Security has always been a top priority at Binance, but even the most advanced infrastructure works best when users play their part. Your account security ultimately depends on daily habits, smart configuration, and awareness of common attack vectors.
The crypto industry moves fast, and so do attackers. By following a few practical steps and building good security routines, you can dramatically reduce the risk of unauthorized access and protect your funds with confidence.

1. Use a Strong Password and Update It Regularly
A strong password is the foundation of your account security. It should be long, unique, and impossible to guess. Mixing uppercase and lowercase letters, numbers, and special characters makes brute-force attacks far more difficult. Using the same password across multiple platforms is one of the most common mistakes and one of the easiest ways attackers gain access.
Password managers are an effective solution for generating and storing complex passwords securely. Reputable tools encrypt your credentials and allow you to manage them in one place, protected by a strong master password. Changing your passwords periodically is also important, especially for your Binance account and the email address linked to it.
Email security deserves special attention. Since email is often used for confirmations and recovery, a compromised inbox can undermine every other security measure. Using separate email addresses for different services limits the impact of data breaches. Tools like Have I Been Pwned can help you check whether an email address has appeared in past breaches.
After changing your Binance password, withdrawals are temporarily disabled for 24 hours. This safeguard exists to prevent attackers from immediately draining funds if credentials are compromised.
2. Enable Two-Factor Authentication (2FA)

Two-Factor Authentication adds a second layer of defense beyond your password. Binance supports both SMS-based verification and app-based authenticators, but app-based options are widely considered more secure. Using Google Authenticator significantly reduces the risk of account takeover.
SMS-based 2FA is more vulnerable to SIM-swapping attacks, where attackers convince mobile carriers to transfer your phone number to a new SIM. High-profile cases have shown how damaging this can be. App-based authenticators are not tied to your phone number, making them much harder to compromise. Always back up your recovery key so you can restore access if you change devices.
3. Review Authorized Devices and Account Activity
Every device that accesses your account leaves a trace. Binance allows you to review and manage authorized devices through its security settings. If you notice unfamiliar devices or ones you no longer use, removing them immediately cuts off potential access points.
Monitoring login activity is equally important. Unrecognized IP addresses or login times can indicate a security issue. If something looks wrong, disabling your account will suspend trading and withdrawals, revoke API keys, and remove all authorized devices until the issue is resolved. This makes email security even more critical, as confirmations are sent there.
4. Control Withdrawal Addresses
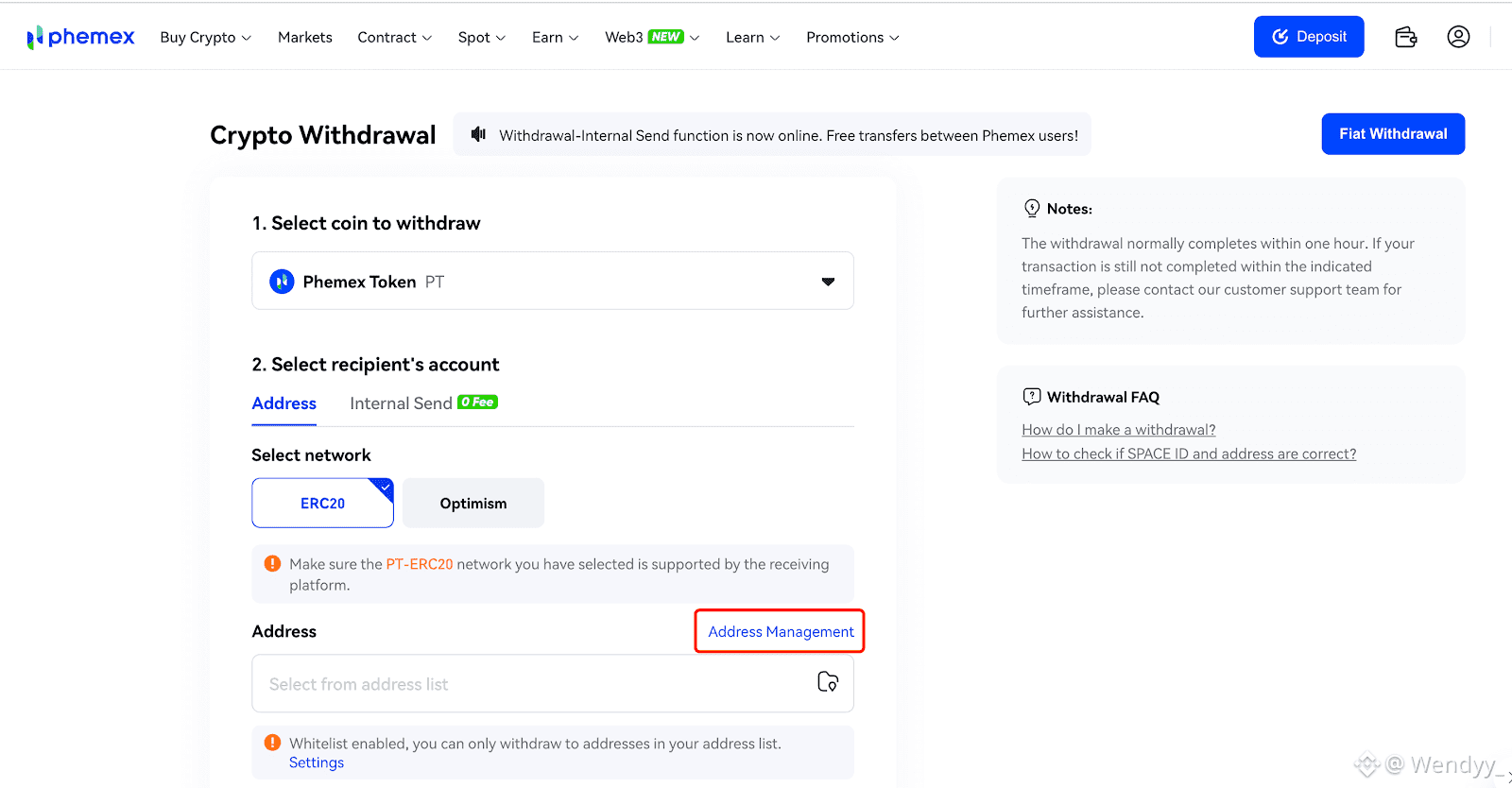
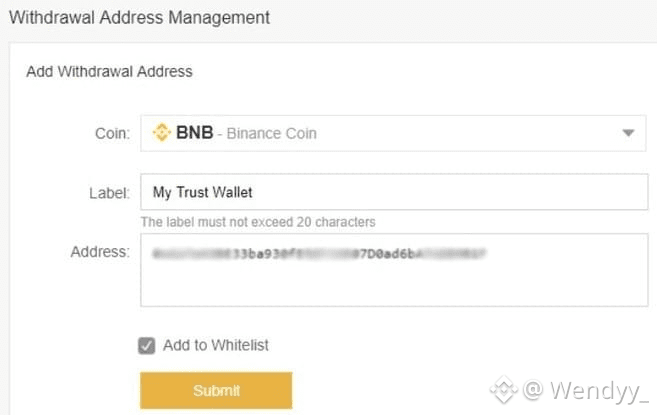
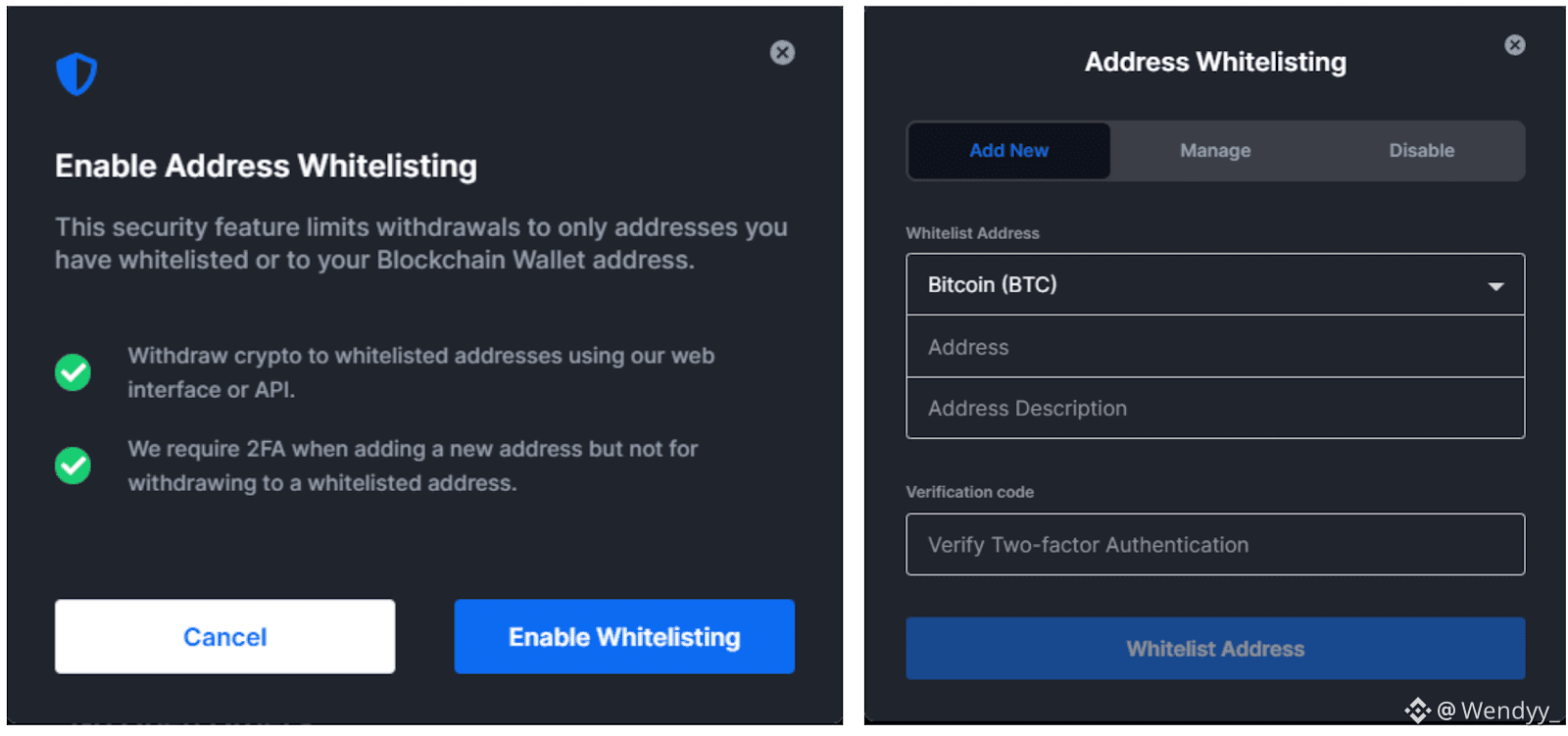
Address Management allows you to whitelist withdrawal addresses, meaning funds can only be sent to approved wallets. Each new address requires email confirmation before it becomes active, adding another layer of protection against unauthorized withdrawals.
When choosing where to withdraw your funds, secure wallets matter. Software wallets like Trust Wallet are convenient for everyday use, while hardware wallets keep private keys offline for maximum security. The key principle is simple: only withdraw to wallets you fully control and trust.
5. Learn to Recognize Phishing Attempts
Phishing remains one of the most effective attack methods in crypto. Attackers often create fake websites or send messages that appear to come from Binance, hoping users will enter their credentials.
A simple but powerful habit is accessing Binance only through a saved bookmark rather than typing the URL each time. This avoids many lookalike websites designed to steal login information. Binance also offers an Anti-Phishing Code feature, which embeds a personal code in official emails so you can instantly tell whether a message is genuine.
Understanding phishing techniques is one of the best defenses. Awareness turns many attacks into obvious red flags before any damage is done.
6. Follow API Security Best Practices
Advanced traders often use the Binance API to automate strategies and connect third-party tools. While powerful, API keys introduce additional risk because they allow external applications to interact with your account.
Restricting API access by IP address ensures that only approved locations can use your keys. Regularly rotating API keys and never sharing them unnecessarily reduces exposure. Treat API credentials with the same care as passwords, because misuse can lead to financial loss even without direct account login.
7. Use Universal 2nd Factor (U2F) Authentication

For an extra layer of protection, Binance supports Universal 2nd Factor authentication using hardware devices such as the Yubico YubiKey. Unlike software-based authenticators, U2F requires physical access to the device itself.
This means that even if someone learns your password, they still cannot access your account without the hardware key. For users holding significant balances, U2F is one of the strongest defenses available.
Final Thoughts
Securing your Binance account doesn’t require advanced technical skills. It requires consistency, awareness, and a few smart configurations. Strong passwords, reliable 2FA, careful device management, and phishing awareness work together to form a robust defense.
Crypto puts control directly in your hands. With that control comes responsibility. By following these steps and checking your Security Dashboard regularly, you can trade and invest with far greater confidence, knowing your account is protected by both strong systems and smart habits.




