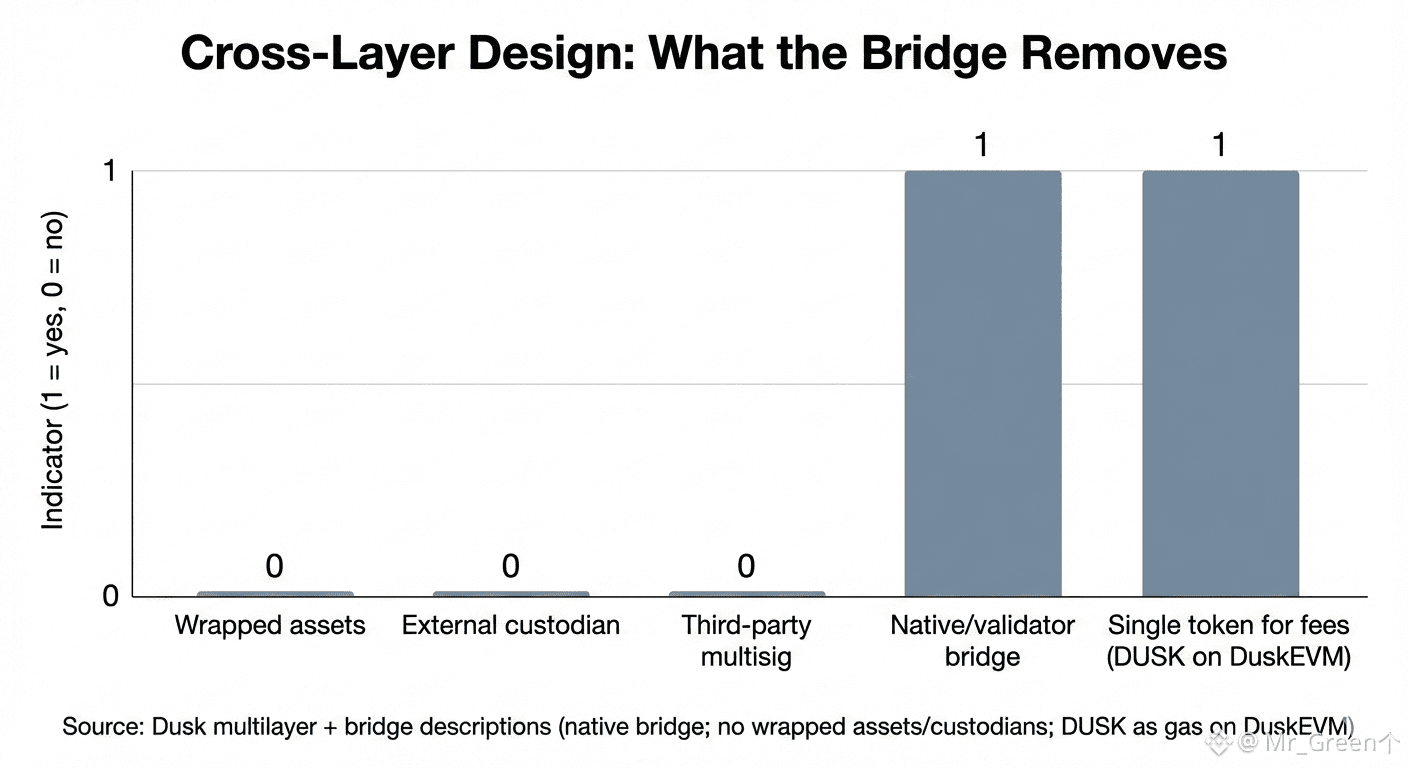
In most crypto systems, bridging is where clean architecture goes to die. You can have a solid base chain and a fast execution layer, but the moment value needs to move between environments, you often end up with wrapped tokens, third-party custodians, or fragile multisig trust. That is why so many hacks don’t start in the core protocol—they start at the “glue.” Dusk’s modular direction tries to avoid that trap by treating bridging as part of the system’s backbone, not an add-on. If the network is going to split responsibilities between DuskDS (settlement/data/consensus) and DuskEVM (EVM execution), then the bridge is not optional. It becomes the hallway connecting the building.
The architectural reason is straightforward. DuskDS is optimized for the parts finance cares about most: settlement integrity, consensus, and the privacy-enabled transaction model. DuskEVM is optimized for what builders care about: an Ethereum-compatible environment where Solidity apps can run without forcing teams to learn a new execution model. If these layers don’t share a reliable native path for assets and messages, the system becomes two chains with an awkward relationship. Users would have to decide where to live, liquidity would fragment, and application design would constantly fight the boundary. A native bridge is what makes modularity usable: assets move to the environment where they deliver the most value, and then they can return to the settlement layer when final accounting matters.
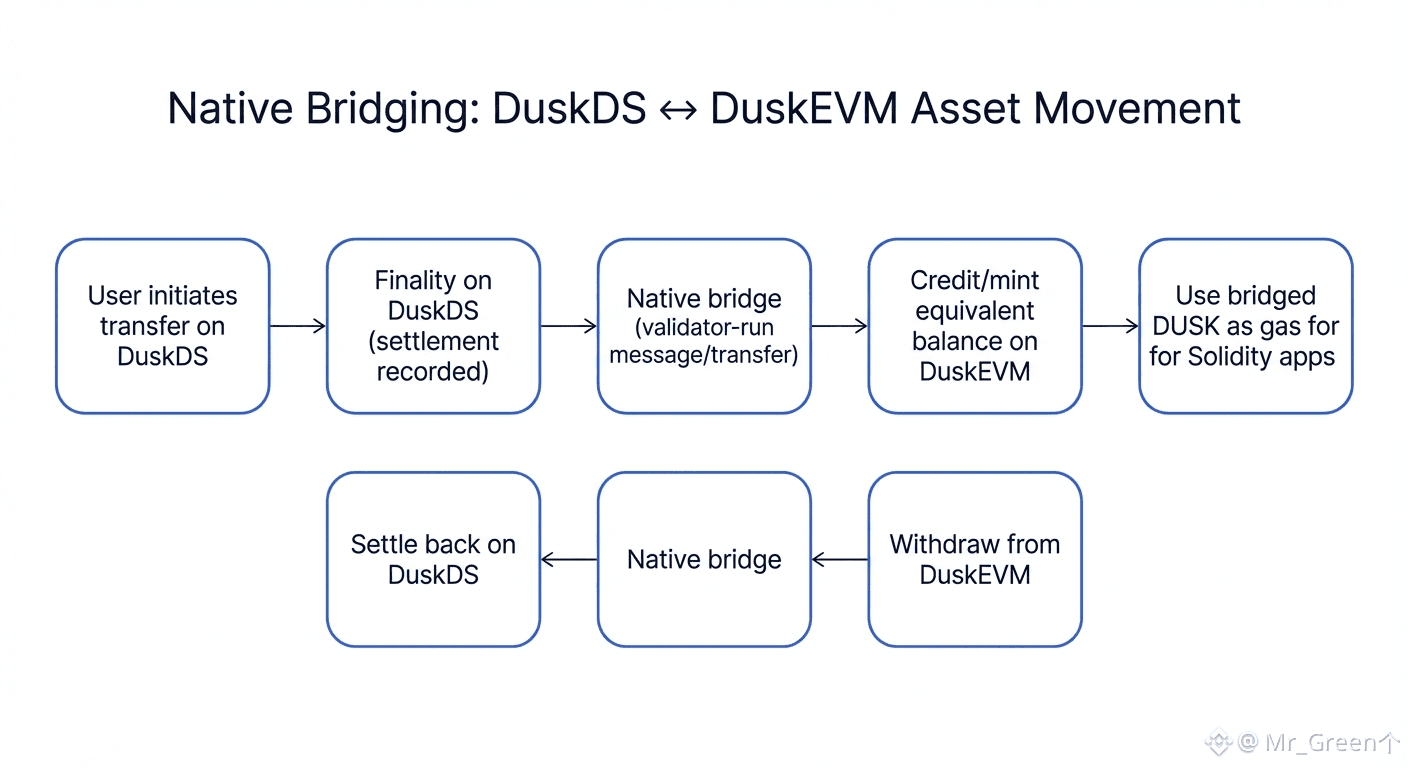
The token design reinforces this. Dusk positions DUSK as the single native asset across the stack, with DUSK used as gas on DuskEVM while still being the core asset tied to the base layer’s economics. That choice sounds small, but it’s strategic. Multi-token modular stacks often create “two economies”: one token for base security and another for execution fees. Over time, that splits incentives, complicates exchange listings, and makes user experience messy. If DUSK is the common denominator, you reduce moving parts. You also make cross-layer movement feel like shifting the same asset between environments—rather than swapping representations that only experts understand.
The hard part, of course, is security. If the bridge is “native” and validator-driven, the bridge’s trust model is tightly coupled to the chain’s trust model. That can be a strength: you’re not outsourcing security to a separate committee or a third-party bridge operator. But it also means the bridge becomes as critical as consensus. Any failure in bridge logic is not a side incident—it’s systemic risk. This is where settlement finality matters more than marketing. A credible cross-layer system needs a clean concept of “when something is final,” because bridging is basically state movement. If DuskDS offers deterministic finality after ratification, then cross-layer transfers can be designed around a stable, unambiguous checkpoint: once the base layer finalizes an outgoing transfer, the execution layer can mint/credit with confidence. In good designs, finality isn’t just about user comfort; it’s a safety primitive for message passing.
There’s also a practical engineering challenge: bridging isn’t only “move coins.” It is also “move meaning.” Modern apps don’t just need balances; they need proofs of events, receipts of actions, and consistent state transitions. If the bridge supports more than a basic token transfer model, you need a message format that’s strict, versioned, and hard to misinterpret across upgrades. That means protocol upgrades become delicate. Validators and nodes must maintain compatibility across releases, because a mismatch in bridge message handling can cause stuck assets, inconsistent accounting, or worse—double credit scenarios. The more native and integrated the bridge is, the more disciplined release engineering must be.
A strong cross-layer system also needs a clear answer to “where is truth recorded?” In a modular stack, execution happens on the execution layer, but settlement truth is often anchored in the base layer. The clean mental model is: DuskEVM runs the application logic and produces outcomes; DuskDS is where final settlement and canonical records live. Bridging is how outcomes and value move in and out of the EVM environment without weakening that anchor. That is why Dusk’s modular story only works if the bridge is reliable: otherwise the separation becomes friction instead of clarity.
What does this unlock in real use cases? It allows Dusk to match environments to requirements without forcing everything into one compromise. A regulated RWA workflow can keep settlement and compliance-sensitive records close to the base layer while still using familiar Solidity execution when it helps. An application can run fast interactions on DuskEVM—where developer tooling is mature—then settle and finalize outcomes through DuskDS. Liquidity can live where it’s most useful, rather than where it’s stuck. Over time, that makes the system feel less like “two chains” and more like “one network with two engines.”
The best way to judge this approach is not by slogans like “trustless” or “native,” but by the specifics of the threat model. How are bridge messages authorized? What events must be finalized before a credit happens on the other side? How do upgrades handle message versioning? What happens during partial outages? How are disputes resolved if a message arrives late or out of order? Those questions decide whether the bridge is just a convenience layer or a true infrastructure layer.
If Dusk gets this right, the bridge stops being the weakest link and becomes a quiet strength: a reliable internal route that lets the stack stay modular without sacrificing coherence. In a world where bridging is often where systems break, treating the bridge like core infrastructure is not just a technical choice; it’s a statement about what kind of chain you want to be.

