In most blockchain networks, communication is often treated as something that just happens in the background. Developers usually rely on gossip protocols, where nodes randomly share information and the network is expected to eventually synchronize. This method can work when there are only a few participants but it starts causing problems as the network grows. Messages take uneven amounts of time to reach different nodes, some nodes end up handling too much traffic, bandwidth usage becomes unpredictable, and certain nodes unintentionally become communication hubs. Dusk Network decided to take a different approach by clearly defining how messages travel across the network instead of leaving it to chance.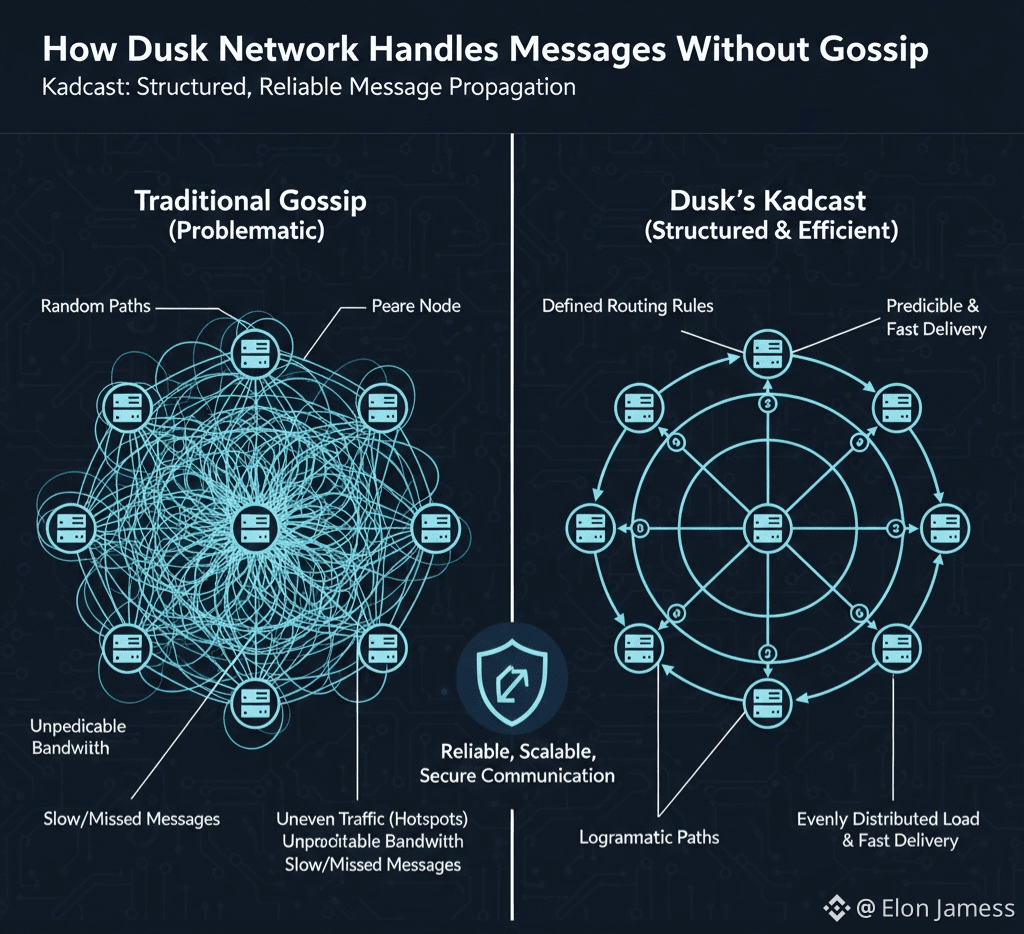
Dusk uses a protocol called Kadcast to manage message propagation. Kadcast is not like a regular gossip system. It is a structured overlay network. Each node keeps a small, clearly defined set of peers and forwards messages following fixed routing rules. This means that when a message is sent, its path through the network is predictable and bounded instead of random. The design of Kadcast fits perfectly with the needs of Dusk. Messages involved in consensus, block proposals, and validation must reach all nodes within a set time for the network to operate correctly. Gossip networks cannot provide that kind of guarantee. Kadcast limits message fan-out and ensures messages move along logarithmic paths instead of being broadcast to everyone. This reduces variance and keeps the network predictable.
Kadcast also helps control bandwidth. In gossip systems, well-connected nodes often end up carrying a lot of the network traffic. Over time this can push the network towards centralization because only high-resource nodes can keep up. Kadcast distributes forwarding duties more evenly. No node is permanently a relay point for the entire network. Instead, routing responsibilities appear naturally through the network overlay, not because a node is popular or manually assigned. This also makes the network safer. Structured paths allow nodes to detect abnormal behavior. If expected messages do not arrive on time, nodes can tell whether it is a network delay or malicious interference. An attacker would need to control a large portion of the routing space to cause real damage.
Another advantage of Kadcast is that it can handle different types of messages differently. Not all messages are equally important. Consensus-critical messages get priority while less critical communication follows slower paths. This prevents congestion caused by non-essential traffic and keeps the network responsive. From an economic standpoint, this matters too. Validators and block generators stake DUSK tokens to participate. They rely on predictable network costs to maintain their nodes. Spikes in bandwidth could make running a node expensive or unreliable. By keeping message paths structured and bounded, Kadcast helps stabilize network costs over time.
Kadcast also improves scalability. As the network grows and more nodes join, the message propagation does not grow linearly. Because each node only communicates with a limited set of peers along defined paths, adding participants does not multiply network traffic. Existing nodes do not need to change their connections. This allows Dusk to scale without slowing down message delivery or increasing delays. Another benefit is diagnosability. Because the network paths are predictable, it is easier to track down missed messages, delays, or inconsistencies. This reduces reliance on external monitoring and makes auditing and debugging the network easier.
Overall Kadcast is not just an optimization. It is a fundamental part of the Dusk Network that makes the rest of the protocol work as intended. It minimizes uncertainty, prevents hidden centralization, and aligns network behavior with the timing and security assumptions of the protocol. By using defined communication paths instead of gossip, Dusk ensures that the network operates reliably and predictably.
Message propagation is often overlooked but it is critical. Dusk’s structured approach shows a commitment to building long-term infrastructure rather than an experimental system. Gossip networks may work in small setups but they cannot guarantee delivery times, manage bandwidth fairly, or scale efficiently. Kadcast solves these problems by providing predictable routing, prioritizing critical messages, evenly distributing workload, and supporting scaling without compromising security or costs.
The network design also supports real-world use cases. Consensus messages, block proposals, and validation signals must arrive within known time frames. Nodes can detect failures or interference more quickly because message paths are structured. Bandwidth usage is predictable, so validators can calculate costs. As the network grows, adding new nodes does not disrupt operations or multiply traffic uncontrollably. These features make Dusk suitable for long-term deployment and large-scale adoption.
In conclusion Kadcast is a quiet but essential part of Dusk Network. It replaces random gossip with a structured message propagation system that is reliable scalable secure and predictable. This design improves the network’s ability to function as real infrastructure that can handle growth and support financial applications. By focusing on communication and message delivery Dusk Network ensures that consensus and validation work smoothly, costs stay manageable, and the network remains resilient against failures and attacks. It is a fundamental choice that makes all other features of the protocol possible.

