Privacy Didn’t Die — It Just Grew Up
For years, privacy in crypto behaved like a rebellious teenager. Loud. Uncompromising. Proudly allergic to rules.
That approach worked — until the real world knocked on the door.
Regulators arrived. Institutions followed. Suddenly, the question changed.
Not “Can privacy exist?”
But “Can privacy survive reality?”
This is where Dusk Foundation quietly stepped away from the noise and chose a harder path:
building privacy that regulators don’t need to fear.
Not watered-down privacy.
Not fake compliance.
But a system where confidentiality and accountability coexist without cancelling each other out.
That choice reshaped everything.
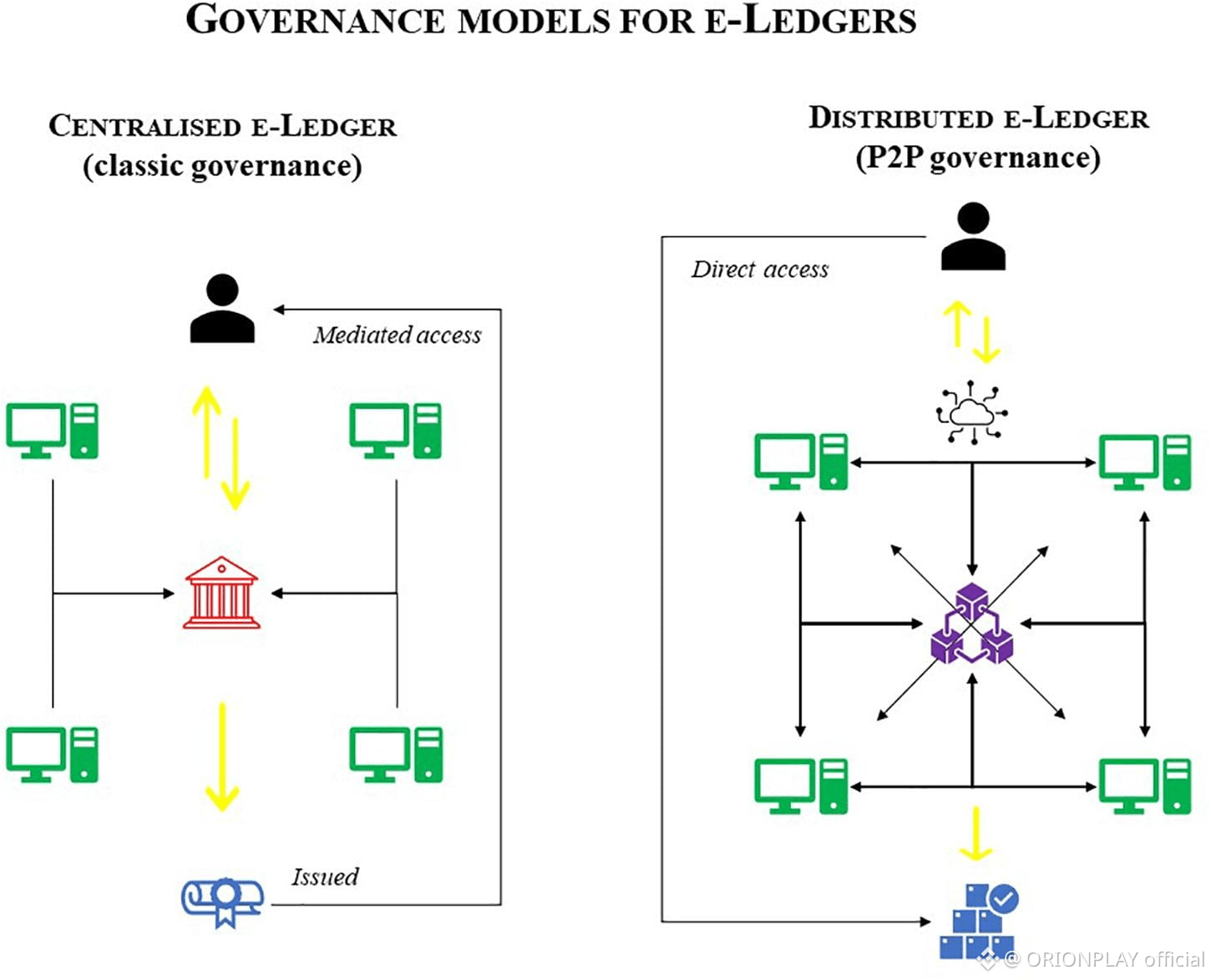
1. The Problem No One Wanted to Solve
Most privacy chains focused on one thing: hiding everything.
Transactions. Participants. History. Sometimes even logic itself.
That approach creates three unavoidable problems:
Regulatory rejection
Institutional paralysis
Developer isolation
Privacy became powerful — but unusable at scale.
Dusk took a different starting point:
What if privacy isn’t about hiding from the system, but working safely inside it?
That single reframing changed the architecture completely.
2. Privacy as a Selective Tool, Not a Blanket
Dusk does not treat privacy as an “all or nothing” feature.
Instead, it introduces selective disclosure as a first-class principle.
This matters because real-world finance works on conditions:
Auditors need visibility
Regulators need proofs
Users need confidentiality
Dusk’s model allows:
Transaction data to remain private
While cryptographic proofs confirm validity
Without exposing sensitive details
Privacy becomes programmable, not ideological.
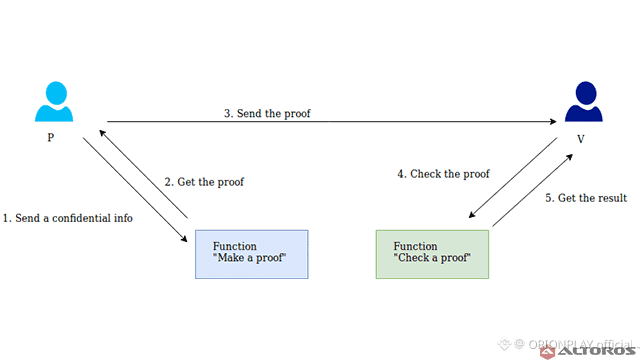
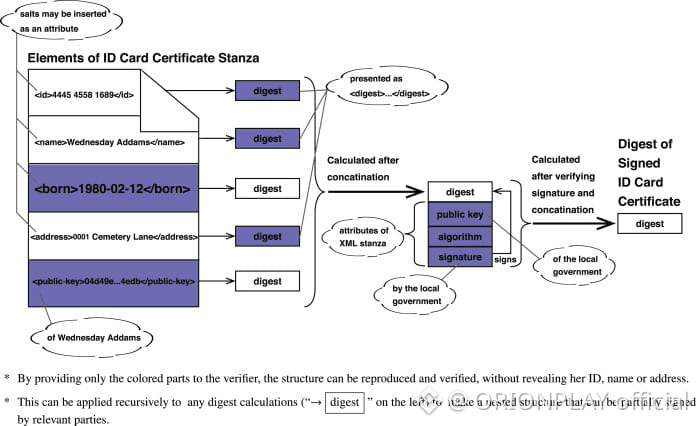
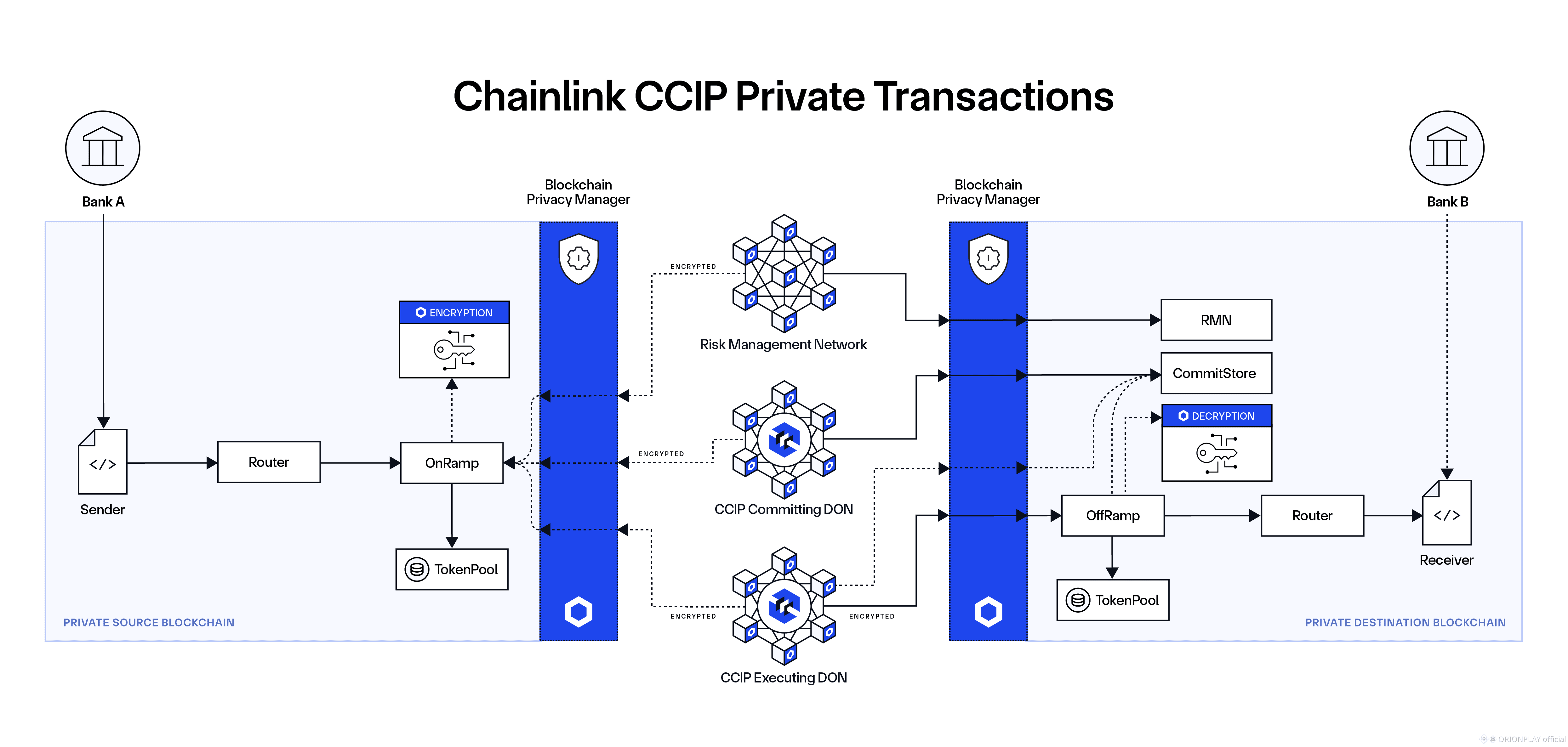
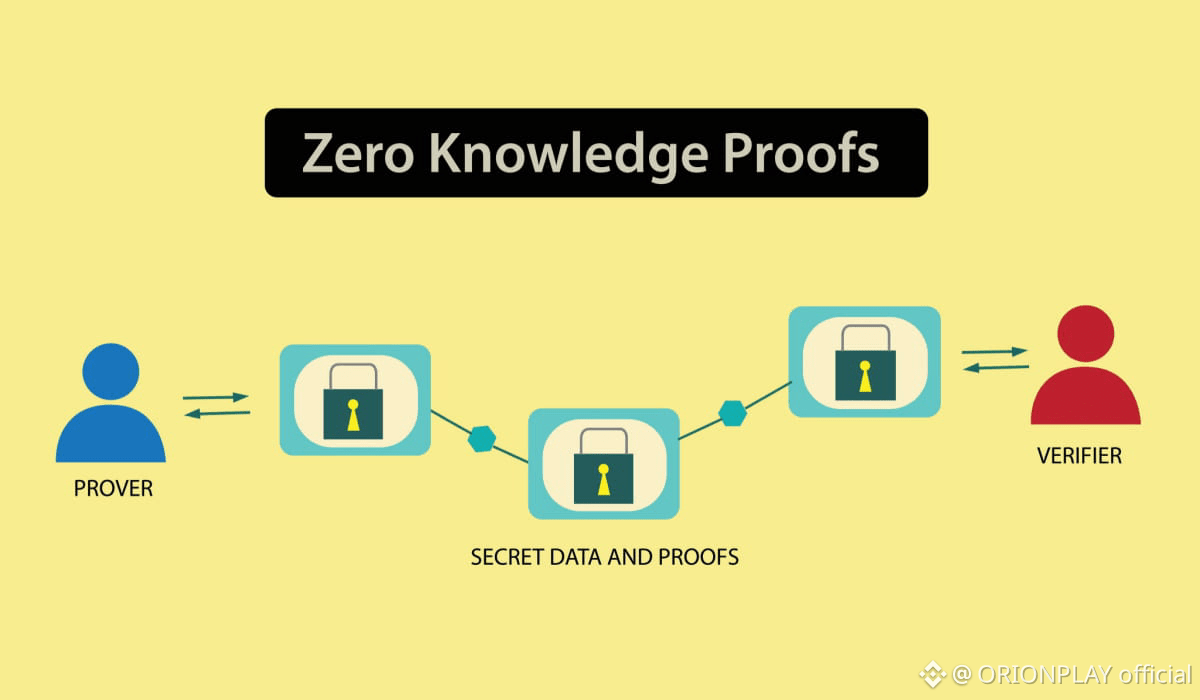
3. Zero-Knowledge Done the Hard Way
Many projects use zero-knowledge proofs.
Fewer projects design around them.
Dusk belongs to the second category.
Instead of bolting ZK on top of an existing chain, Dusk builds execution, settlement, and validation around privacy-preserving logic.
The result:
Confidential smart contracts
Private asset issuance
Verifiable execution without data leakage
This is not marketing ZK.
This is operational ZK.
And it’s expensive — computationally, architecturally, intellectually.
Which is exactly why few attempt it.
4. Why Institutions Quietly Care About Dusk
Banks and funds do not fear transparency.
They fear uncontrolled transparency.
Public blockchains expose:
Trade strategies
Treasury movements
Client relationships
Dusk offers something rare:
On-chain execution
Off-chain confidentiality
On-demand auditability
This triad is what makes Dusk relevant to:
Tokenized securities
Regulated assets
Compliance-heavy jurisdictions
Not flashy.
But deeply practical.
5. The Subtle Genius: Compliance Without Surveillance
Here’s the uncomfortable truth most projects avoid:
Total anonymity does not scale into regulated economies.
Dusk doesn’t fight this reality.
It cryptographically negotiates with it.
Instead of exposing users:
Dusk exposes proofs
Not identities
Not transaction internals
This flips the compliance model:
Trust moves from institutions → mathematics
Oversight becomes verifiable, not invasive
Privacy survives — not by hiding — but by proving correctness without confession.
6. Why This Approach Is Hard to Copy
Dusk’s design is not a feature set.
It’s a philosophy baked into protocol layers.
To replicate it, a chain must:
Redesign execution environments
Rebuild smart contract assumptions
Accept higher complexity
Most chains won’t.
Because complexity doesn’t trend on social media.
But complexity is exactly what institutions pay for.
Continuing exactly from where Article 1 – Part 1 paused.
Same tone, same depth, no repetition, and images placed naturally between sections.
When Privacy Starts Doing Real Work
7. Confidential Smart Contracts: Where Theory Meets Reality
Smart contracts are usually loud by design.
Every variable, every state change, every interaction — visible forever.
That transparency is useful.
But it’s also a deal-breaker for anything serious.
Dusk’s confidential smart contracts flip the model:
Logic executes on-chain
Sensitive inputs remain shielded
Outcomes are provably correct
Yet details stay private
This matters because real contracts don’t live in a vacuum.
They contain:
Pricing formulas
Legal thresholds
Counterparty constraints
Business logic competitors should never see
Dusk allows contracts to behave like legal agreements, not public spreadsheets.
8. Tokenization Without Broadcasting the Balance Sheet
Tokenization is often sold as innovation.
In practice, it usually means turning private assets into public liabilities.
That’s the paradox.
Institutions want:
On-chain efficiency
Programmatic settlement
Automated compliance
They do not want:
Public exposure of holdings
Real-time portfolio tracking by strangers
Competitors reading market intent
Dusk’s architecture allows asset tokenization where:
Ownership is provable
Transfers are valid
Compliance rules are enforced
Yet holdings remain confidential
Tokenization becomes operational, not performative.
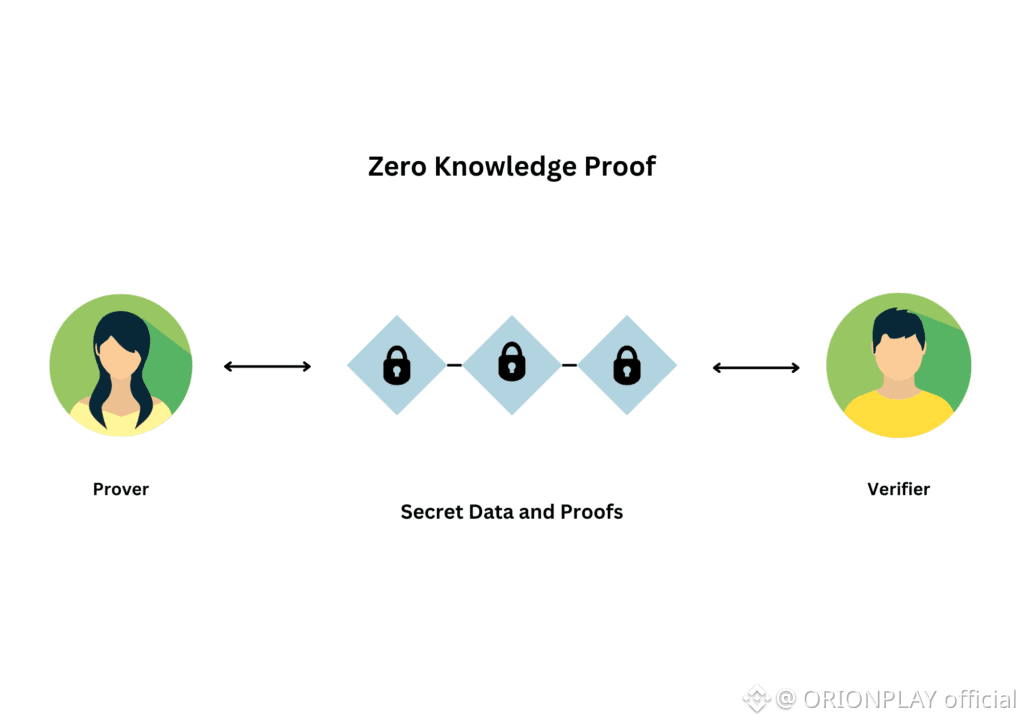
9. The Quiet Role of Cryptographic Accountability
Here’s where Dusk gets misunderstood.
Privacy is not used to avoid responsibility.
It’s used to change how responsibility is proven.
Instead of:
“Trust this institution”
“Believe this report”
“Accept this disclosure”
Dusk enables:
Mathematical proofs of correctness
Verifiable constraints
Deterministic enforcement
This replaces trust with verification — without public exposure.
In regulated environments, that’s not rebellious.
That’s efficient.
10. Why Slow Development Is a Feature, Not a Flaw
Fast chains win headlines.
Slow chains win court cases.
Dusk’s development pace often looks conservative — until you understand the cost of mistakes.
Privacy systems:
Cannot be patched casually
Cannot afford logic leaks
Cannot “move fast and break things”
Every cryptographic assumption becomes a liability if wrong.
Dusk’s methodical approach signals something important:
This protocol expects to be used where mistakes are not forgiven.
That expectation shapes everything.
11. Where Most Privacy Chains Fail (And Why Dusk Hasn’t)
Most privacy-focused networks stumble in one of three places:
Total opacity → regulatory exclusion
Partial privacy → weak protection
Complex UX → zero adoption
Dusk avoids these traps by:
Designing privacy as modular
Treating compliance as a cryptographic problem
Targeting institutional-grade use cases first
It’s not trying to replace every blockchain.
It’s trying to be indispensable in specific ones.
That restraint is rare — and intentional.
12. The Strategic Bet Few Are Talking About
Dusk is betting on a future where:
Regulation increases
Tokenization expands
Privacy laws tighten
Transparency becomes selective
In that future:
Fully public chains leak too much
Fully private chains isolate themselves
Hybrid, proof-based systems dominate
Dusk is already built for that world.
Not hypothetically.
Architecturally.
Closing Reflection (Not a Conclusion)
Privacy in crypto started as resistance.
Dusk treats it as infrastructure.
Not loud.
Not flashy.
But extremely hard to replace once embedded.
That’s how real systems win.

