Hardware wallets are widely regarded as one of the safest ways to store cryptocurrency. By keeping private keys offline, these devices drastically reduce exposure to online threats like malware, phishing attacks, and remote hackers. But owning a hardware wallet is only part of the story—using it correctly is equally important.
This guide explains how hardware wallets work, why they’re effective, and the key habits you should adopt to protect your crypto.
What Is a Hardware Wallet?
A hardware wallet is a physical device designed to store your cryptocurrency private keys offline. Private keys are essential for authorizing transactions—anyone who controls them can access your funds. By keeping them isolated, hardware wallets prevent unauthorized access.
These wallets are also called cold wallets, contrasting with hot wallets that run on internet-connected devices like smartphones or computers. While hot wallets are convenient, they are more vulnerable to digital attacks.
Popular hardware wallet brands include Ledger and Trezor, both emphasizing secure key storage without sacrificing usability.

How a Hardware Wallet Works
Although hardware wallets stay offline, they still interact with computers or smartphones to process transactions:
You connect the wallet to a device via USB or wireless connection.
The device prepares a transaction but cannot sign it.
The unsigned transaction is sent to the wallet. You verify the details on the device screen.
The wallet signs the transaction internally and sends it back for broadcasting to the blockchain.
Key point: the private key never leaves the device—even if your connected computer is infected.
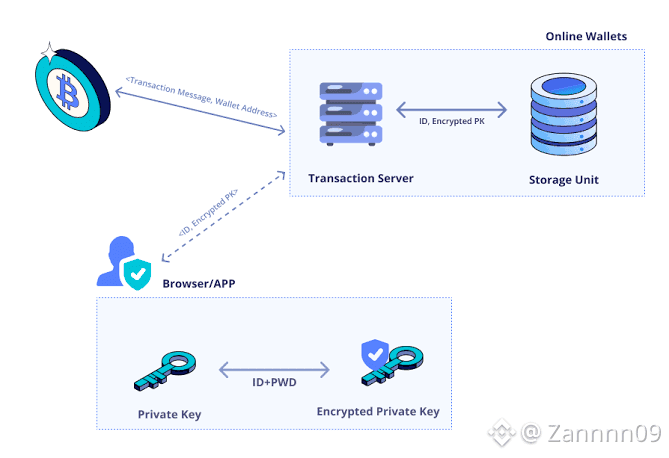
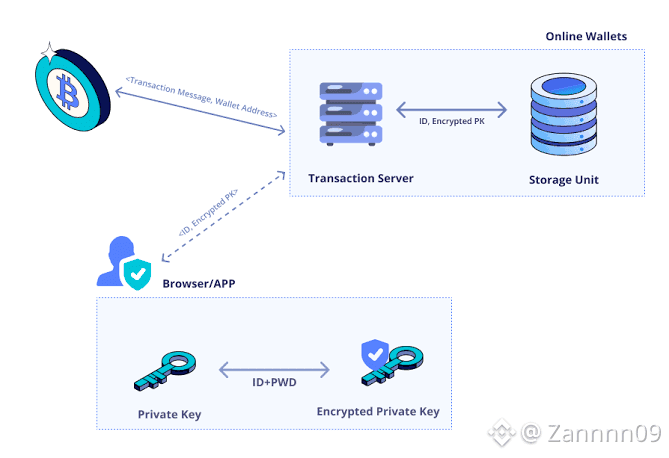
Private Keys vs. Recovery Phrases
Private keys: Long cryptographic numbers used to sign transactions. They stay inside the device.
Recovery phrases (seed phrases): 12–24 word human-readable backups that can restore all private keys in your wallet. Losing this phrase = losing access to your funds. Anyone with it can take full control.
Tip: Treat your recovery phrase like cash. Store it offline in a secure place.
10 Tips for Using a Hardware Wallet Securely
Buy Only From Trusted Sources
Purchase directly from the manufacturer or authorized retailers. Avoid second-hand devices.Keep Firmware Updated
Updates patch vulnerabilities and improve reliability. Ignoring them leaves your wallet exposed.Never Share Your Recovery Phrase
No one—including support agents—should ever ask for it.Store Recovery Phrases Offline
Avoid cloud storage, screenshots, or password managers. Use a physical, secure location.Use a Strong PIN
Choose something difficult to guess to protect the device from unauthorized access.Double-Check Addresses
Clipboard malware can swap copied addresses. Always verify on the hardware wallet screen.Verify Transactions on the Device
The device’s screen is the final authority, not your computer or phone.Protect the Device Physically
Treat it like cash or jewelry. Keep it secure and out of sight.Use a Passphrase Carefully
An optional passphrase creates a hidden wallet. Strong protection, but losing it means permanent loss.Connect Only to Trusted Computers
Avoid public or unfamiliar devices to reduce exposure further.
Benefits and Risks
Benefits:
Strong security from offline key storage
Reliable backups with recovery phrases
Portability and full control over your crypto
Risks:
Physical loss
Supply chain attacks
Phishing attempts
Forgotten PINs or recovery phrases
Firmware vulnerabilities
Most risks arise from user behavior, not device flaws.
Final Thoughts
Hardware wallets strike a powerful balance between security and usability. They allow you to interact with online systems while keeping your crypto safe—but responsibility matters.
If you:
Protect your recovery phrase
Verify transactions carefully
Keep firmware updated
Buy from reputable sources
…then your hardware wallet will remain one of the most effective tools for long-term cryptocurrency security.
Remember: a device is only as secure as the habits of the person using it.
#Binance #CryptoSecurity #HardwareWallets #ColdStorage #CryptoTips


