The Quiet Work of Making Privacy Legible
There’s a particular kind of ambition in crypto that rarely announces itself loudly. It doesn’t promise to overthrow finance or replace everything with “trustless” versions overnight. It shows up instead as an uncomfortable question: can we build a financial system on shared infrastructure without forcing every participant to live under permanent public scrutiny?
That question is less glamorous than most blockchain narratives, but it is closer to how real adoption happens. Financial institutions don’t adopt technology because it feels ideologically pure. They adopt it when it reduces risk, lowers costs, increases control, or makes new products possible without creating new kinds of unmanageable exposure. In that world, “privacy” and “compliance” are not opposing beliefs. They are both operational requirements, and they have to coexist in the same system or the system won’t be used.
Dusk, founded in 2018, is built around that tension. It presents itself as a layer 1 designed for regulated and privacy-focused financial infrastructure—an attempt to make confidentiality a default property while still leaving room for auditability and oversight. The premise is not that rules should disappear, but that financial activity should not be automatically broadcast to the entire internet just to achieve settlement on-chain.
That sounds almost obvious when stated plainly, yet many blockchains are structured in a way that makes it hard to pull off. Public ledgers are powerful because they are shared and verifiable, but they are also unnatural environments for most real financial behavior. In normal markets, confidentiality protects clients, prevents front-running, and keeps counterparties from learning each other’s positions and intentions. A bank does not publish its transaction feed. A fund manager does not reveal trades in real time. A corporate treasury does not want competitors watching its liquidity move around.
The moment you imagine regulated assets living on a fully transparent chain, you start to see the friction. If everything is visible, then ordinary behavior becomes strategically dangerous. Confidentiality stops being a preference and becomes a survival need. But if you swing too far the other way—toward total secrecy—you run headfirst into the reality that institutions operate under continuous accountability. Audits happen. Regulators ask questions. Internal risk committees demand evidence. Records must be retained, reconstructed, and explained. Privacy that cannot be reconciled with oversight doesn’t scale into regulated finance; it gets isolated.
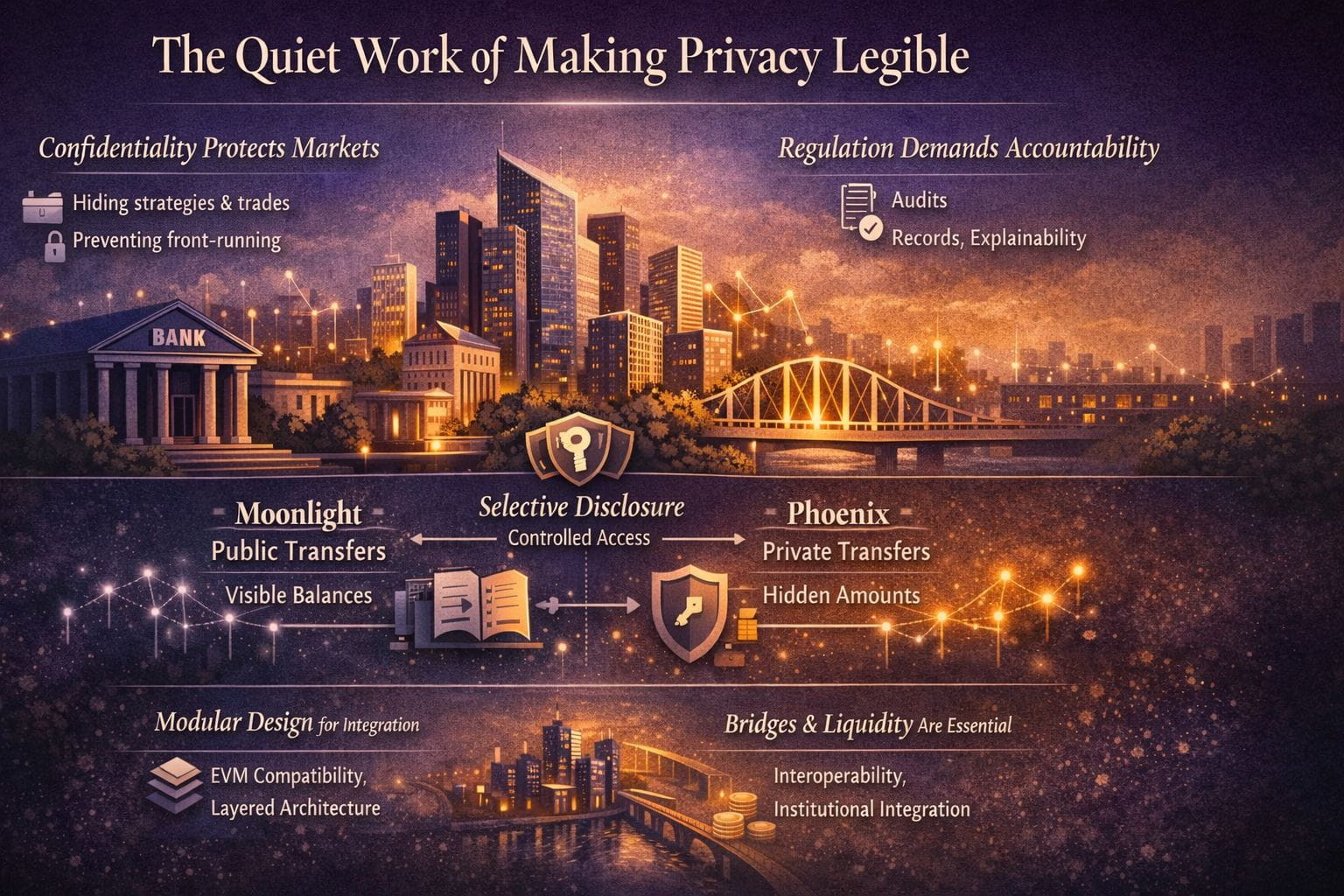
The most interesting part of Dusk is that it appears to accept this as the central design problem rather than treating it as a public-relations obstacle. Its approach to privacy, at least conceptually, is not a demand for absolute anonymity. It’s closer to selective confidentiality—information hidden from the public but revealable under defined conditions to authorized parties. This is a subtle distinction, but it matters. It shifts privacy from being a blanket promise to being a governed capability.
That framing resembles how financial systems handle information today. Confidentiality is normal, but it isn’t arbitrary. Access is controlled. Disclosure can be compelled. There are logs, policies, and responsibilities attached. In other words, the system isn’t “transparent,” but it is accountable.
Dusk’s transaction model reflects that same practicality. Rather than insisting on a single way the world should work, it supports two different kinds of transfers. One is public and account-based, the familiar model where balances and movements are visible. The other is shielded and note-based, using zero-knowledge proofs to keep amounts and linkages private. In crypto culture, multiple modes can be dismissed as compromise. In institutional contexts, it can look like segmentation: different rails for different operational needs.
You can imagine why that could matter. Some flows in regulated environments are meant to be openly verifiable: certain disclosures, treasury reporting, issuance events, or compliance-related views. Other flows are legitimately sensitive: client transfers, trading activity, bilateral settlements, and anything that would create market distortions if exposed. A system that only offers “everything public” or “everything hidden” forces institutions into unnatural choices. A system that supports confidentiality as default, with defined paths to reveal information when required, maps more cleanly to how finance actually works.
The other aspect that reads like someone thinking about adoption rather than ideology is the push toward modular architecture. Most people outside of engineering circles underestimate how much of “adoption” is simply integration. Institutions don’t move onto new infrastructure because they enjoy rewriting everything. They move when the new system speaks the languages they already know, fits into existing vendor relationships, and doesn’t demand a wholesale reinvention of the stack.
Dusk’s modular direction—separating settlement and core privacy primitives from execution environments—resembles a pattern you see in enterprise software when systems need to evolve without breaking every application. It also creates room for pragmatic compatibility choices, like offering an EVM-equivalent environment to reduce friction for developers and integrators. EVM compatibility is not exciting, but it is the kind of boring decision that often determines whether an ecosystem forms at all. Wallet providers, exchanges, custody vendors, and security tooling already orbit the Ethereum execution model. A chain that can interface with that reality stands a better chance of being used, even if its long-term differentiation lives elsewhere.
Of course, compatibility comes with tradeoffs. Borrowing widely-used execution frameworks can also import constraints that matter in finance—especially around finality and settlement assumptions. In consumer crypto applications, delayed finality can be tolerable. In regulated markets, finality is a risk variable. It affects when ownership is considered settled, when collateral can be released, and how exposure is calculated. If a chain wants to support financial-grade settlement, it eventually has to offer crisp answers about when state is final and what failure modes exist. Institutions don’t accept “it’s probably final” as a basis for operational commitments.
This is where the conversation naturally turns away from architecture diagrams and toward governance and operational discipline. In regulated finance, systems are judged not only by how they behave when everything is normal, but by how they behave when things go wrong. What happens during validator outages? How does the system respond to misbehavior? Are penalties calibrated to discourage attacks without making routine incidents catastrophic? Can participants monitor the system in a way that supports audit and risk reporting?
Token economics matters here, but only in the narrow sense that incentives shape operator behavior. A chain that wants to be durable needs validators who remain online, invest in reliability, and have something to lose if they act maliciously. Slashing regimes, staking requirements, and reward structures become tools for reliability engineering as much as they are economic design. The goal is not excitement. The goal is stable security under mundane conditions—quiet incentives that encourage boring, professional operation.
Then there’s the unavoidable reality of bridges and liquidity. In an idealized worldview, a chain could grow into self-sufficiency and treat interoperability as optional. In practice, bridges are the cost of living in a multi-chain world, and liquidity is the cost of building markets. Institutions will not adopt infrastructure that strands assets in an isolated environment, no matter how elegant the base layer is. But bridges expand attack surface, introduce governance complexity, and create failure modes that can be hard to explain in regulatory or audit contexts. Treating bridging as “growth” rather than as risk-managed infrastructure is a common mistake. If Dusk is serious about regulated finance, the long-term credibility of its ecosystem will be shaped as much by how it handles these boring necessities as by the privacy technology itself.
So what might quietly matter here, if anything does? It’s not that Dusk will replace public chains or become the default home for everything. The more realistic possibility is that it becomes useful precisely because it doesn’t try to flatten the world into one model. Regulated finance needs shared settlement infrastructure, but it also needs confidentiality. It needs programmability, but it also needs auditability. It needs composability, but it also needs controls. A chain that builds for that uncomfortable middle—privacy that doesn’t sabotage compliance, and compliance that doesn’t require universal surveillance—could end up being the kind of infrastructure that’s rarely celebrated but frequently used.
Still, that’s only the theory. The hard part is execution, and execution is where institutional narratives usually break down. It’s one thing to describe selective disclosure; it’s another to build key management, governance processes, and access controls that can survive audits, disputes, and internal policy changes without compromising confidentiality. It’s one thing to offer modular layers; it’s another to make them feel coherent in day-to-day operations, especially around finality, risk boundaries, and incident response. It’s one thing to attract builders with familiar tooling; it’s another to sustain an ecosystem of serious operators and integrators who can meet institutional expectations.
And even if the technology holds, institutions apply pressure in their own way. They standardize. They demand specific assurances. They will push for features that reduce their liability and increase their control. The question is whether a system designed for regulated privacy can absorb that pressure without losing the very properties that differentiate it, and whether it can do so while remaining credible to multiple stakeholders at once: developers, validators, auditors, regulators, issuers, and end users.
If Dusk ends up mattering, it will likely be in that slow, quiet register where infrastructure becomes normal. But the more honest ending is uncertainty. The architecture suggests an attempt at pragmatism, not purity. The premise—privacy with accountability—matches how real financial systems are forced to operate. What remains open is whether the project can translate that premise into sustained usage, resilient operations, and institutional trust without being reshaped into something simpler and less nuanced by the realities of regulation, integration, and market structure.