In 1934, Switzerland codified banking secrecy into law, it created a global sanctuary for financial privacy that would define wealth protection for generations. This system balanced legitimate confidentiality with eventual regulatory cooperation, much like modern privacy-preserving DeFi protocols.
The fundamental tension between transparency and privacy has existed throughout financial history, from numbered Swiss accounts to the 1990s Crypto Wars over encryption, where the U.S. government attempted to mandate backdoors through the Clipper Chip proposal.
Blockchain technology initially swung the pendulum toward radical transparency. Bitcoin's public ledger created an unprecedented level of financial visibility where every transaction could be traced by anyone. While this transparency solved the double-spend problem, it created new challenges for commercial confidentiality, personal financial privacy, and protection against front-running and predatory trading strategies.
The emergence of zero-knowledge proofs represents the latest chapter in this ongoing balance. These cryptographic breakthroughs enable verification without disclosure, allowing blockchain networks to maintain their trustless nature while restoring necessary privacy protections. Just as Swiss banks eventually developed mechanisms for legitimate regulatory cooperation, modern privacy protocols are building compliance into their fundamental architecture.
II. What Are Privacy-Preserving DeFi Protocols?
❍ Core Privacy Technologies
Privacy-preserving DeFi protocols utilize advanced cryptographic techniques to protect user data while maintaining blockchain verifiability. The three primary technological approaches each solve the privacy problem differently.
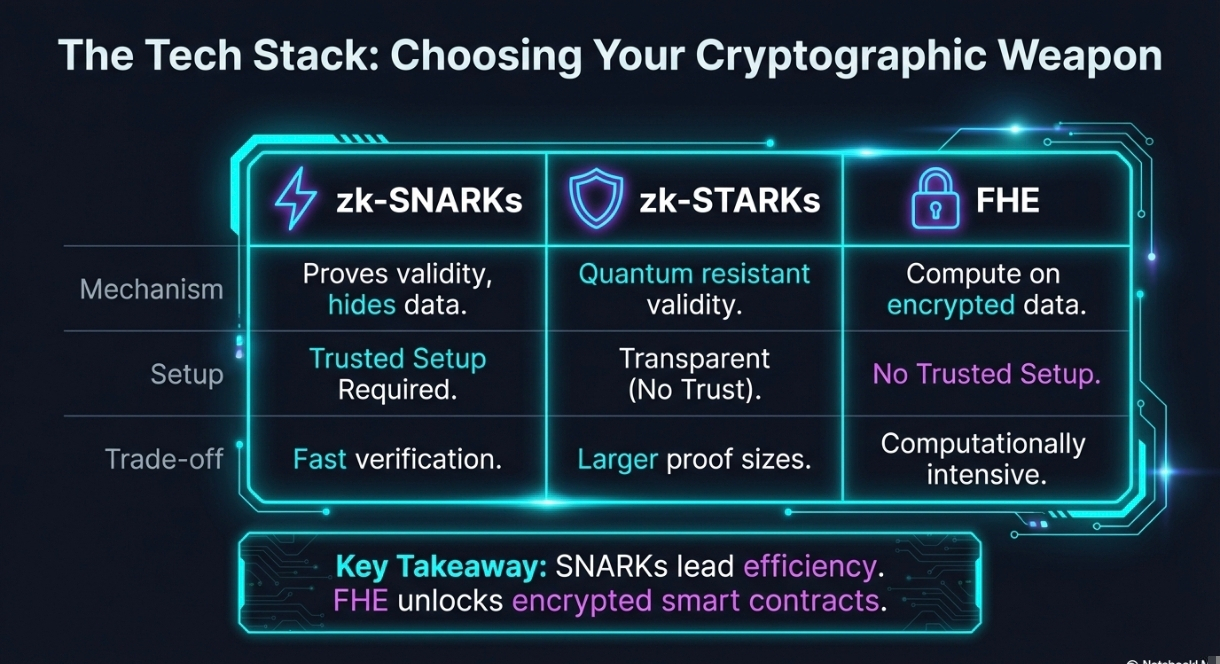
zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge) enable one party to prove to another that a statement is true without revealing any information beyond the validity of the statement itself. This technology powers protocols like Zcash and Aztec Network, allowing users to verify transaction validity without exposing sender, receiver, or amount details. zk-SNARKs require a trusted setup but generate small proofs that verify quickly on-chain.
zk-STARKs (Zero-Knowledge Scalable Transparent Arguments of Knowledge) offer similar functionality without requiring a trusted setup, making them more transparent and quantum-resistant. However, they generate larger proof sizes, which can increase gas costs. This trade-off makes them suitable for applications where trust minimization is paramount and larger proof sizes are acceptable.
Fully Homomorphic Encryption (FHE) takes a fundamentally different approach by allowing computations to be performed directly on encrypted data without decryption. Zama's FHEVM implementation enables confidential smart contracts where data remains encrypted throughout processing. This technology is particularly valuable for applications requiring complex computations on sensitive data while maintaining end-to-end encryption.
❍ Privacy Pools vs. Mixing Protocols
Modern privacy protocols have evolved beyond simple mixing techniques. Early solutions like Tornado Cash used mixing pools to break the link between sender and receiver, but this approach provided limited functionality and faced regulatory challenges due to its indiscriminate anonymity.

Privacy pools represent a more sophisticated approach. Protocols like Railgun create shielded pools where users can deposit assets and then use them for various DeFi activities without revealing their entire transaction history. These systems maintain cryptographic links between transactions for the user while keeping them opaque to external observers.
The key differentiation lies in selective disclosure capability. Modern privacy protocols incorporate features like view keys that allow users to voluntarily disclose transaction details to authorized parties such as auditors or tax authorities. This programmable compliance distinguishes them from anonymous transactions and makes them compatible with regulatory frameworks.
III. How Privacy-Preserving DeFi Works
❍ Zero-Knowledge Proof Generation Process
The magic of zero-knowledge proofs lies in their ability to verify truth without revealing information. The process involves four key components working in concert.
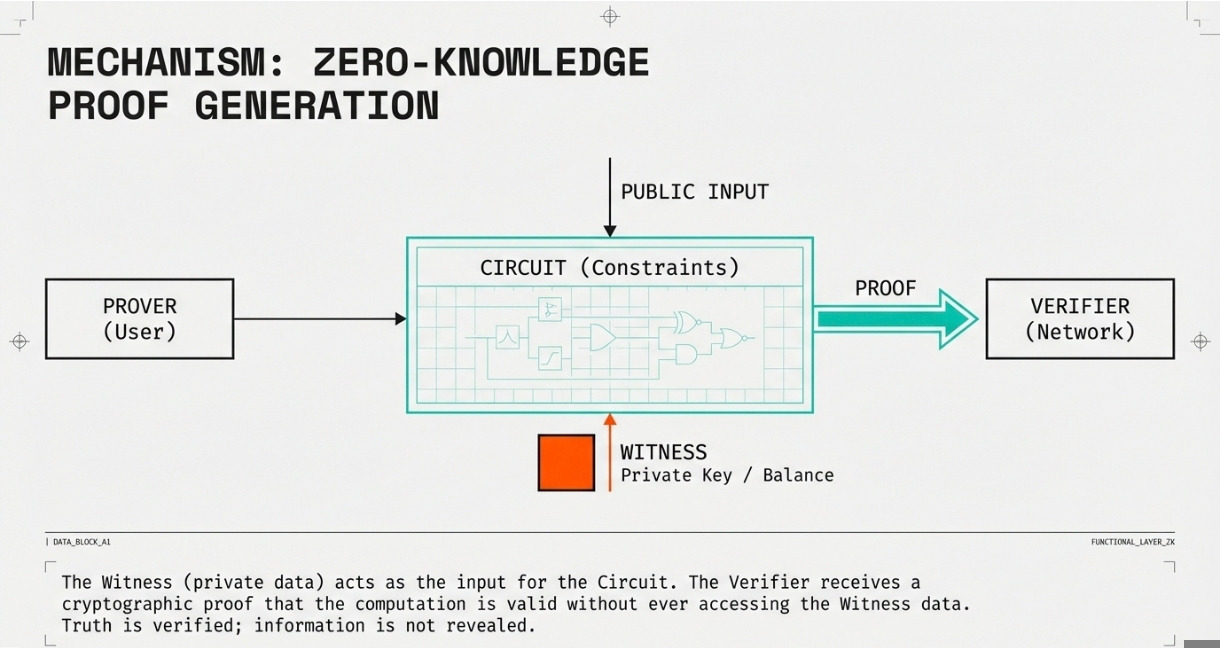
The prover is the party who wants to prove they possess certain knowledge or have performed a computation correctly. In DeFi contexts, this is typically the user wanting to show they have sufficient funds for a transaction or have executed a trade properly without revealing their balance or position.
The verifier is the entity that checks the proof's validity. In blockchain applications, this is often the network itself or a smart contract that must verify the proof before executing subsequent actions. The verifier only receives the proof, not the underlying data.
The witness represents the private information that the prover knows but doesn't want to reveal. This could be a private key, account balance, or specific transaction parameters. The witness serves as the input to the computation that generates the proof.
The circuit is the set of constraints that define the computation being proven. Circuits are typically represented as arithmetic circuits that can be compiled into the format required by specific proof systems. Designing efficient circuits is crucial for minimizing computational costs and gas fees.
❍ Anonymity Set Construction and Management
Privacy in these systems depends heavily on the concept of anonymity sets. The anonymity set refers to the group of possible originators of a transaction. Larger anonymity sets provide stronger privacy guarantees because it becomes statistically more difficult to identify the actual source.
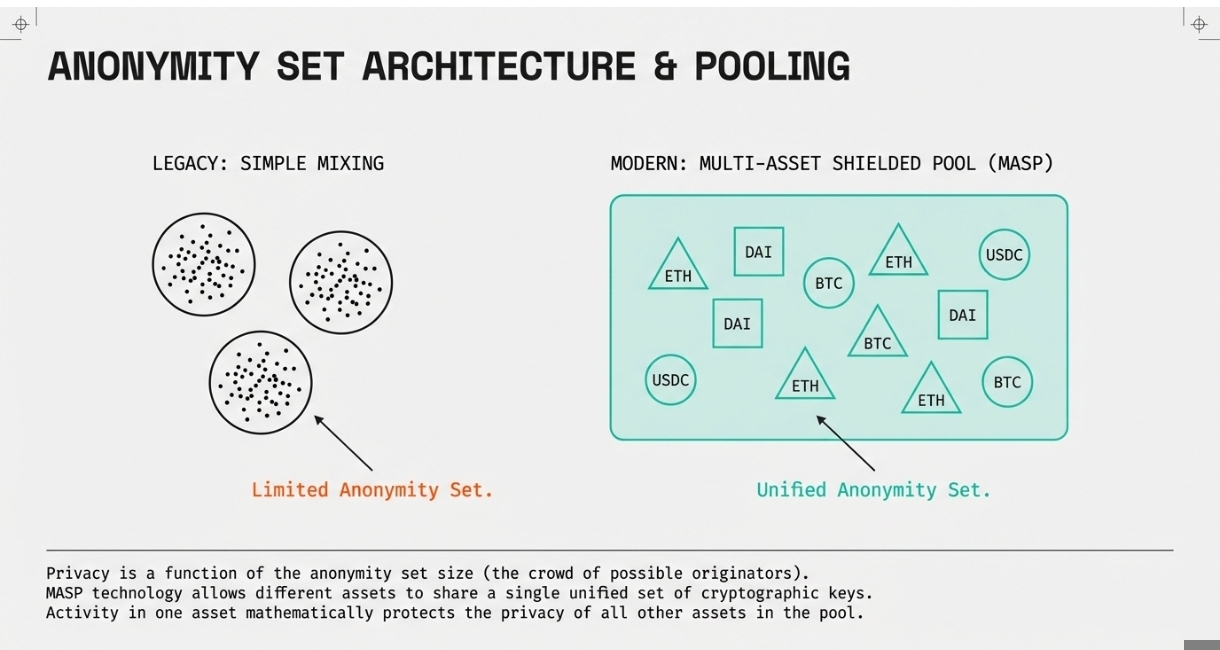
Protocols employ various techniques to expand anonymity sets. Some use time-based pooling where transactions are batched together, making it harder to link specific inputs and outputs. Others implement constant-sized pools where assets are fungible within the pool, similar to how cash in a vault becomes co-mingled.
Advanced protocols like Namada implement multi-asset shielded pools (MASP) that allow different assets to share the same anonymity set. This cross-asset privacy significantly expands the anonymity set beyond what would be possible with single-asset pools, enhancing privacy for all participants.
❍ Gas Optimization Techniques
Privacy transactions traditionally required more computational resources than transparent transactions, leading to higher gas costs. Several optimization techniques have emerged to address this challenge.
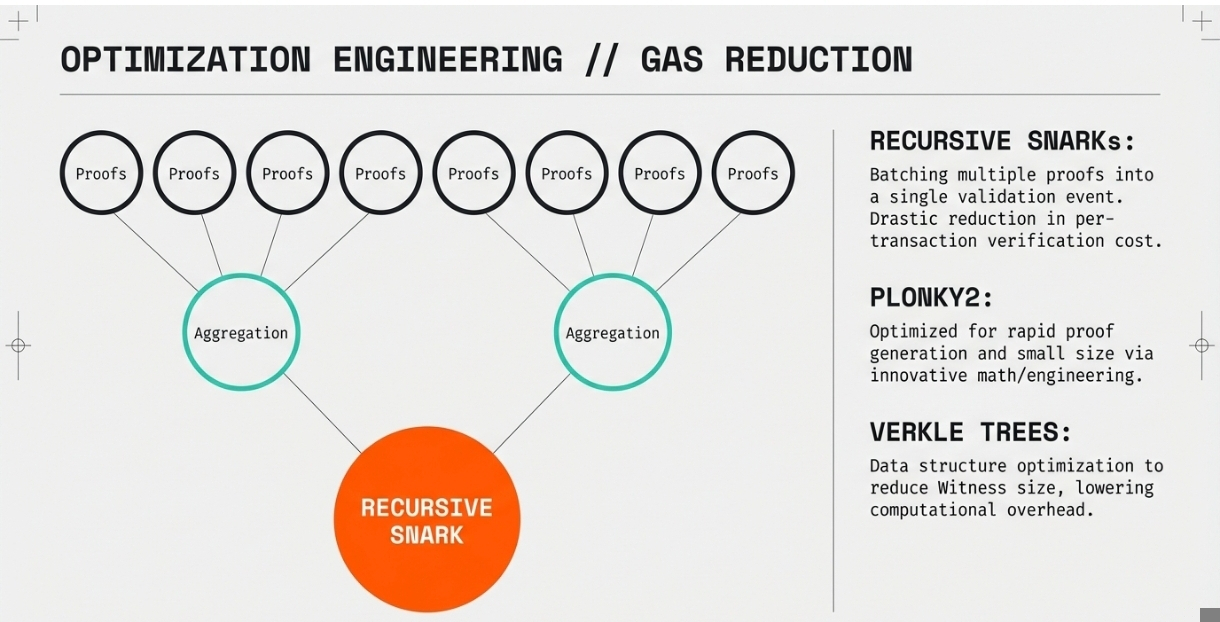
Recursive SNARKs allow multiple proofs to be combined into a single proof that verifies all underlying computations. This technique enables batching of multiple transactions into a single proof, dramatically reducing the per-transaction verification cost. The resulting aggregate proof can be verified much more efficiently than verifying each individual proof separately.
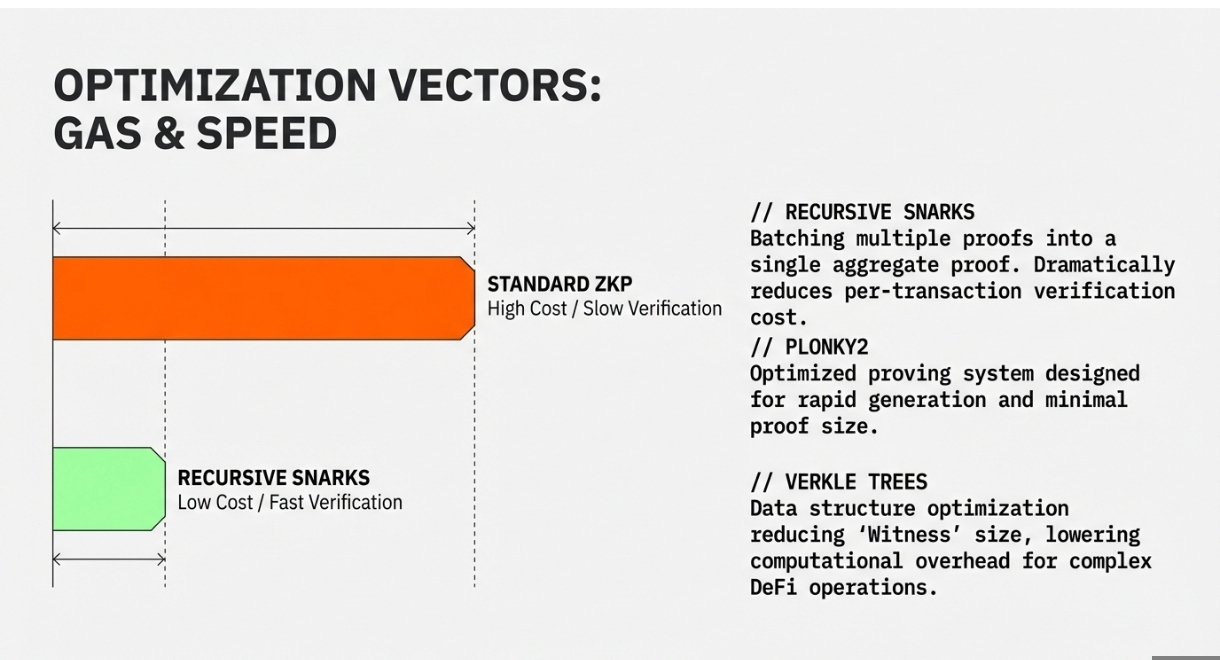
Plonky2 and similar proving systems optimize for rapid proof generation and verification. These systems use innovative mathematical approaches and engineering optimizations to reduce both proof generation time and proof size. The efficiency gains make privacy-preserving transactions economically viable for everyday use.
Verkle trees and other advanced data structures help reduce the witness size required for proofs. Smaller witnesses mean less data needs to be processed during proof generation, lowering computational requirements and gas costs. These optimizations are particularly important for complex DeFi operations that involve multiple steps or conditions.
IV. Top 5 Privacy-Preserving Protocols
1. Railgun: Private Ethereum DeFi Integration
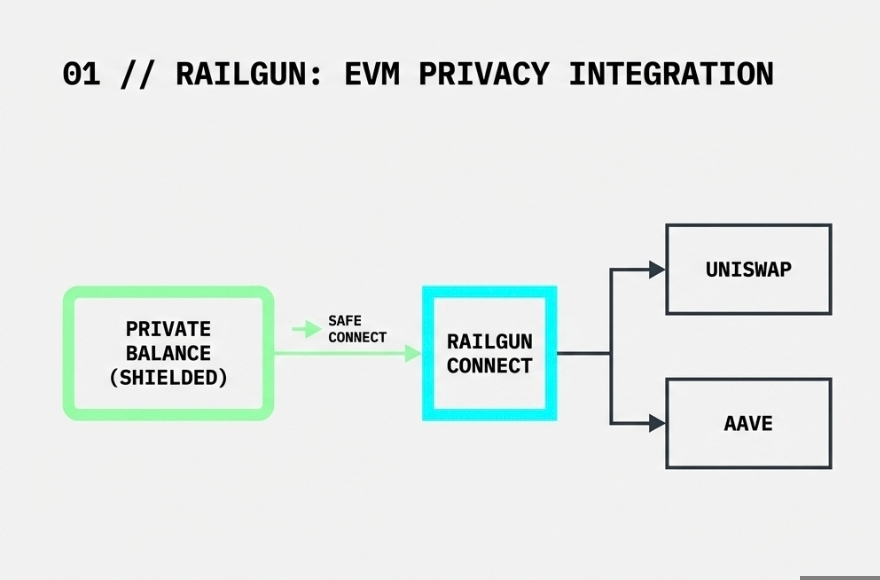
Railgun has emerged as a leading privacy solution for Ethereum-based DeFi. Unlike earlier privacy systems that required users to withdraw funds from privacy pools to use DeFi applications, Railgun's breakthrough Railgun_connect technology enables direct interaction with DeFi protocols from private balances.
The system leverages zk-SNARKs to create shielded transactions that hide sender, receiver, and amount while still allowing the transactions to interact with standard DeFi smart contracts. Users can engage with protocols like Uniswap, Aave, and Compound without revealing their strategies or positions to competitors or front-running bots.
Recent data shows impressive adoption growth, with daily shields reaching a record 326 in early 2026 and cumulative volume hitting $4.5 billion, representing nearly 100% year-over-year growth. The protocol maintains approximately 7,000 tokenholders with healthy distribution, though staking contracts concentrate about 74% of the supply.
Railgun's approach represents the practical application of privacy technology to existing DeFi ecosystems rather than creating separate privacy-focused chains. This compatibility-focused strategy allows users to maintain their existing workflows while adding privacy protection where needed.
2. Aztec Network: ZK-ZK-Rollup Architecture
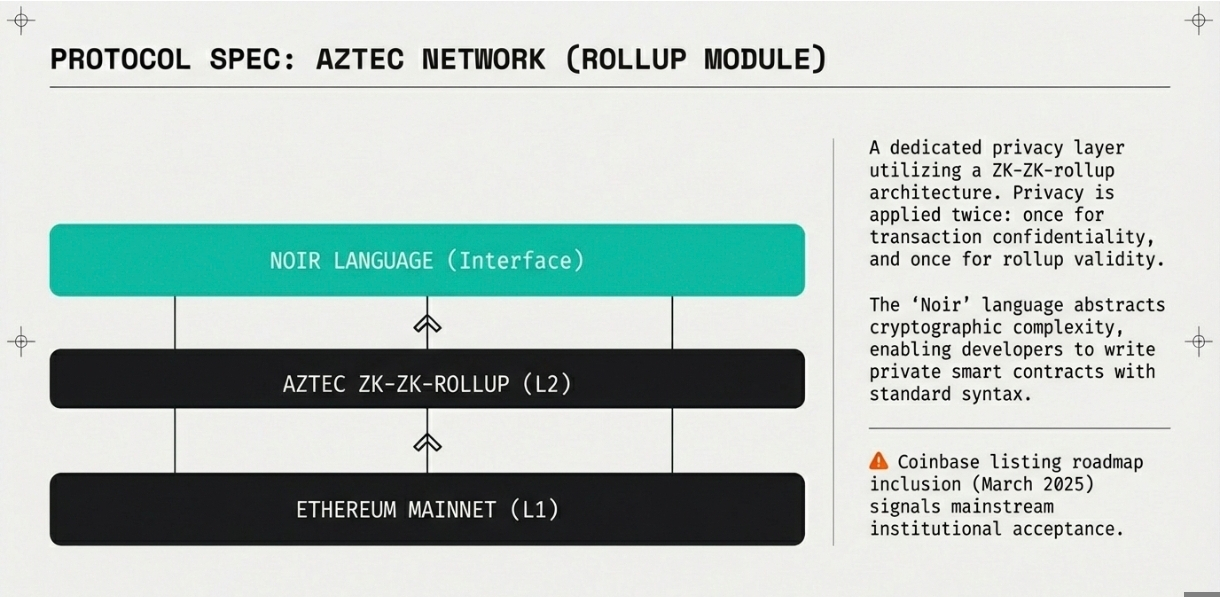
Aztec Network takes a comprehensive approach to privacy by building a dedicated zk-rollup with privacy as a core feature. Their innovative ZK-ZK-rollup architecture applies zero-knowledge proofs at two levels: for transaction privacy and for rollup validity.
The network's Noir programming language enables developers to write privacy-preserving smart contracts using a familiar syntax. Noir abstracts away much of the complexity of zero-knowledge cryptography, making it accessible to developers without specialized cryptography expertise. This developer-friendly approach accelerates ecosystem development and application diversity.
Aztec's hybrid model allows users to choose between public and private transactions within the same network. This flexibility enables applications that require some transparent components while keeping sensitive operations private. The system also includes compliance features that allow for selective disclosure when necessary for regulatory requirements.
The protocol has gained significant attention, with Coinbase adding AZTEC to its listing roadmap in March 2025. This exchange recognition signals growing mainstream acceptance of privacy technologies that incorporate compliance mechanisms rather than providing absolute anonymity.
3. Zama: Fully Homomorphic Encryption Revolution
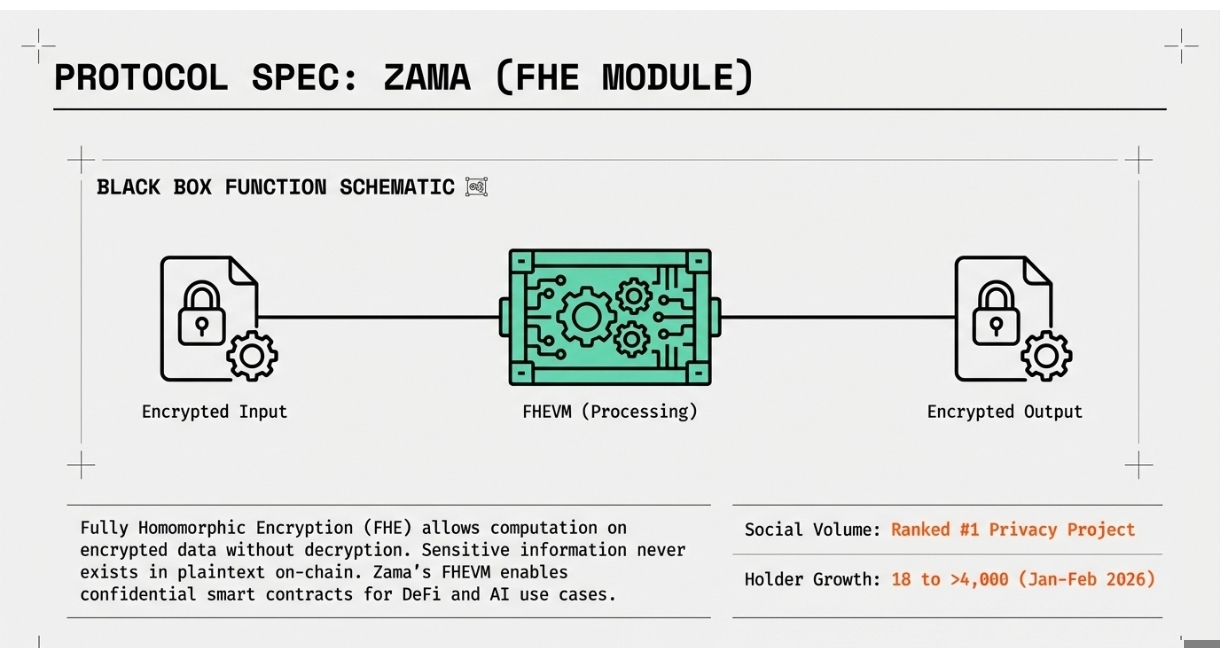
Zama represents a fundamentally different approach to blockchain privacy using Fully Homomorphic Encryption (FHE). While zero-knowledge proofs verify computations without revealing inputs, FHE allows computations to be performed directly on encrypted data.
The company's FHEVM (Fully Homomorphic Encryption Virtual Machine) enables confidential smart contracts that maintain data encryption throughout execution. This means sensitive information never exists in plaintext on-chain, not even during processing. The system supports general-purpose computations while preserving confidentiality.
Zama has generated significant developer interest and social mindshare, recently ranking as the top privacy project by social discussion volume. Their open-source cryptography tools, including TFHE-rs and Concrete, provide the foundation for building applications with end-to-end encryption.
The protocol has seen remarkable holder growth, increasing from 18 tokenholders on January 26, 2026, to over 4,000 by early February. This rapid adoption reflects strong interest in FHE technology and its potential applications beyond DeFi to areas like artificial intelligence and confidential data processing.
4. Secret Network: Trusted Execution Environment Approach
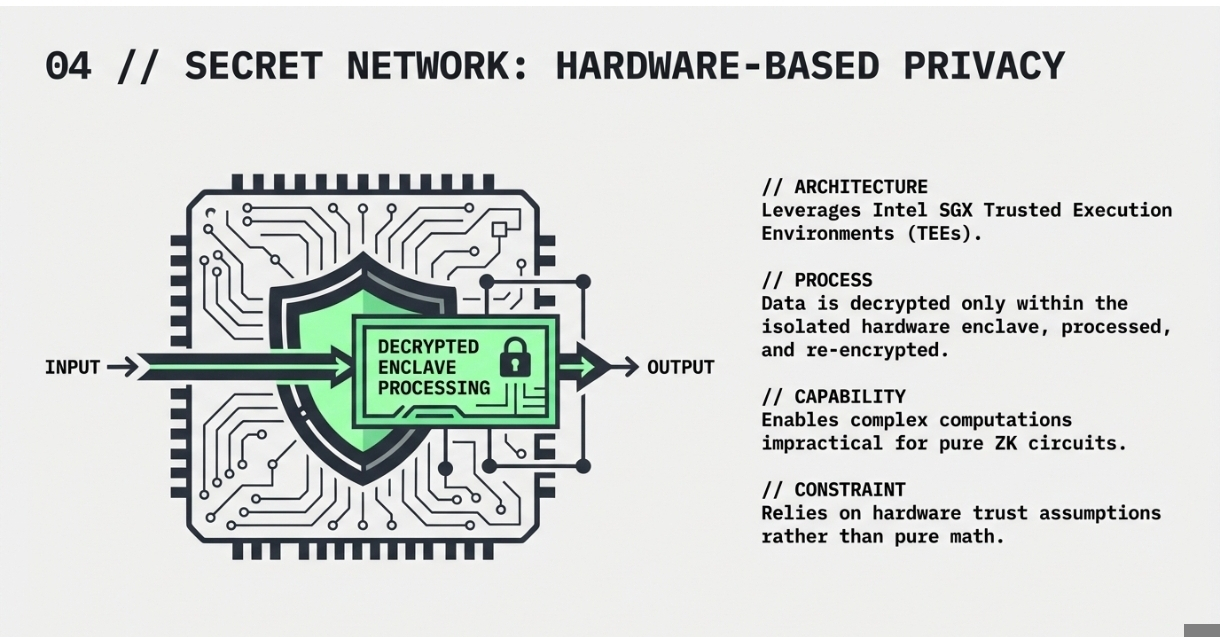
Secret Network implements privacy through Trusted Execution Environments (TEEs), specifically using Intel's SGX technology. TEEs create secure enclaves within processors where code can be executed in isolation from the main operating system, protecting it from observation or tampering.
This hardware-based approach allows smart contracts to process encrypted data by decrypting it only within the secure enclave. The computation results are then re-encrypted before being written to the blockchain. This model provides strong confidentiality guarantees backed by hardware security features.
The network enables private computations for various use cases, including decentralized exchanges, lending protocols, and data management applications. Their approach allows for complex computations that might be impractical with pure cryptographic solutions due to computational constraints.
However, TEE-based solutions face different trust assumptions than cryptographic approaches. Users must trust that the hardware manufacturers have properly implemented the security features and that no vulnerabilities exist in the specific processor models being used. This trade-off between practical efficiency and trust minimization represents a key consideration for protocol selection.
5. Namada: Multi-Asset Shielded Pool Innovation
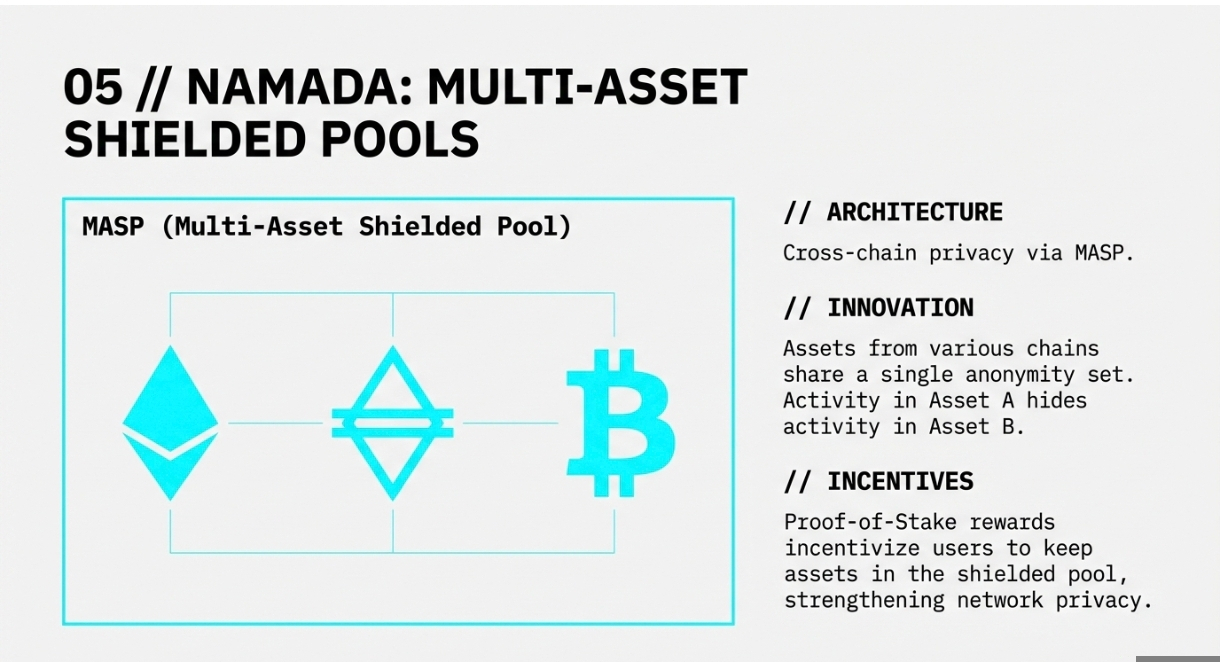
Namada introduces a novel approach to cross-chain privacy through its Multi-Asset Shielded Pool (MASP) technology. Unlike single-asset privacy pools, MASP allows different types of assets to share the same anonymity set, significantly enhancing privacy for all participants.
The protocol uses a unified set of cryptographic keys for all assets within the shield pool. This design means that activity with one asset contributes to the anonymity of all other assets in the pool. The larger combined anonymity set provides stronger privacy guarantees than would be possible with separate single-asset pools.
Namada implements a proof-of-stake consensus mechanism with inflation rewards designed to incentivize participation in the shielded ecosystem. These incentives encourage users to maintain assets in shielded form, further expanding the anonymity set and enhancing network privacy for all participants.
The protocol focuses on interoperability, allowing assets from various blockchains to benefit from its privacy features. This cross-chain approach recognizes that privacy needs often span multiple ecosystems and that siloed privacy solutions provide limited protection in an interconnected DeFi landscape.
V. Privacy 2.0: Programmable Compliance and Future Directions
The evolution from Privacy 1.0 to Privacy 2.0 represents a fundamental shift from adversarial anonymity to programmable compliance. Early privacy technologies often positioned themselves in opposition to regulatory frameworks, leading to conflicts and limitations in their adoption and utility.
Modern privacy protocols incorporate compliance features at the protocol level. Technologies like view keys allow users to selectively disclose transaction details to authorized parties while keeping them hidden from the general public. This approach mirrors traditional banking privacy, where financial institutions maintain confidentiality while providing necessary information to regulators.
The concept of programmable compliance extends beyond simple disclosure mechanisms. Advanced systems can implement complex rulesets that automatically enforce regulatory requirements. For example, protocols can integrate real-time sanctions list checking or transaction amount limits while preserving privacy for compliant transactions.
This compliance-friendly approach has garnered institutional interest, with major financial technology firms like Circle and Paxos planning to issue private, compliant stablecoins on privacy-focused networks. These developments signal a growing recognition that privacy and regulation can coexist when designed with both considerations in mind.
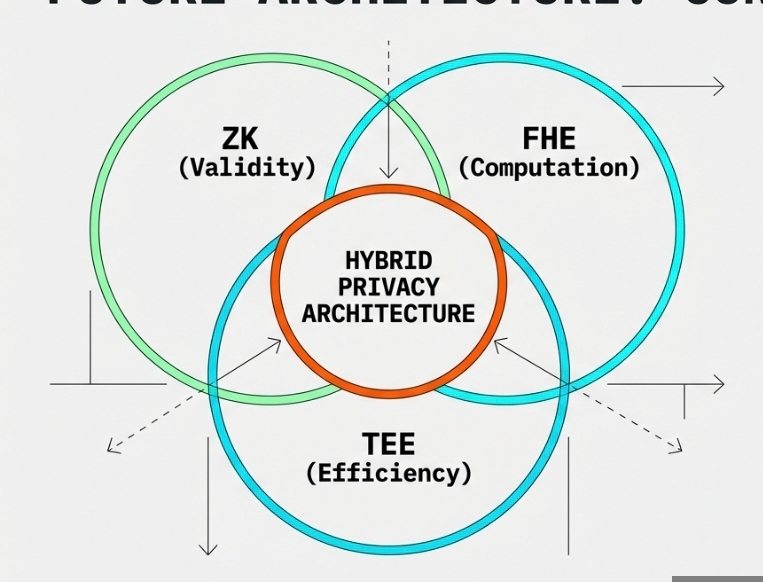
The future of privacy-preserving DeFi likely involves hybrid approaches that combine the strengths of different technologies. ZKPs might handle transaction privacy while FHE enables confidential computation, with TEEs providing efficient execution for certain operations. This technological diversity will allow developers to choose the right privacy solution for each specific application requirement.
As the ecosystem matures, we can expect increased standardization and interoperability between different privacy protocols. Cross-protocol privacy preservation will become increasingly important as users interact with multiple chains and applications. The ultimate goal remains providing users with control over their financial privacy while maintaining the transparency and verifiability that make blockchain technology valuable.

