One of the hardest problems in blockchain design is not security or privacy. It is liveness—the ability of the network to keep moving forward under imperfect conditions. Most protocols solve this by relaxing guarantees. They allow forks, reorgs, or probabilistic confirmation in exchange for speed. Dusk Network takes a more deliberate route. It chooses bounded progress over optimistic acceleration.
The white paper makes a clear assumption: the network is synchronous within known limits. Messages may be delayed, but only up to a defined bound. This assumption is not hidden. It is explicit, and the protocol is built tightly around it. Dusk does not try to operate correctly under every imaginable network condition. It focuses on operating predictably under realistic ones.
This choice has structural consequences.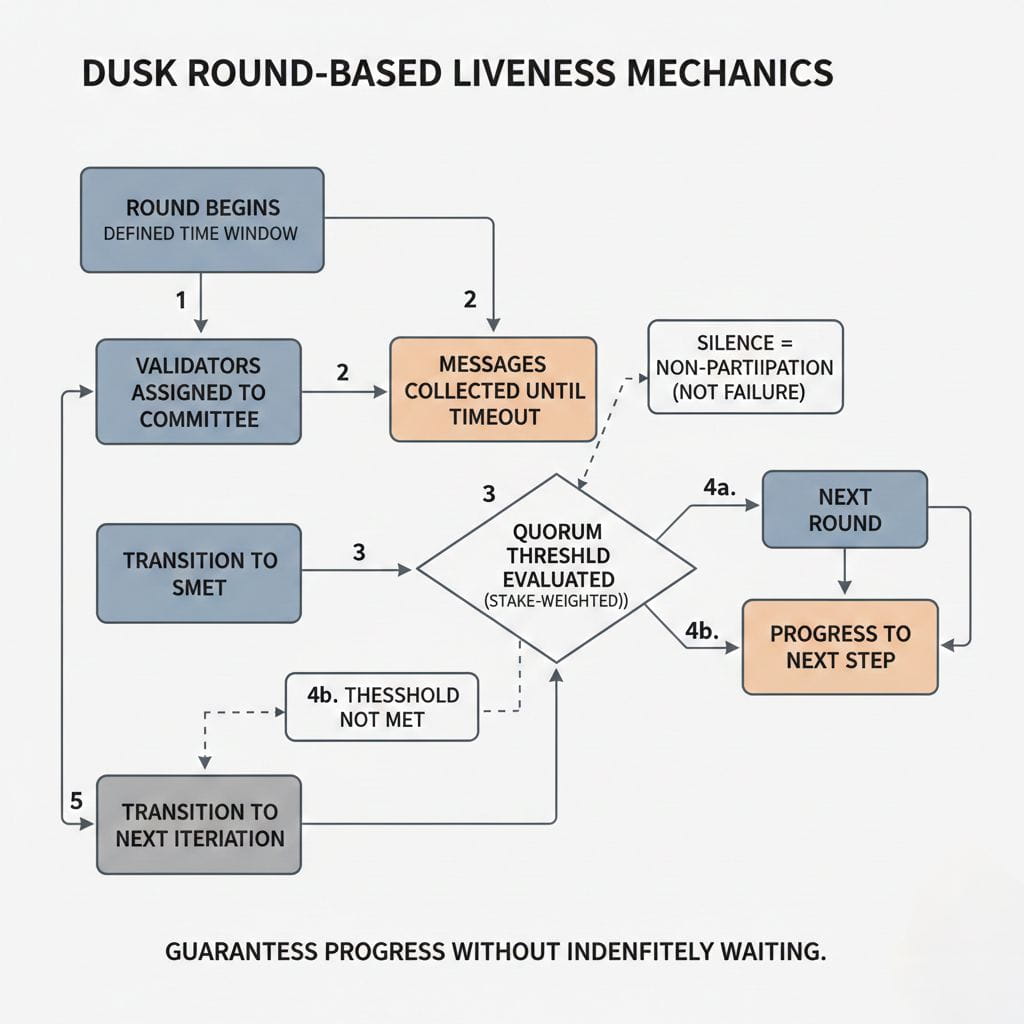
In Dusk, time is divided into rounds and steps, each with a clearly defined duration. Progress is not driven by who shouts first or who has the fastest connection. It is driven by timers and thresholds. If something does not arrive in time, the protocol does not guess. It advances according to rules.
This is a subtle but important difference. Many systems conflate liveness with aggressiveness. They try to move as fast as possible and then repair damage later. Dusk avoids that entirely. It defines how long the network will wait, what constitutes enough participation, and when it is safe to move on—even if not everyone responded.
The key insight here is that waiting is a feature, not a failure.
Dusk’s consensus design allows for partial participation without stalling the system. Validators are selected into committees for specific steps. If some fail to respond, the protocol does not pause indefinitely. It checks whether a quorum threshold has been met. If it has, progress continues. If it has not, the protocol transitions to the next step or iteration.
This ensures that a small number of slow or faulty participants cannot block the entire network.
Importantly, this is not done by lowering standards. Safety thresholds remain strict. What changes is how the protocol reacts to absence. Silence is treated as non-participation, not as a signal to halt.
Timing and voting logic must be carefully coordinated in this method. The white paper specifies precise benchmarks for advancement. Stake-weighted participation, not the total number of nodes, determines these thresholds. This guarantees that decisions about liveness are based on economic considerations rather than just technical ones.
Another often overlooked aspect is parallelism. Dusk runs agreement logic concurrently with other phases of consensus. The system does not wait for one phase to fully complete before preparing for the next. This overlap allows the network to absorb delays without losing momentum.
But this parallelism is tightly controlled. It does not create race conditions or ambiguity. Each phase knows exactly what inputs it depends on and what outputs it produces. Progress is pipelined, not improvised.
This design contrasts sharply with protocols that rely on leader optimism. In those systems, if a leader fails or stalls, the network scrambles to recover. In Dusk, leadership is temporary and replaceable within the same round structure. Progress does not hinge on any single actor behaving well.
Through incentives, both validators and generators benefit financially just as validators and generators are encouraged to participate immediately, as the protocol does not necessitate an immediate response to the protocol in order for it to remain functional. A person who participates in the protocol will earn rewards; however, a person who does not participate does not halt the functionality of the protocol.
This distinction matters for long-term reliability. Real networks experience outages, maintenance windows, and unpredictable latency. A protocol that assumes constant responsiveness eventually breaks. Dusk assumes bounded imperfection and designs around it.
There is also a security implication. Many attacks aim not to break correctness, but to delay progress. By forcing honest nodes to wait indefinitely, attackers can create economic pressure or user frustration. Dusk limits the effectiveness of such attacks by making delay costly and ineffective beyond defined bounds.
From an application perspective, this results in a predictable execution environment. Developers know how long it takes for a transaction to be finalized under normal conditions. Users know when results can be relied upon. There is no need to “wait a bit longer just in case.”
The DUSK token interacts with this model indirectly but meaningfully. Because participation is time-scoped and rewarded per round, there is a natural incentive to maintain availability. But because progress does not depend on unanimity, the system remains robust even when incentives fail locally.
What stands out is restraint. Dusk does not chase theoretical maximum throughput or minimum latency. It optimizes for steady forward motion under known constraints. That makes the system less exciting in benchmarks—but more reliable in practice.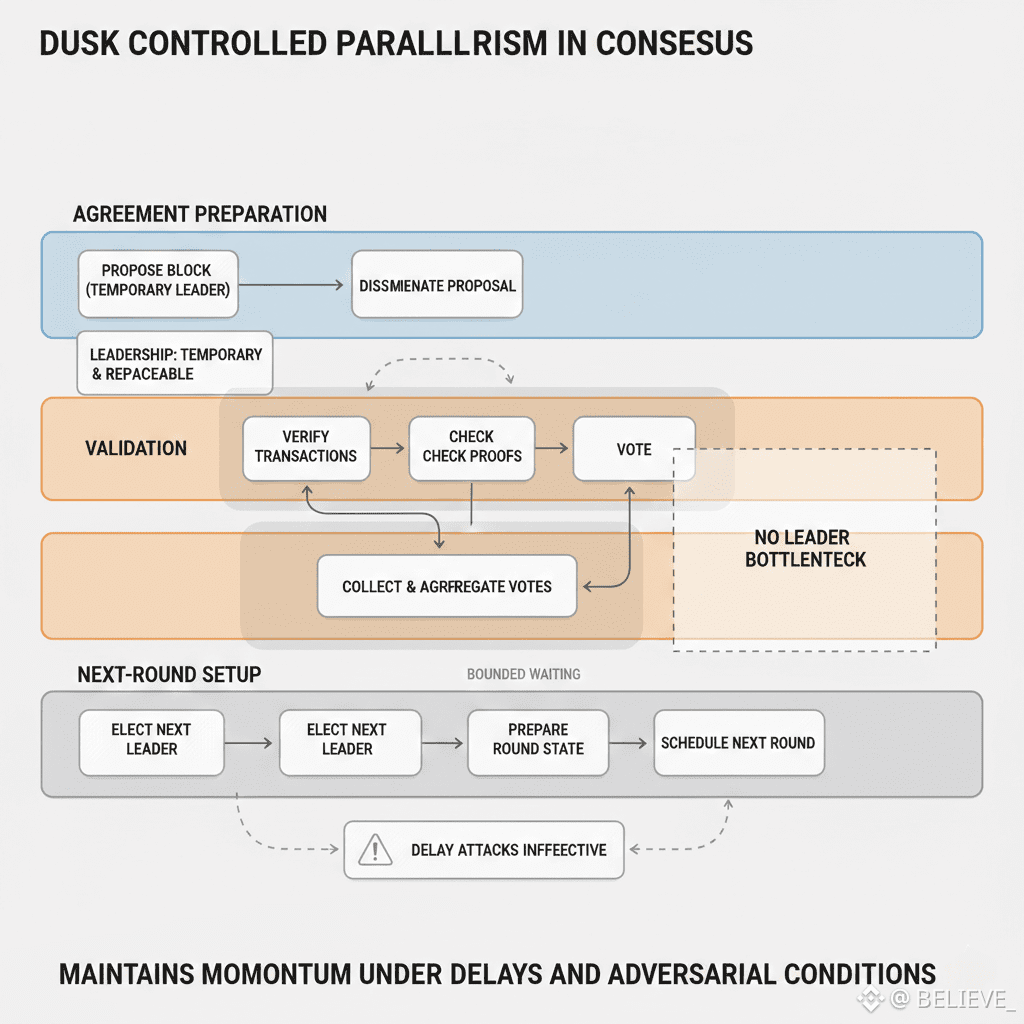
In conclusion, Dusk Network treats liveness as a coordination problem, not a speed contest. By defining how long to wait, how much participation is enough, and how to proceed in the face of absence, the protocol ensures that the network keeps moving without sacrificing safety.
Progress in Dusk is not accidental.
It is engineered—step by step, round by round, within boundaries the system understands.
That discipline is what allows Dusk to function as infrastructure rather than experiment, especially in environments where predictability matters more than raw speed.

