Introduction Of Dusk
@Dusk Launched in 2018, Dusk Network set out with a focused mission that immediately set it apart. Instead of chasing mass-market transparency or open-access experimentation, Dusk aimed squarely at regulated finance. The idea was simple but ambitious: build a layer-1 blockchain where privacy is baked in from the ground up while still meeting the demands of compliance, auditability, and institutional trust.
Over time, Dusk has grown from a research-driven initiative into a fully operational blockchain with its own consensus model, virtual machine, cryptographic stack, and a steadily maturing ecosystem. What follows is a detailed, practical overview of Dusk Network—where it came from, how it works, and why it occupies a distinct niche in the broader blockchain landscape.
1. Origins and Core Vision
Dusk Network was founded by a team experienced in cryptography, distributed systems, and financial infrastructure. Early on, they identified a problem most blockchains ignored. Financial institutions cannot operate on systems where every balance, counterparty, and transaction is permanently public.
In traditional finance, confidentiality and oversight coexist. Regulators get access when needed. Auditors verify records without broadcasting them. Dusk’s founding insight was that blockchains could replicate this model if privacy and compliance were designed together rather than treated as opposing forces.
The project’s long-term direction rests on three guiding principles:
Privacy as a default, not an optional feature
Compatibility with real-world regulation
Performance and security suitable for institutional use.
Every major technical decision flows from these ideas.
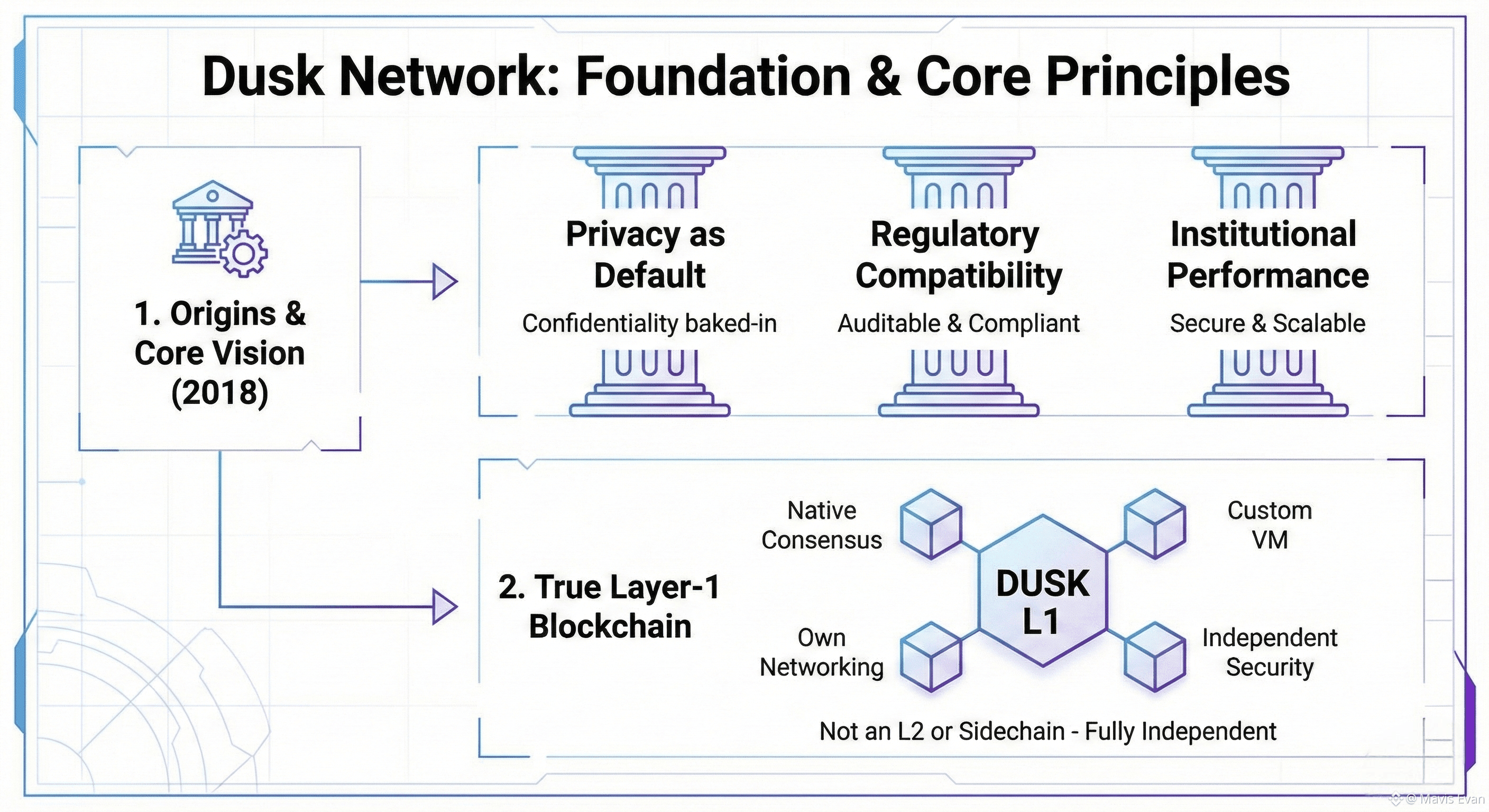
2. Why Dusk Is a True Layer-1
Dusk operates as a fully independent layer-1 blockchain. It does not inherit security or execution from Ethereum or any other network. Instead, it runs its own consensus mechanism, networking stack, execution environment, and cryptographic systems.
This independence matters. It allows Dusk to optimize for confidential finance without being constrained by assumptions built into general-purpose chains. Throughput, finality, privacy guarantees, and compliance features are all handled directly at the protocol level.
Some defining characteristics include:
A native consensus algorithm designed with privacy in mind
A custom virtual machine optimized for zero-knowledge computation
Built-in support for confidential assets
Deterministic finality suitable for financial settlement
3. A Modular Architecture
Rather than relying on a single, tightly coupled design, Dusk follows a modular architecture. Each layer of the protocol has a clear responsibility, making upgrades and audits easier over time.
At a high level, the system is composed of:
Consensus Layer for block production and finality
Execution Layer for smart contracts and transaction logic
Privacy Layer handling zero-knowledge proofs and encryption
Networking Layer enabling peer-to-peer communication
Application Layer where financial products and dApps live
This separation is especially important in regulated environments, where rules evolve and systems must adapt without sacrificing security.
4. Consensus via Succinct Attestation
Dusk uses a proprietary consensus mechanism known as Succinct Attestation. It differs from proof-of-work and traditional proof-of-stake models by focusing on efficiency, fast finality, and privacy awareness.
Key traits include:
Deterministic finality, essential for settlement
Low latency suitable for market activity
Energy efficiency without wasteful computation
Sybil resistance enforced through staking
Validators stake the DUSK token to participate. Honest behavior is rewarded, while misbehavior leads to slashing. The incentives are clear and aligned.
5. Zero-Knowledge Cryptography at the Center
Privacy on Dusk goes far beyond hiding transaction metadata. The network relies heavily on zero-knowledge cryptography, allowing participants to prove that rules were followed without revealing sensitive details.
This enables scenarios such as:
Proving ownership without exposing balances
Demonstrating regulatory compliance without revealing counterparties
Validating transactions without publishing full state data
Years of research have gone into balancing performance with strong cryptographic guarantees. The result is a system capable of supporting real financial workloads, not just theoretical use cases.
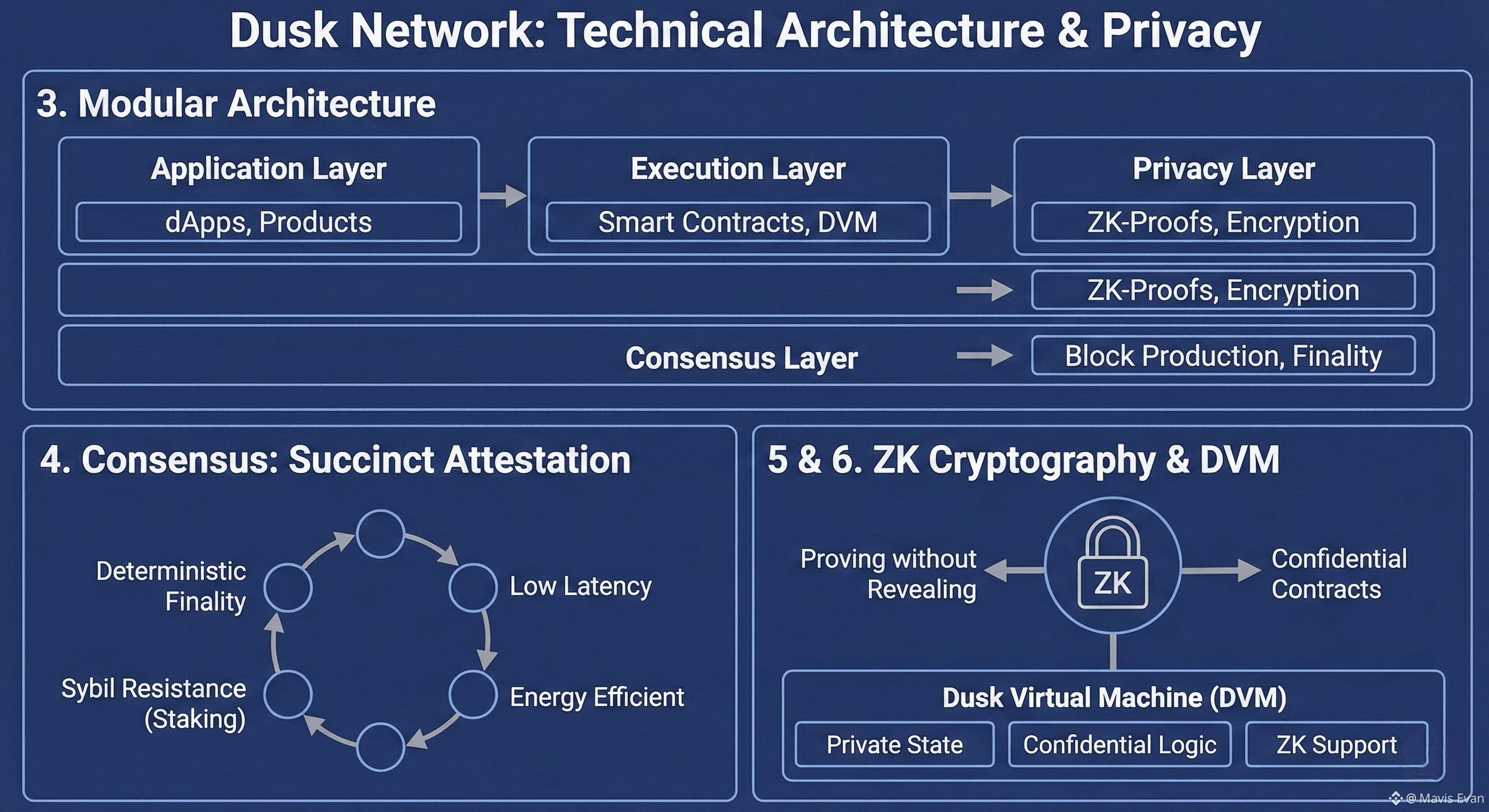
6. The Dusk Virtual Machine (DVM)
Smart contracts on Dusk run inside the Dusk Virtual Machine, a custom-built environment designed specifically for confidential computation.
Unlike the EVM, which assumes public state and transparent execution, the DVM supports:
Private contract state
Confidential business login
Native zero-knowledge proof generation and verification
Deterministic execution for financial reliability
This allows developers to encode complex financial rules while keeping sensitive data off the public ledger.
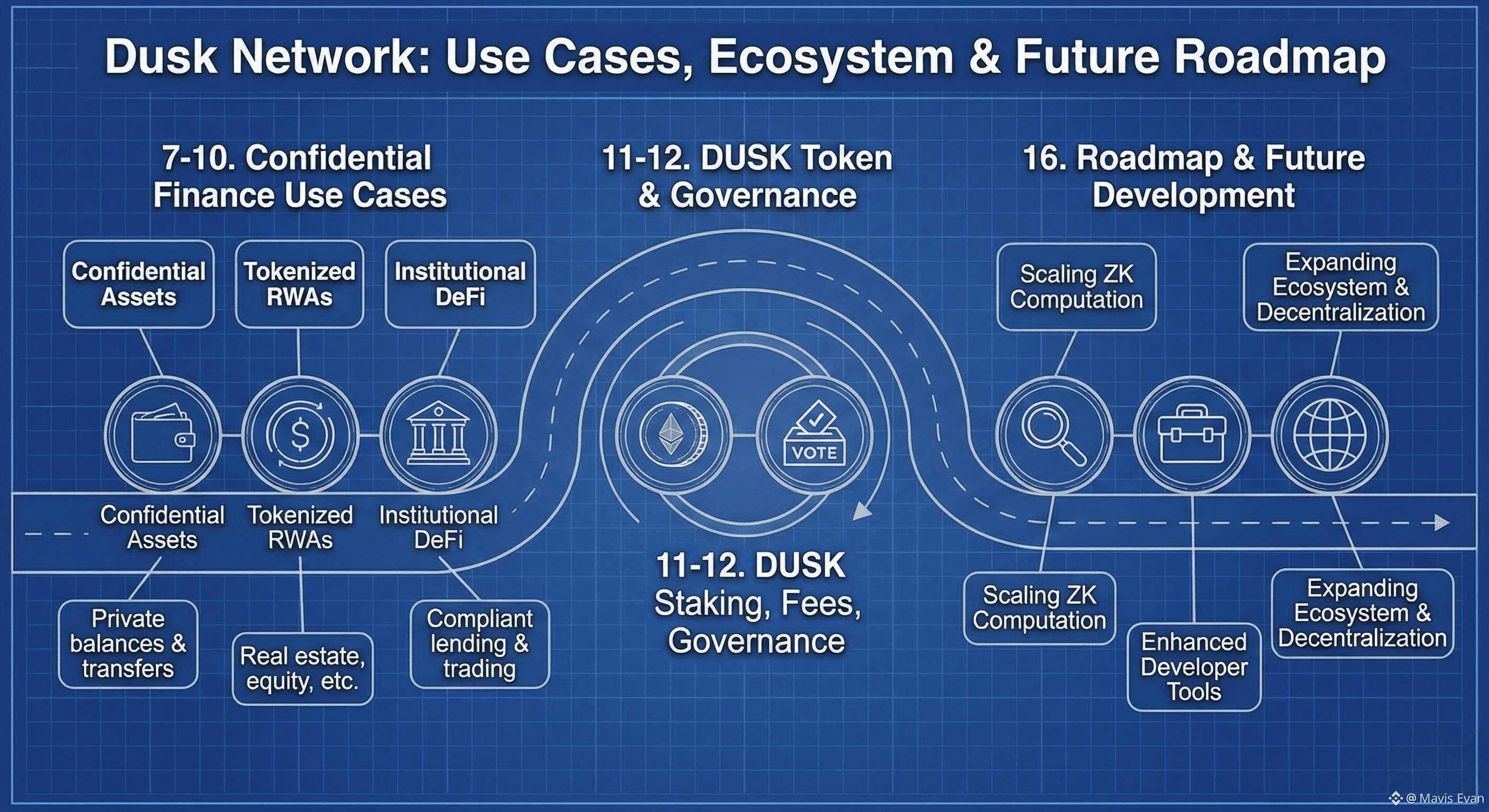
7. Confidential Assets and Token Standards
Dusk provides native support for confidential assets. These assets allow balances, transfers, and ownership details to remain private, while still being auditable by authorized parties.
This capability is essential for:
Tokenized securities
Private equity instruments
Bonds and structured products
Institutional investment funds
Issuers can embed compliance logic directly into the asset itself, including transfer restrictions, whitelisting, and jurisdiction-specific rules.
8. Compliance Without Compromise
One of Dusk’s most distinctive strengths is its approach to regulation. Rather than trying to sidestep it, the protocol is designed to work with existing legal frameworks.
Notable compliance features include:
Selective disclosure for regulators and auditors
Support for identity, KYC, and AML systems
On-chain enforcement of ownership and transfer rules
Privacy-preserving audit trails
This makes Dusk usable for institutions that cannot legally operate on fully transparent blockchains.
9. Tokenized Real-World Assets
Tokenization is rapidly becoming one of blockchain’s most practical use cases, and Dusk is built with this in mind.
Assets suitable for tokenization on Dusk include:
Equity and debt instruments
Real estate shares
Funds and ETFs
Commodities
Structured financial products
Privacy ensures that investor information, pricing data, and allocations remain confidential while still benefiting from blockchain settlement.
10. Institutional-Grade DeFi
Most DeFi today is optimized for retail users and radical transparency. Dusk enables a different model: compliant DeFi.
Potential applications include:
Private lending markets
Confidential automated market makert
Institutional staking products
Regulated derivatives
This opens decentralized finance to banks, asset managers, and funds that previously could not participate.
11. The Role of the DUSK Token
The DUSK token underpins the network’s economics and security.
Its main functions are:
Staking for validator participation
Securing the network through economic incentives
Paying transaction fees
Participating in governance
The token model is structured to support long-term sustainability rather than short-term speculation.
12. Governance Structure
Dusk uses on-chain governance, allowing token holders to vote on protocol-level decisions.
Governance covers areas such as:
Network upgrades
Economic parameters
Validator requirements
Ecosystem funding
This approach balances community participation with the stability institutions expect.
13. Ecosystem and Strategic Focus
Rather than chasing consumer hype, Dusk has concentrated on building relationships within the financial sector.
The ecosystem includes:
Infrastructure providers
Financial institutions
Tokenization platforms
Compliance and identity services
Depth, reliability, and long-term alignment matter more than rapid expansion.
14. Developer Experience
Developer tooling is treated as a first-class concern.
Support includes:
SDKs and APIs
Documentation tailored to financial use cases
Testing environments for confidential contracts
A strong emphasis on protocol stability
This lowers the barrier for teams building serious financial applications.
15. Security and Verification
Security is non-negotiable in financial systems. Dusk invests heavily in:
Formal verification of cryptographic components
External audits of core code
Conservative and carefully reviewed upgrades
These measures reduce systemic risk and build institutional trust.
16. Roadmap and Future Development
Ongoing development remains tightly aligned with the original mission. Current priorities include:
Scaling confidential computation
Enhancing developer tooling
Expanding RWA and DeFi primitives
Strengthening decentralization and governance
Trends come and go. Dusk stays focused.
17. A Unique Position in the Market
Dusk does not compete with meme-driven ecosystems or consumer-focused chains. Its target market is far larger and more demanding: global financial assets that require privacy, compliance, and reliability.
That niche is measured in trillions, not hype cycles.
Conclusion
Dusk Network takes a disciplined, intentional approach to blockchain design. By prioritizing privacy, regulatory compatibility, and institutional needs from the outset, it fills a gap most platforms ignore.
As tokenization and regulated DeFi continue to gain momentum, Dusk is well positioned to serve as foundational infrastructure. Instead of forcing institutions to adapt to blockchain limitations, it adapts blockchain to the realities of modern finance.

