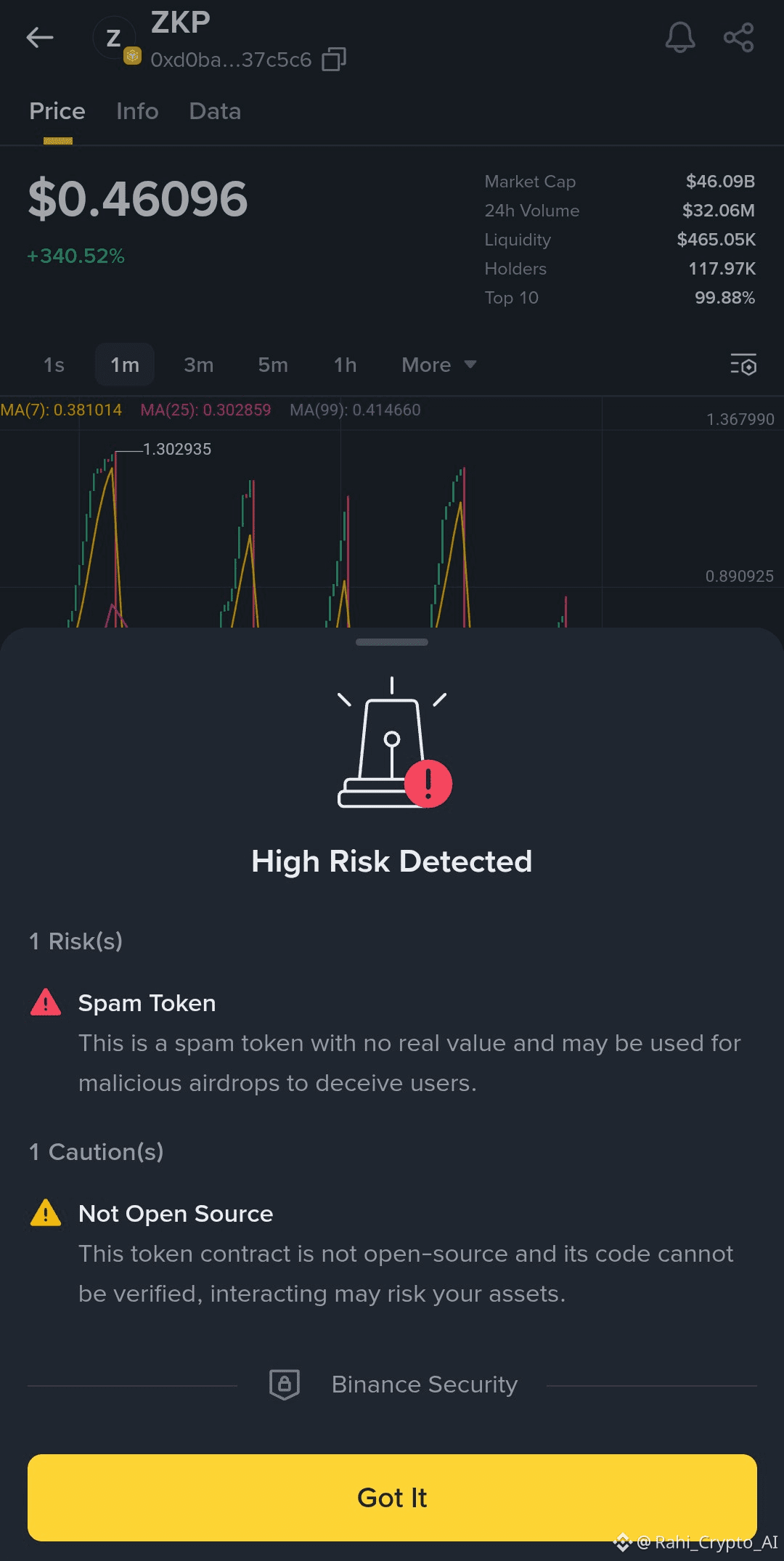
In the rapidly evolving world of cryptocurrency, users are increasingly encountering spam tokens—digital assets that have no real value and are often distributed through malicious airdrops. These tokens are not legitimate investments; instead, they are commonly used as tools to deceive users and expose them to scams, phishing attacks, and financial losses.
What Are Spam Tokens?
Spam tokens are cryptocurrencies that appear in users’ wallets without being requested or purchased. They often have:
No real utility or development team
No legitimate market demand or liquidity
Misleading names resembling popular tokens or projects
Their sudden appearance is usually intentional and designed to trigger curiosity or panic.
How Malicious Airdrops Work
Malicious actors distribute spam tokens through airdrops to thousands of wallet addresses. Once the token appears, users may:
Search for its value
Attempt to trade or “claim” rewards
Visit a website linked in the token’s description
These actions can lead to dangerous outcomes, including:
Wallet-draining smart contracts
Phishing websites that steal private keys
Approval scams that grant attackers control over funds
In many cases, simply interacting with the token or its associated contract can compromise the entire wallet.
Common Red Flags
Be cautious if a token:
Appears in your wallet without consent
Promises guaranteed profits or rewards
Requires connecting your wallet to an unknown website
Has no verifiable project website, whitepaper, or social presence
Legitimate projects do not rely on deceptive tactics to attract users.
Why Spam Tokens Have No Real Value
Spam tokens are typically created at near-zero cost and with no intention of long-term development. Any displayed price may be artificially generated or manipulated to lure victims. In reality, these tokens:
Cannot be safely sold
Have no sustainable liquidity
Exist solely as bait for scams
How to Protect Yourself
To stay safe:
Do not interact with unknown tokens
Never connect your wallet to unverified websites
Revoke suspicious token approvals regularly
Use separate wallets for testing or airdrops
Rely on trusted sources for airdrop announcements
Ignoring spam tokens is often the safest action.
Conclusion
Spam tokens and malicious airdrops are a growing threat in the crypto ecosystem. While they may look harmless or even enticing, they carry significant risk and no real value. Education, caution, and skepticism are essential tools for protecting your assets in a decentralized environment.
Staying informed is the first step toward staying secure.

