Most blockchain discussions focus on consensus, execution, or cryptography. Very few examine how messages actually move through the network—and that omission is costly. In Dusk Network, communication is not treated as a background utility. It is treated as part of the security model itself.
The Dusk white paper makes a deliberate choice to formalize message propagation instead of assuming it “just works.” This matters because consensus safety and liveness do not fail only due to bad cryptography. They fail when messages arrive too late, arrive unevenly, or overwhelm parts of the network. Dusk designs against those risks directly.
Rather than relying on unstructured gossip, Dusk uses a structured overlay network for propagation. The goal is not raw speed. The goal is controlled diffusion—ensuring that messages spread predictably, without concentrating load or creating information asymmetry between participants.
In many networks, gossip-based propagation rewards nodes with superior connectivity. Those nodes receive information earlier, react faster, and gain subtle advantages over time. This creates an invisible hierarchy, even in systems that claim decentralization. Dusk actively resists that outcome by shaping how information flows.
The structured overlay used by Dusk divides the network into logical neighborhoods. Messages are forwarded along predefined paths instead of being broadcast blindly. Each node knows who it should forward messages to, and under what conditions. This creates balance. No single node becomes a hub. No small group controls dissemination speed.
Fairness in consensus is directly supported by this design. Blocks, votes, and proofs propagate within time windows that are predetermined by the protocol. Consensus timing is in line with the actual behaviour of the network and is not an optimistic estimate.
Another important consequence is resilience under stress. During periods of high activity or partial failure, unstructured gossip can collapse. Messages duplicate excessively, bandwidth spikes, and weaker nodes fall behind. In contrast, Dusk’s propagation limits redundancy by design. Messages travel efficiently, without flooding the network.
This matters especially for a protocol that supports privacy-preserving computation. Proofs, commitments, and certificates are not small. If message propagation were careless, network overhead would scale unpredictably as usage grows. Dusk anticipates this by designing propagation rules that scale with participation, not with noise.
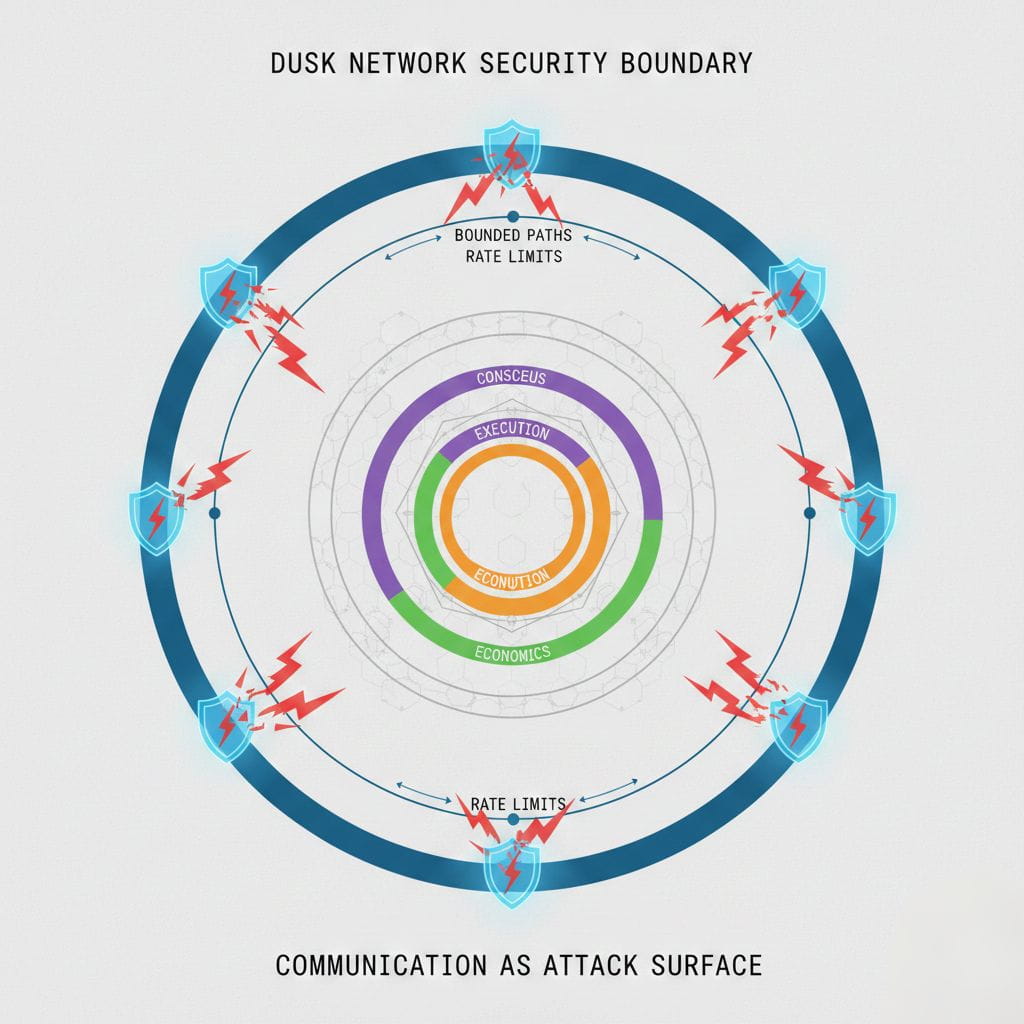
There is also a security angle that is often ignored: denial through congestion. An attacker does not need to break cryptography to disrupt a blockchain. They can attempt to overload message paths, delay critical votes, or selectively partition the network. By using structured propagation, Dusk reduces the effectiveness of such strategies. There are fewer choke points to exploit.
Crucially, the propagation layer is not adaptive in a way that can be manipulated. It does not “learn” optimal routes from observed traffic, which could be gamed. It follows deterministic rules derived from network structure. Predictability here is a strength, not a weakness.
This predictability also improves debuggability and auditability. When something goes wrong in the network, engineers can reason about message paths. They can identify whether a delay came from node failure, connectivity loss, or rule violation. In gossip-based systems, such analysis is notoriously difficult because paths are emergent and opaque.
From a protocol perspective, treating communication as a first-class concern simplifies higher layers. Consensus logic does not need to compensate for wildly variable delivery times. Execution logic does not need to account for extreme propagation asymmetry. The network behaves within bounds the protocol already understands.
The DUSK token indirectly benefits from this stability. Economic incentives assume timely participation. If message delivery were erratic, honest participants could be penalized unfairly simply for receiving information late. By stabilizing communication, Dusk aligns economic outcomes with actual behavior.
There is also a long-term implication. As networks grow, communication overhead often becomes the bottleneck—not computation. Dusk’s approach anticipates that reality. It designs for sustainable growth rather than short-term performance metrics.
What stands out is that Dusk does not treat networking as “plumbing.” It recognizes that in distributed systems, how information moves determines who has power. By constraining and equalizing that movement, the protocol prevents power from accumulating invisibly at the network layer.
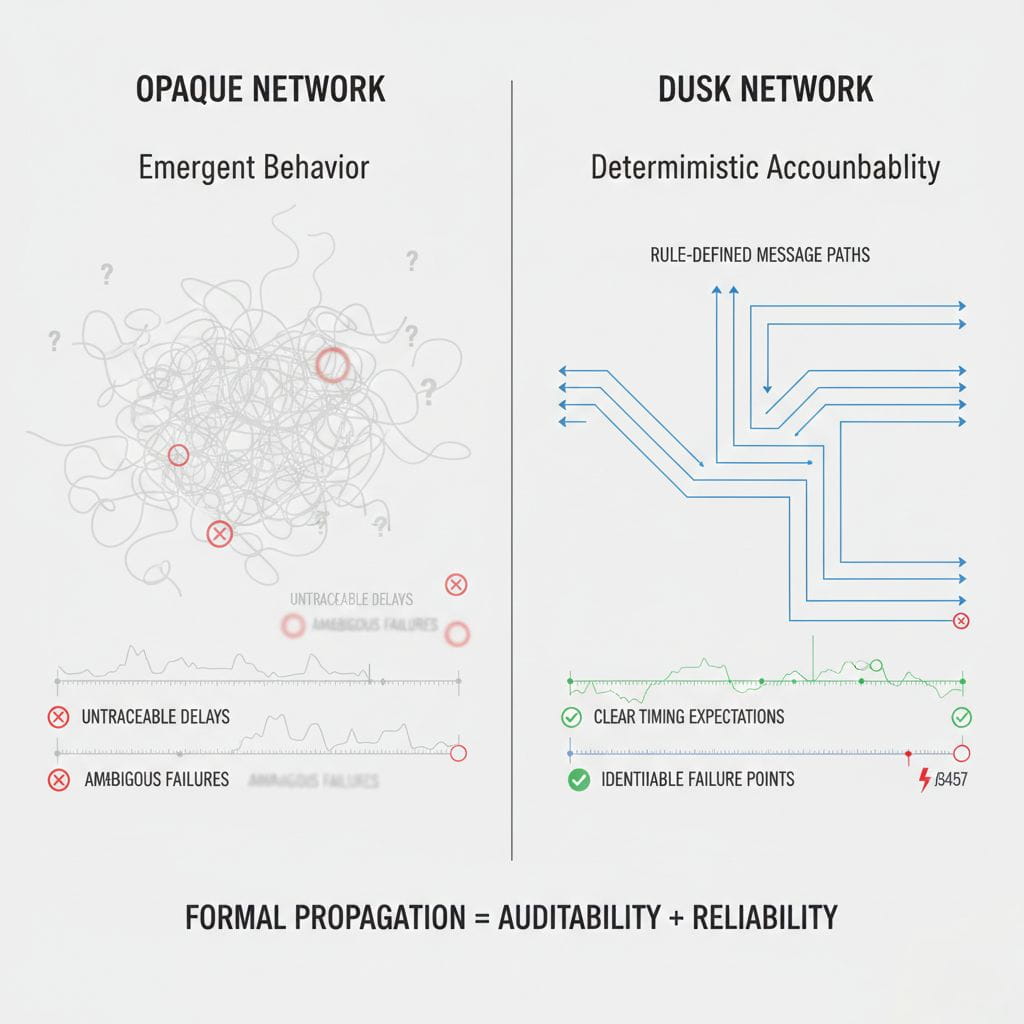
In conclusion, Dusk’s handling of message propagation reflects a broader philosophy: decentralization is not achieved by intention alone. It must be enforced at every layer, including the one most protocols ignore.
By formalizing communication, bounding delivery, and preventing emergent hierarchies, Dusk ensures that consensus, execution, and economics rest on stable ground.
The network does not just agree on blocks.
It agrees on how information reaches agreement.
That discipline is what allows Dusk to function as serious infrastructure rather than an optimistic experiment.

