The building is awake in a way it shouldn’t be. A strip of white light over a desk. A low fan that never changes speed. One person sitting alone, shoulders forward, laptop open. The dashboard is up. Everyone checks it. No one fully trusts it. It’s where numbers go to become arguments.
A tiny discrepancy is there, calm and stubborn.
Not big enough to trigger alarms. Not big enough to justify waking anyone. Big enough to sit behind the eyes like grit. Big enough to threaten sleep, because you can’t unknow it once you’ve seen it.
They refresh once. Then again. The gap stays.
They open the incident report template almost without thinking. Not because they love process. Because process is what keeps small problems from turning into stories that ruin weeks. The form is blank and indifferent. Time observed. Metric affected. Systems involved. Suspected scope. The cursor blinks in the “Impact” field like it’s waiting for a confession.
At 02:11, impact is always a shadow. You don’t know what it is yet, but you know what it could become. Money that has names attached to it. Payroll. Contracts. Clients. The adult world where mistakes don’t stay technical for long.
This is when slogans start to feel thin.
People say “transparent” like it’s a cure. People say “trustless” like it’s a shield. People say “public” like it automatically means fair. Those words sound clean when nothing is on the line. Then money stops being abstract. Then “it’s decentralized” stops being an explanation and becomes a dodge.
When money becomes payroll, there’s no room for theater. Payroll isn’t an idea. It’s rent. It’s school fees. It’s a quiet promise that you made when you hired someone and told them they could rely on you.
The operator doesn’t reach for philosophy first. They reach for evidence.
What changed. What version ran. Which environment executed. Which wallet signed. What was assumed instead of verified. They follow the path that people follow when they’ve been burned before and learned that hope is not a control.
The dashboard is not the source of truth. It’s a summary. Summaries are always convenient until they become dangerous. They flatten detail. They hide edge cases. They look like certainty while being built on assumptions.
And in serious systems, assumptions are what fail first.
There’s a second mistake people make, quieter than slogans. They treat privacy like a personal preference. In real operations, privacy is often duty. It’s legal obligation. It’s contractual obligation. It’s the difference between protecting people and turning them into a dataset.
At the same time, auditability is non-negotiable. Not because auditors are heroes, but because memory is unreliable and incentives drift. When a regulator asks what happened, you either know or you don’t. When a client asks for assurance, you either have evidence or you’re asking for trust you haven’t earned.
You can’t run adult systems on “trust us.”
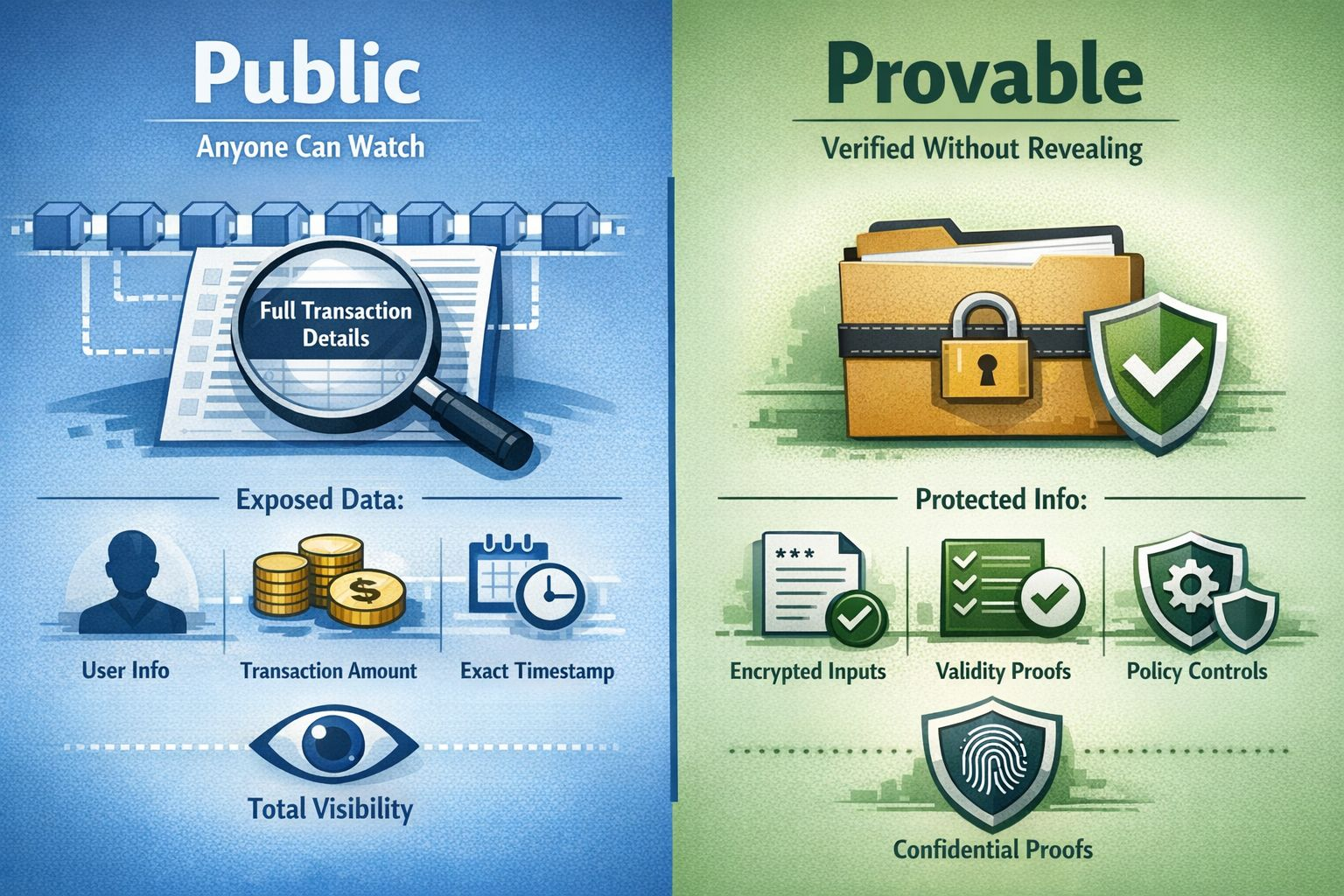
And “public” is not the same thing as “provable.”
Public can mean exposed. Public can mean searchable. Public can mean permanent. Public can mean anyone can watch you bleed slowly.
Provable means accountable.
A system can publish everything and still fail to prove the one thing that matters: that the rules were followed, and that when they weren’t, the exception was recorded, controlled, and explainable.
The operator leans back and rubs their eyes. Their mind goes to a room they’ve sat in before. A room that smells like paper and policy. A room with no windows and a table built for uncomfortable conversations.
The audit room.
In that room, you don’t dump every document you own onto the table. You bring what is needed. You keep sensitive parts protected. You show evidence to authorized hands and record what was accessed and why. You prove a claim without creating collateral damage.
The metaphor that fits is simple: a sealed folder.
The folder exists. The contents exist. It can be opened. But not for everyone, not all the time, not without a record. The existence of the folder is not a secret. The discipline around the folder is the point.
Selective disclosure is the grown-up version of transparency. It admits something basic: not everyone is entitled to everything. And it refuses the coward’s escape of “just trust us.” It says: we can prove this to the right parties, under defined rules, without dumping private lives into public view.
Because indiscriminate transparency causes harm in ways dashboards don’t measure.
Client positioning can be inferred from patterns. Trading intent can be hunted. Negotiation leverage can be stripped away before a conversation even happens. Salaries can be guessed from payroll rhythms, even if names aren’t on-chain. A public ledger can turn ordinary work into permanent exposure, and permanent exposure changes behavior. People stop taking reasonable risks. People start hiding. Markets become a game of who can analyze the fastest, not who can operate the best.
Data doesn’t need names to hurt people. Structure is enough. Timing is enough. Repetition is enough.
This is where private transactions stop being a moral debate and become a technical requirement. Not invisibility. Not escape. Confidentiality with enforcement.
Phoenix private transactions, as an idea worth taking seriously, aim for that: validity proofs without leaking details. The action can be checked against constraints without broadcasting sensitive inputs. You can prove correctness without spilling the whole story. You can satisfy policy without turning the policy context into public entertainment.
It’s the sealed folder, but built into the workflow.
That’s where the phrase “compliance by design” either means something real or means nothing. If compliance is something you do after the fact, it becomes paperwork and apology. If compliance is embedded in the workflow, it becomes constraint and proof. It becomes a system that says no when it should, and can prove why later.
Vanar’s architecture, in this operational frame, leans into containment. Modular execution environments over a conservative settlement layer.
The words are technical, but the motive is plain. Let the part that changes quickly have boundaries. Let the part that settles value be boring and dependable. Keep the foundation calm so the building doesn’t shake every time someone updates a feature.
Settlement should be boring. That is not an insult. It is a compliment. Boring is what you want when other people’s money and obligations are involved. Boring is what you want when you’re trying to sleep.
Separation is containment. It reduces blast radius. It makes audits cleaner. It gives you a way to evolve execution without constantly rewriting the meaning of finality.
EVM compatibility, in this same spirit, is not a trophy. It is fewer surprises. Familiar execution patterns can reduce the number of unknown behaviors that show up under stress. Familiar tooling can make monitoring and incident response faster. It doesn’t guarantee safety, but it narrows the space in which weird failures can hide.
Then there’s the token, $VANRY, which people love to treat like a scoreboard. In the room at 02:11, that framing doesn’t help. What matters is responsibility. Staking as bond. Staking as accountability. A mechanism that makes participation carry consequence, because consequences are how adult systems keep promises from drifting into wishful thinking.
None of this eliminates sharp edges.
Bridges and migrations are sharp edges. Moving from ERC-20 or BEP-20 representations into a native asset is where clean diagrams meet messy reality. Address mistakes. Network confusion. Contract versions. Timing windows. A single misread prompt. A single rushed approval. A single person skipping a checklist because they’re tired and the pressure is quiet but constant.
Key management is a sharper edge than any bridge. Keys don’t fail gradually. They fail completely. A seed phrase copied somewhere it shouldn’t be. A hot wallet used “temporarily” until temporary becomes permanent. Permissions that aren’t revoked after role changes. Recovery procedures that exist only in someone’s memory, which is to say they don’t exist at all.
And when these things go wrong, trust doesn’t fade slowly. Trust doesn’t degrade politely—it snaps.
That’s why the operator keeps writing. They’re building a record that will survive later conversations, when the mood is different and the stakes are clearer. They’re not trying to look competent. They’re trying to be accountable.
As the incident report fills in, it stops being just a timeline and becomes something else. Not a motivational story. Not a pitch. A sober statement about how systems should treat people when people are tired, when people are rushed, when people make mistakes.
Policy logic should live where actions happen. Permissions should be explicit. Controls should be enforceable. Revocation should be normal, not embarrassing. Recovery should be possible, not mythical. Audit trails should be complete. Proof should be available to authorized parties without turning private details into public harm.
This is the adult world: obligations that don’t care how elegant your architecture is.
The discrepancy eventually collapses into an explanation. Not comforting. Just real. A sequencing detail. A reconciliation delay. A missed step caught early enough to stay small.

The operator saves the report. Closes the laptop halfway. Doesn’t celebrate. Doesn’t feel heroic.
Because the point was never drama.
The point was to be able to prove what happened, to the right people, without exposing everyone else to what they never consented to reveal.
There are two rooms that matter.
The audit room, where the sealed folder has to exist and the proofs have to hold.
And the other room, quieter and heavier, where someone signs under risk—where a client agrees, where a company attests, where responsibility becomes real and irreversible.
That’s where compliance stops being a slogan and becomes design.
