The first time I tried to explain a “private” deal on a public chain to a non crypto friend, I watched their face change. They did not care about blocks or gas. They cared that anyone could trace who paid who, when, and how much. That is the real wall most finance workflows hit on a permissionless network.
A permissionless chain is great at one thing: neutral settlement. Anyone can validate, anyone can inspect rules, and the network keeps moving even if a single party disappears. The problem is that many real workflows are permissioned by nature. Not because people love gatekeeping, but because law, risk, and basic business reality demand it. A broker cannot match orders for sanctioned parties. An issuer cannot let restricted shares trade freely. A fund manager cannot broadcast every position to the entire internet.
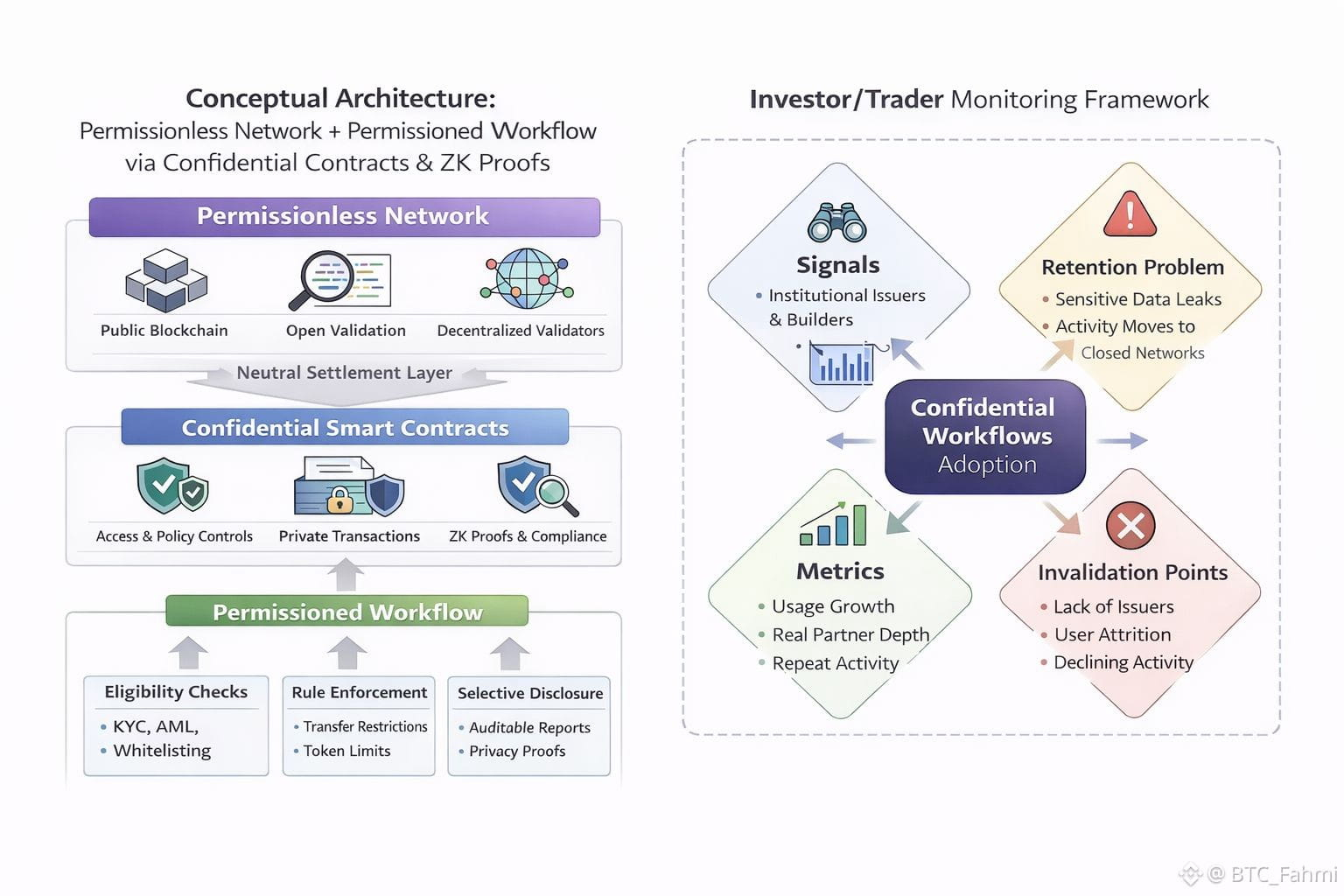
So the question in this title is not a marketing one. It is a design question. How do you keep the base layer open, while making the application layer behave like a regulated system when it needs to?
The core idea is simple. “Permissioned workflow” does not have to mean “permissioned network.” A network can stay open for validators and still support applications that enforce access, roles, and transfer rules. The trick is where you put the permissioning. You put it in the contract logic and the proofs, not in a private validator set.
This is where Dusk’s approach is useful to understand. It is built around confidential smart contracts, meaning a contract can enforce rules without exposing all the underlying data to everyone watching the chain. Dusk’s own materials frame this as privacy that still fits regulatory needs, aimed at financial market use cases rather than pure retail activity.
In practice, permissioned workflows usually require three things.
First, eligibility. A user must prove they are allowed to do the action. That can mean KYC done, jurisdiction allowed, accreditation status, or simply being part of a known counterparty list.
Second, policy. Transfers often need constraints. Think lockups, whitelists, maximum holders, or limits on who can receive a token.
Third, auditability without oversharing. Regulators and internal risk teams need a trail. Counterparties often need confidentiality. Those are not opposites if the system supports selective disclosure.
Confidential execution plus verifiable proofs is how you bridge that gap. A user can prove “I meet the rule” without publishing the personal data that makes the proof true. Validators can still confirm the transaction followed the rules because they verify the proof, not the raw data. Dusk describes its stack as permissionless at the network level, while using zero knowledge and its transaction model to support private and compliant behavior at the application level.
Now bring this back to traders and investors, because narratives do not pay you, flows do.
As of February 3, 2026, DUSK trades around ten to eleven cents, with market cap around $52M to $53M and 24 hour volume around $18M to $19M depending on venue. Circulating supply is shown near 497M. That is liquid enough to trade, but still small enough that sentiment swings can matter.
But the market data belongs in the middle of the story, not the start, because price only becomes meaningful when you know what adoption would look like.
The current trend that makes this category worth watching is the steady growth of onchain dollars and tokenized real world assets. Coin aggregates put total stablecoin market cap a bit above $312B right now. Data from RWA.xyz shows a “distributed asset value” of about $24.17B and stablecoin value of about $293.45B on its dashboard. You can argue about definitions, but you cannot argue about direction. More value is trying to live on public rails, and public rails are brutally transparent by default.
That is why permissioned workflows on a permissionless chain matter. They are not a nice feature. They are what makes institutions stay after the first pilot.
This is also where The Retention Problem shows up. Most teams can get a demo partner. Retention is harder. If the workflow forces them to leak sensitive data, they will quietly move the real activity back to spreadsheets, private databases, and closed networks. The chain becomes a press release, not a system. Users do not leave because they hate crypto. They leave because the product makes them feel exposed.
Here is a real life style example from how I think about it as a trader who also watches product risk. Imagine a small issuer trying to run a compliant secondary market for a tokenized instrument. They need transfer rules, a way to block bad actors, and a way to show auditors what happened. On a fully transparent chain, even if the transfer rules work, the issuer may still reject it because positions and counterparties become public. If the system supports confidential logic with selective disclosure, the same issuer can keep the network benefits while meeting privacy expectations. That is a retention win, not a gimmick.
Dusk’s mainnet launch date matters here because retention only starts once the network is live and boring. Some market trackers and updates summarize mainnet going live on January 7, 2026, following prior upgrades in late 2025. If you are evaluating this as an investment theme, you should treat “live chain plus real users” as the first gate, not the finish line.
What should you watch next, without falling into hype?
Watch whether confidential workflows attract real issuers, brokers, or fintech builders who actually have compliance constraints. Watch whether activity grows in a way that looks sticky, not just a one week spike. Watch whether tools make it easier to build these flows without custom cryptography work every time. And watch whether the project communicates clearly about what is private, what is provable, and what can be disclosed when needed.
If you want to trade it, treat it like an adoption bet with clear invalidation points. If permissioned workflows do not keep users onchain, liquidity will not save it. If they do, you will see it first in steady usage, partner depth, and repeat activity, not in viral posts.
My call to action is simple. Pull up the live token metrics, then spend the same amount of time reading how the system enforces privacy and compliance in practice. Track usage signals weekly, not emotionally. If the retention problem gets solved, the chart will eventually reflect it.
