Hello Binance Family... In this article I'll tell you about @Dusk Foundation..
Dusk Foundation is built around one core idea: financial privacy that still works with real-world rules. Technically, everything in the network is designed to support private transactions, regulated assets, and secure execution without leaking sensitive data. What makes Dusk different is how all these pieces fit together instead of working in isolation.
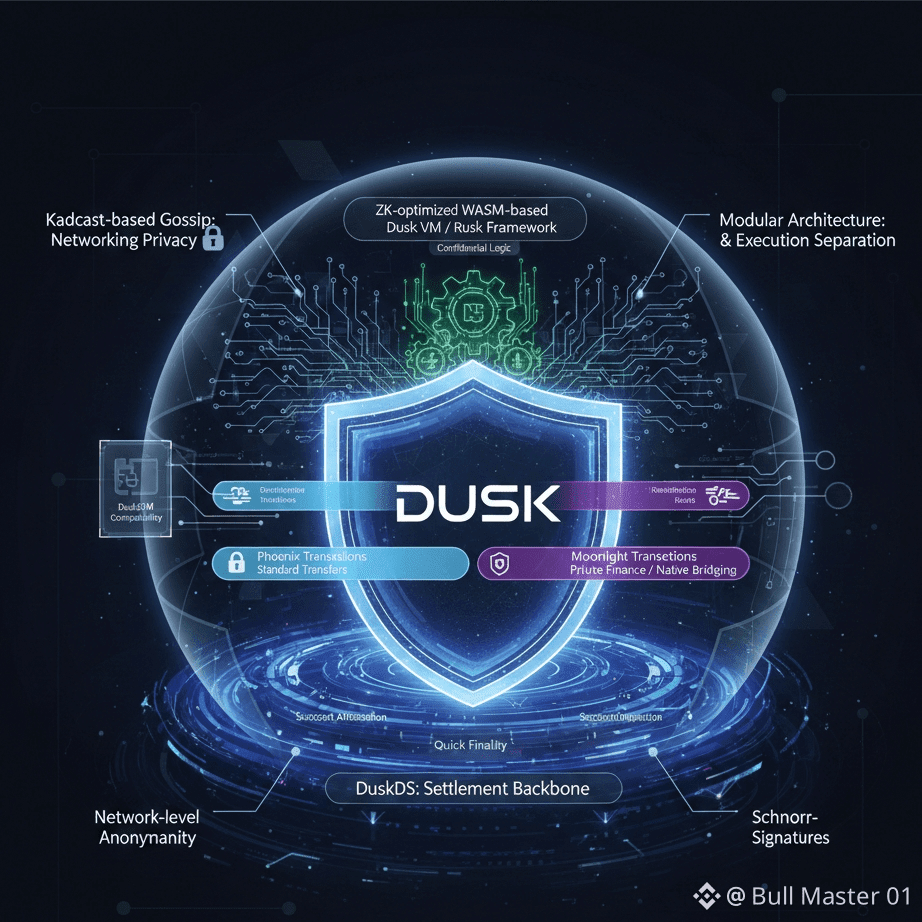
At the base layer, Dusk uses something called DuskDS, which acts as the settlement backbone of the network. This layer is responsible for consensus, transaction finality, and data availability. Instead of traditional block production, it relies on a proof-of-stake model called Succinct Attestation, which keeps validation efficient and secure. Transactions finalize quickly, and the network avoids unnecessary forks, which is important for financial use cases where certainty matters more than speed hype.
Networking privacy is handled through Kadcast-based gossip, which spreads transactions in a way that hides where they came from. This makes IP-level tracking much harder. In simple terms, even if someone watches the network traffic, they can’t easily trace transactions back to individual users or nodes. This is an underrated feature that adds real-world privacy beyond just cryptography.
Dusk supports two transaction modes, which is actually very smart. Phoenix transactions work like standard transfers and are lighter and faster. Moonlight transactions are fully privacy-focused and designed for sensitive financial activity like tokenized securities. Moonlight also allows native bridging, meaning assets can move across environments without exposing private details.
For execution, Dusk does not rely on a generic virtual machine. Instead, it uses a ZK-optimized WASM-based runtime, often referred to as Dusk VM. This environment is designed specifically for zero-knowledge applications. It avoids common memory leaks and side-channel risks found in many smart contract systems. Developers can write confidential logic using the Rusk framework, which natively supports cryptographic proofs rather than treating them as add-ons.
Privacy is enforced using proven cryptographic tools. Dusk relies on PLONK zero-knowledge proofs, which are efficient and small in size, making them suitable for on-chain verification. Poseidon hashing is used because it works well inside ZK circuits. BLS12-381 curves allow signature aggregation, reducing overhead, while Schnorr signatures keep keys compact and secure. All of this helps the network stay fast while remaining private.
Earlier versions of the network used Segregated Byzantine Agreement, which separated block proposal from validation using sortition. This design helped prevent forks and improved finality. While the architecture has evolved, the core principle remains the same: split responsibilities so no single layer becomes a bottleneck.
One of Dusk’s strongest technical choices is its modular architecture. Settlement and execution are separated, which means the network can support different execution environments at the same time. This is why DuskEVM compatibility is possible without sacrificing privacy features. Developers can build standard smart contracts or highly confidential financial logic, depending on what the application needs.
Finally, Dusk adds network-level anonymity, inspired by privacy routing systems like I2P. This protects users and institutions from traffic analysis, which is especially important for large financial transactions where timing and patterns can reveal sensitive information even if amounts are hidden.
In short, Dusk’s technical strength comes from combining consensus efficiency, execution safety, cryptographic privacy, and network anonymity into one system. It’s not designed for hype-driven apps. It’s designed for finance that actually needs discretion, compliance, and reliability.

