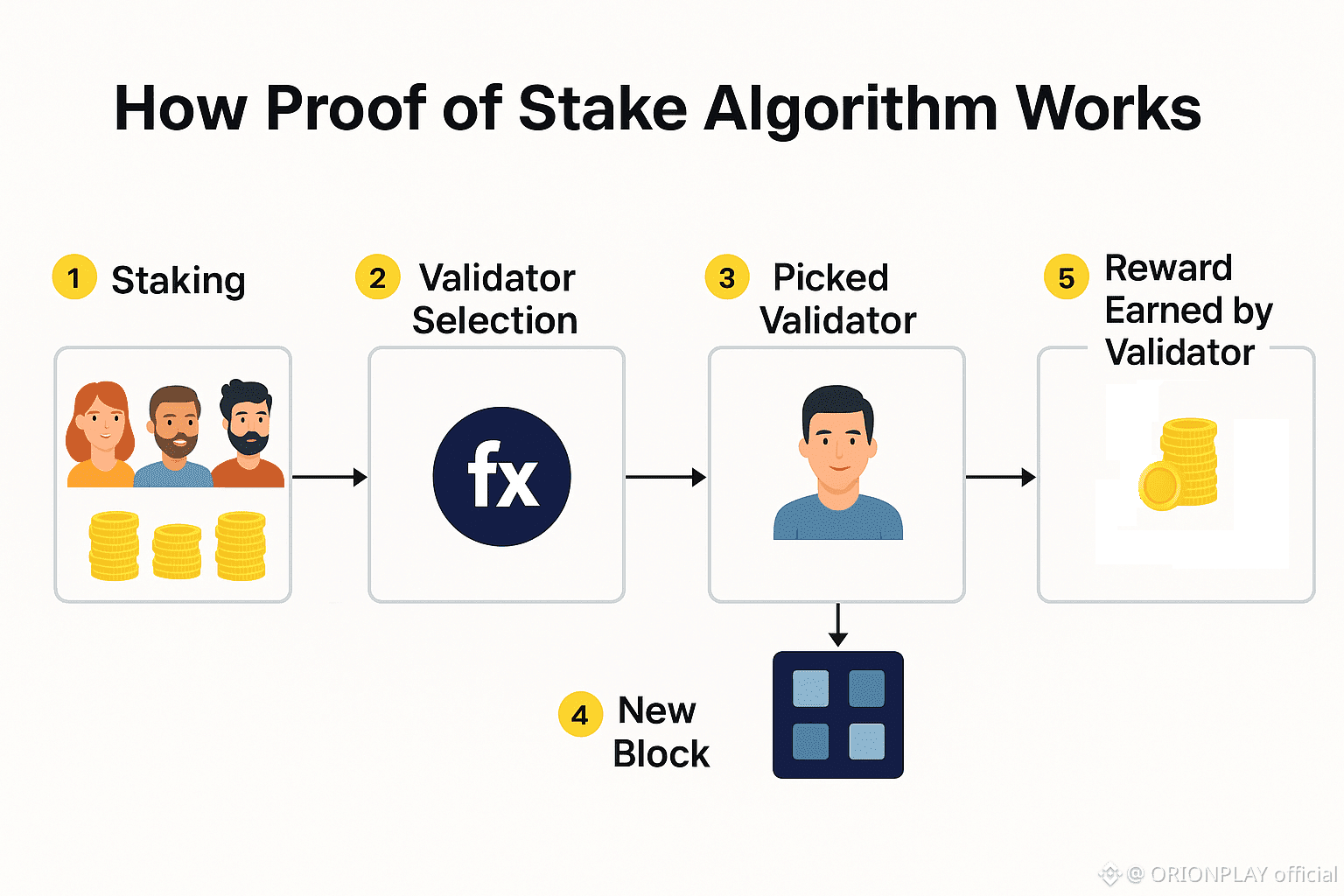
🧠 Segregated Byzantine Agreement (SBA)
Traditional PoS:
• Public validators
• Predictable leaders
• MEV risks
• Fork probabilities
SBA changes the rules.
🟣 Key architectural ideas:
• Validators split into Generators and Provisioners
• Leader selection happens privately
• Committees rotate deterministically
• Finality achieved in a single round
This structure drastically reduces:
• Network instability
• Leader manipulation
• Consensus gaming
🕶️ Proof-of-Blind Bid: Privacy at the Consensus Level
Most blockchains protect users…
but expose validators 😬
Dusk fixes that.
How Proof-of-Blind Bid works (simplified):
• Stake amount is committed, not revealed
• Zero-knowledge proof confirms eligibility
• Leader is selected probabilistically
• Identity stays hidden
🎯 Result:
• No stake spying
• No validator targeting
• No whale dominance
Consensus privacy is not optional here — it is architectural .
🔁 Transaction Architecture: Phoenix Model
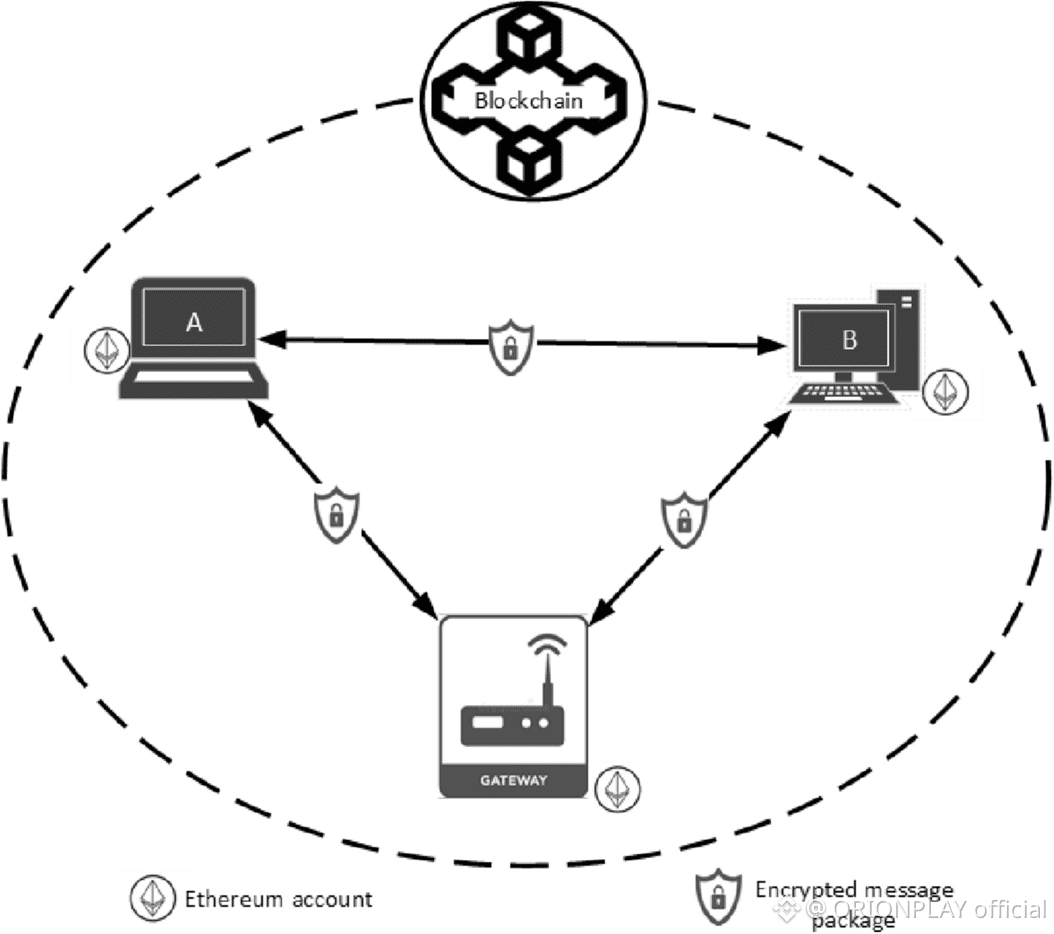
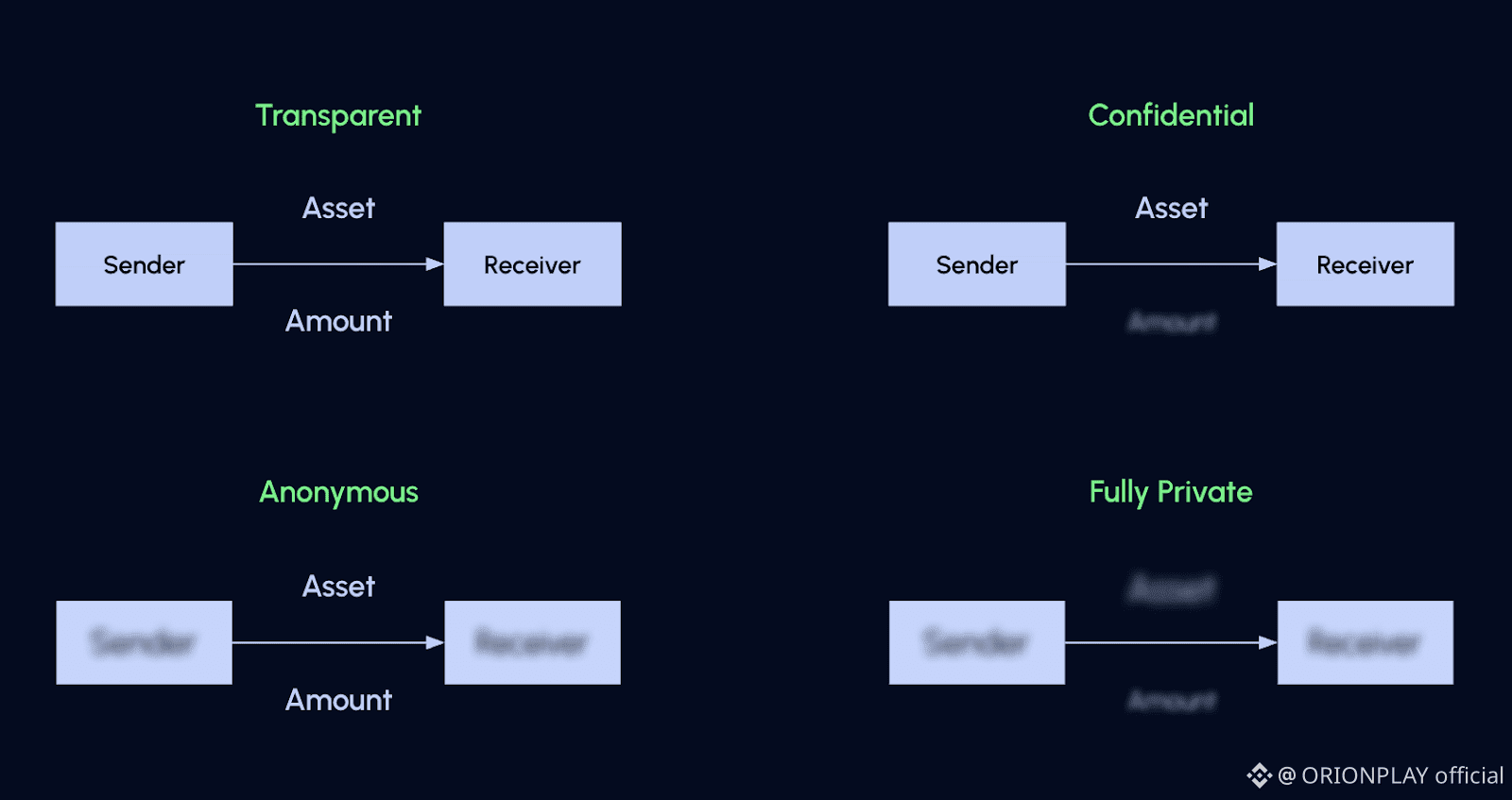
Why Phoenix Exists
Account-based models:
• Leak metadata
• Reveal balances
• Correlate users
Phoenix uses:
• UTXO-style notes
• Stealth addresses
• Nullifiers
• ZK proofs
Architectural advantages:
• Ever-growing anonymity set
• No address reuse
• No balance leakage
• Smart contract compatible
Phoenix was designed to survive long-term analytics attacks, not just short-term privacy threats.
🧾 Zedger Architecture: Privacy + Compliance
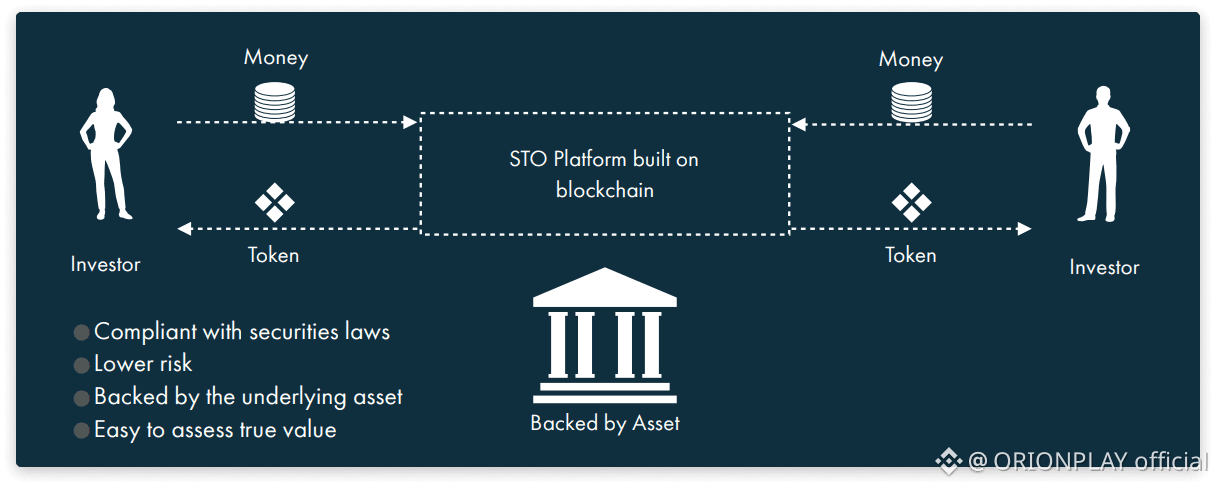
Zedger exists because:
👉 Real finance requires rules
Architectural components:
• One account per identity
• Whitelisted participation
• Private balance segments
• Auditable state roots
The magic lies in the Sparse Merkle-Segment Trie (SMST):
• Logs balance history privately
• Exposes only cryptographic roots
• Enables selective disclosure
This is not anti-regulation tech.
This is regulation-ready privacy.
🧠 Rusk VM: The Brain of the Network

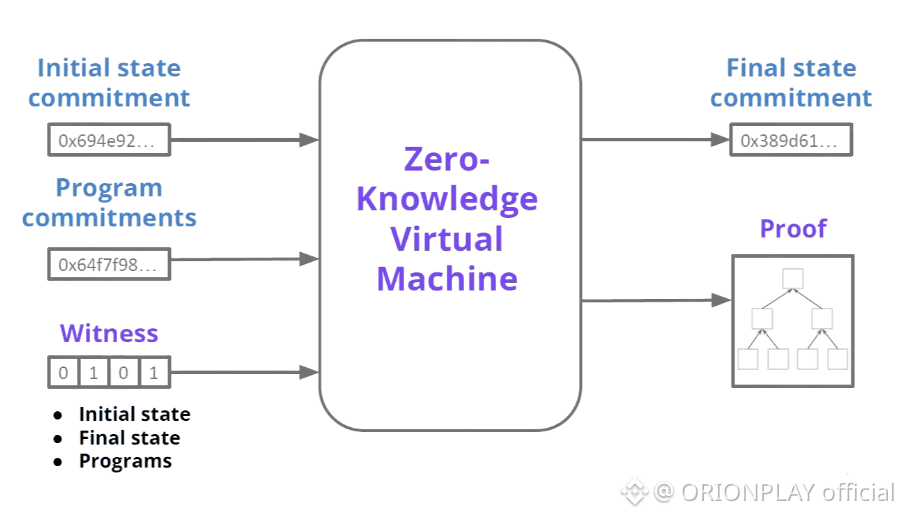
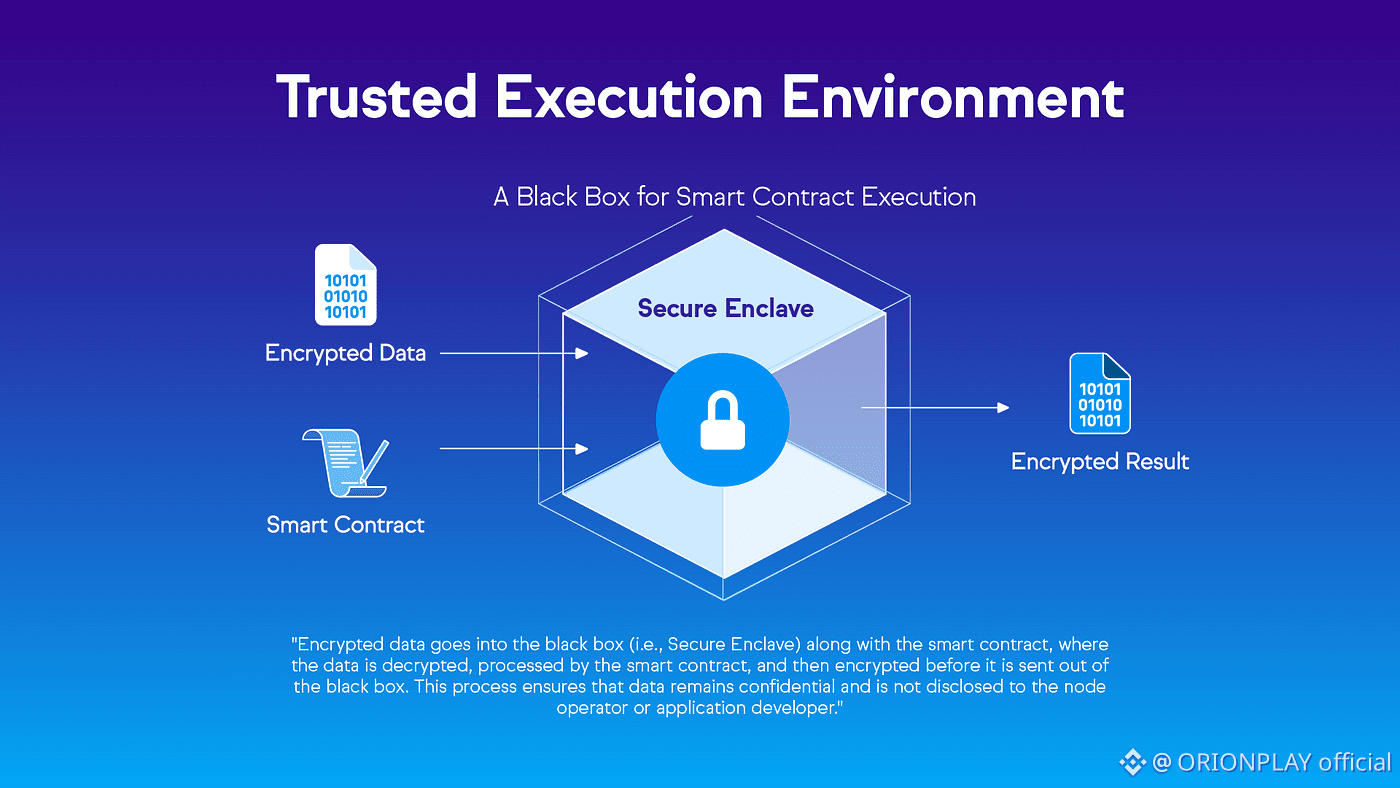
Rusk VM is not EVM with makeup 💄
It is a purpose-built execution engine.
Architectural strengths:
• WebAssembly-based
• Gas-bounded execution
• Native ZK verification
• Privacy-aware state access
Why this matters:
• Contracts can verify proofs directly
• No external ZK systems required
• Less complexity, more security
Smart contracts stop leaking secrets here.
🧬 Genesis Contracts: Built-In Trust Anchors
Instead of deploying core logic later, Dusk embeds it at genesis.
Native contracts include:
• DUSK Contract (asset logic)
• Bid Contract (validator entry)
• Stake Contract (slashing & security)
• Reward Contract (incentives)
This removes:
• Upgrade chaos
• Governance loopholes
• Hidden backdoors
Everything critical is architecturally enforced .
😄 Architecture Analogy (Because Brains Like Stories)
Think of Dusk Network as:
• SBA = traffic police 🚦
• Phoenix = tinted windows 🕶️
• Zedger = legal paperwork 📑
• Rusk VM = engine 🧠
Everything moves smoothly — and quietly.
🧠 Why This Architecture Ages Well
• Privacy baked into consensus
• Finality without energy waste
• Compliance without surveillance
• Smart contracts without leaks
This is not optimized for hype cycles.
This is optimized for decades.

