At 2:32 a.m., an email hits the inbox. Not a “hey, quick question” email. The kind with sharp edges. Audit request. “Show us your backup proof. Show us who held the data. Show us when.” If you’ve ever sat near an ops team, you know the weird part: most firms do have backups. Plenty of them. The fear is the gap between “we copied it” and “we can prove it.” That gap gets loud during a breach, a lawsuit, a regulator check, or a vendor fight. Someone asks, “Where was the file last month?” and the room goes quiet for a second. Because cloud logs can be changed. Vendor dashboards can go down. And when your whole safety plan lives inside one company’s tools… you start to feel the lock-in. Not the good kind. The trap kind.
That’s the enterprise angle that makes Walrus (WAL) interesting. Not as a hype thing. More like a boring, serious tool… that shows up when things go wrong.
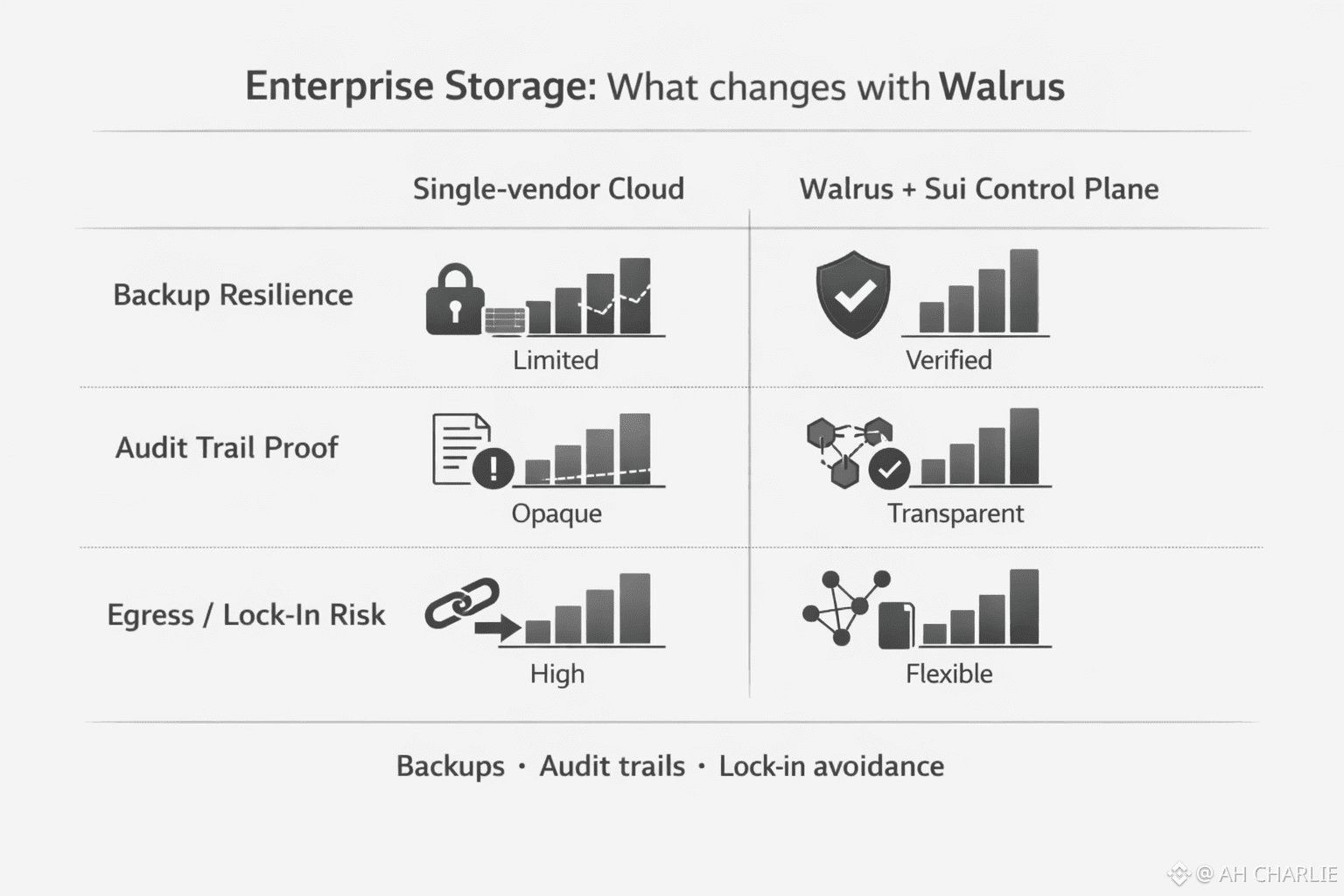
Walrus is built for “blob storage.” That’s just a fancy way to say big, messy files. Images. Videos. PDFs. Data dumps. Stuff that does not fit nicely inside a database row. Walrus stores that kind of data across many storage nodes, but it does it with a trick called erasure coding. Simple meaning: instead of making full copies everywhere (wasteful), it breaks a file into many coded pieces. Like tearing a map into parts… but in a way where you can still rebuild the map even if some parts go missing. Walrus’s design uses an encoding method (often described as “Red Stuff”) and spreads “slivers” of the file across nodes, so the system can stay up even if some nodes fail or act bad. Now comes the part enterprises actually care about: the receipt. Walrus uses Sui as a “control plane,” which is basically the ledger that tracks the rules and records the proof. When a file is stored, Walrus can publish a Proof of Availability (PoA) onchain. That sounds heavy, but the idea is light: a public, verifiable record that a quorum of nodes took custody of the data for a set time. In plain terms… it’s harder to hand-wave. You can point to a record that others can verify, not just a screenshot from a vendor portal. That’s what “audit trail” should feel like. Solid. Boring. Hard to fake. And this is where “backup” stops being a dusty checkbox and turns into a living process. Think of a real incident. A ransomware scare. The company restores files. Great. Then the next question is brutal: “How do we know the restored data is the right data? And how do we prove we didn’t alter it?” Walrus leans into verifiable custody. Not perfect truth for everything, but a stronger chain than “trust us.” Also, vendor lock-in starts to crack. In the normal world, lock-in is sneaky. Your data is “portable,” sure… after you pay the egress fee, export it in their format, and rebuild your whole pipeline. Walrus is a protocol. Data is stored across a network of nodes, coordinated by onchain logic, rather than one provider’s private system. That doesn’t remove every switching cost in life, but it changes the shape of the risk. If one operator disappears, the system is still designed to recover the file from remaining pieces. You’re less trapped by a single door. One more honest note, because enterprises don’t get to be naive: decentralized storage does not magically solve policy. If the data is sensitive, you still encrypt it. You still manage keys. You still decide who can access what. Walrus can give you a stronger “proof” layer and a more open storage base, but it won’t do your governance paperwork for you. That part is on the humans. So if you zoom out, Walrus (WAL) is not just “storage.” It’s a different stance: backups you can verify, audit trails that don’t live inside one vendor’s wall, and a path where switching is at least possible without begging a provider for mercy. Not financial advice - just an infrastructure lens on why the enterprise crowd even cares. And yeah… the next time that 2:32 a.m. email lands, the real flex isn’t “we have backups.” It’s “here’s the proof, and you can check it yourself.”
@Walrus 🦭/acc #Walrus $WAL #Web3

