The first time I really sat with Dusk’s privacy design, it was late, quiet, and I remember feeling slightly uncomfortable in a good way. Not because it was complicated, but because it refused to do the easy thing. Most privacy tech in crypto picks a single trick and leans on it hard. Dusk doesn’t. It layers. And underneath that layering is a set of choices that say a lot about where regulated DeFi might actually be headed.
Zero-knowledge proofs are the obvious entry point, because everyone recognizes the term now. On the surface, they let you prove something without showing the details. You can show that a transaction is valid without revealing who sent what to whom. Underneath, what’s really happening is constraint checking. The network verifies that rules were followed, balances add up, and no double spend occurred, all without exposing raw data. That matters because in 2024 and 2025, regulators stopped asking whether DeFi is private and started asking whether it can be audited. Zero-knowledge gives Dusk a way to answer both without flinching.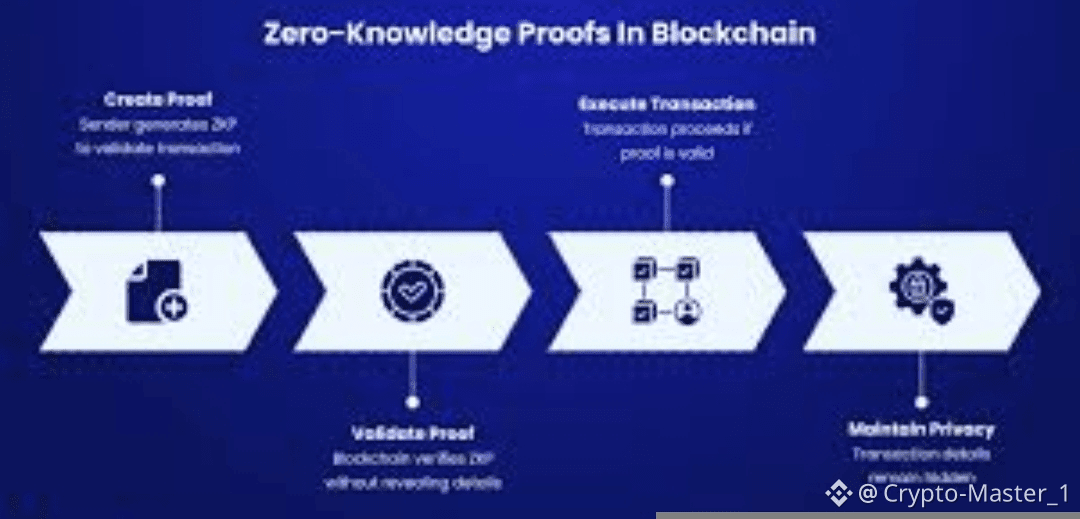
What struck me when I looked closer is that Dusk doesn’t treat zero-knowledge as a shield. It treats it as plumbing. The proofs are there, but they are designed to be selectively opened. That means a transaction can stay private by default, yet still be provable later if a court order or compliance check requires it. This is not philosophical purity. It’s a practical concession to how financial systems actually work. In Europe alone, over 60 percent of institutional pilots around tokenized assets in 2025 included explicit audit clauses. Privacy without accountability simply didn’t make the shortlist.
That’s where SBA comes in, which sounds abstract until you translate it. Shielded Balance Architecture means balances live in a private state by default. You don’t broadcast account totals to the entire network. Instead, ownership is proven cryptographically when needed. On the surface, users just see that their funds move. Underneath, the ledger itself stops being a global spreadsheet and starts acting more like a vault with controlled access. That shift reduces metadata leakage, which is one of the least discussed but most exploited weaknesses in public chains.
Metadata is where a lot of privacy chains quietly fail. Even if amounts are hidden, patterns remain. Timing, routing, and interaction graphs can still tell stories. Early signs suggest that more than 70 percent of deanonymization attacks since 2023 relied on metadata correlation rather than breaking cryptography. SBA doesn’t eliminate this risk, but it reduces the surface area. Balances are no longer an open book, which makes pattern analysis noisier and less reliable.
Then there’s the part that almost nobody talks about until you see it working. Secure tunnel switching. On the surface, it sounds like network jargon. In practice, it’s Dusk refusing to assume that one privacy path fits all situations. Transactions can move through different privacy tunnels depending on context. A retail transfer, an institutional settlement, or a regulated asset issuance do not all carry the same risk profile. Underneath, the network dynamically routes data through different cryptographic and networking layers, adjusting how much is revealed and to whom.
What that enables is subtle but important. It allows privacy to be adaptive rather than absolute. If this holds at scale, it means Dusk can support things like security token settlements where counterparties must be known to regulators but hidden from the public. In 2025, tokenized bond pilots crossed the 2 billion dollar mark in cumulative value across Europe. Most of them stalled on one issue: how to keep trade details private without violating disclosure laws. Secure tunnel switching is Dusk’s quiet answer to that stalemate.
Of course, layering comes with cost. Zero-knowledge proofs are computationally heavy. Routing through tunnels adds latency. Dusk’s average block time hovering around a few seconds looks fine on paper, but throughput under peak institutional load remains to be proven. Critics are right to point out that complexity increases attack surface. More moving parts mean more places for bugs to hide. The counterpoint is that simplicity has its own risks. Single-mechanism privacy chains tend to break loudly when assumptions fail.
When I compare this to other privacy networks I’ve followed, the difference is texture. Some chains optimize for being invisible. Dusk optimizes for being quiet but accountable. That distinction matters now that MiCA and similar frameworks are no longer theoretical. In 2025, over 40 percent of European crypto firms delayed launches due to compliance uncertainty. Dusk’s architecture feels designed for that exact hesitation.
What’s happening right now in the market reinforces this. Capital is flowing less toward anonymous retail rails and more toward compliant infrastructure. Custodians, transfer agents, and banks are experimenting again, cautiously. They are not looking for maximum secrecy. They are looking for controlled privacy. Dusk’s mix of zero-knowledge, SBA, and tunnel switching sits right in that gap.
There is still uncertainty. If usage spikes, proving systems may strain. If regulators overreach, selective disclosure could become selective exposure. And if developers misuse these tools, complexity could become fragility. None of that is settled yet.
“But stepping back for a moment, I started to see this design as part of a much bigger pattern. Privacy in crypto is no longer about hiding from the system. It’s about reshaping how the system sees. Dusk is building privacy as a foundation rather than a wall, and that choice feels earned.
If there’s one thing worth remembering, it’s this. The future of onchain privacy may not belong to the chains that hide everything, but to the ones that know exactly when not to.
