Public blockchains were built on radical transparency. Every transfer, every balance change, every interaction is visible by default. That openness worked when crypto was mostly experimental capital, but it becomes a structural problem the moment real financial assets move on-chain. Stocks, bonds, and private equity cannot operate in an environment where transaction paths expose counterparties, inventory, and business strategy. For institutions, that isn’t innovation—it’s unacceptable risk.
This is the deadlock most RWA initiatives run into. On one side, regulators demand auditability, traceability, and proof of lawful behavior. On the other, issuers and investors cannot afford full disclosure of sensitive financial data. The original promise of public ledgers—trust through transparency—turns into the very reason serious capital hesitates to participate. Full disclosure stops being a feature and becomes a barrier.
Dusk’s architecture starts by rejecting the idea that transparency must be absolute. Instead of asking markets to accept exposure, it reframes the question: what actually needs to be proven for a transaction to be valid? The answer is surprisingly limited. A system only needs to confirm that inputs equal outputs, that no double spending occurs, and that the rules are followed. Everything else can remain private.
Zero-knowledge proofs sit at the center of this shift. In Dusk’s implementation, transactions generate mathematical proofs that confirm correctness without revealing amounts, identities, or flow of funds. Validators do not “see” the transaction in the traditional sense; they verify cryptographic constraints. By using the PLONK proving system combined with Pedersen commitments, sensitive values are hidden by default, while Merkle tree logic inside the Rusk virtual machine ensures state consistency. What emerges is a network where legality is provable and visibility is optional.
This changes the baseline assumption of on-chain finance. Instead of full disclosure with optional privacy, Dusk enforces privacy first and allows disclosure only when it is explicitly required. That distinction matters for regulated markets. Selective disclosure means an issuer can prove compliance without broadcasting their entire capital structure to competitors, and an institution can transact without leaving a permanent, public trail of strategic behavior.
Consensus design reinforces this philosophy. Dusk’s Proof-of-Blind Bid mechanism encrypts validator bids so stake size does not translate directly into influence. Block producers are selected from encrypted bids stored in a Poseidon-based Merkle structure, reducing predictability and limiting dominance by large actors. Within the Segregated Byzantine Agreement model, the network maintains finality as long as honest participation exceeds one third, with probabilistic failure reduced to negligible levels through iterative rounds. The result is a system that can handle institutional throughput without drifting toward centralization.
Compliance is not treated as an external add-on. It is embedded directly into the protocol. Dusk’s Zedger model stores private account state transitions in sparse Merkle trees, allowing issuers to generate targeted proofs for regulators. Instead of handing over full transaction histories, entities can disclose exactly what is required—nothing more, nothing less. View keys and custom zero-knowledge proofs allow regulators, auditors, or counterparties to inspect specific details while the rest of the network remains blind. This avoids the regulatory dead ends faced by fully anonymous chains and the data leakage inherent in public ones.
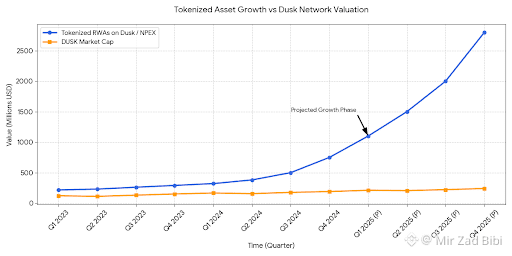
These ideas are not confined to theory. Dusk’s collaboration with the regulated Dutch exchange NPEX has already led to the tokenization of hundreds of millions of euros in securities, including equity and bonds. Settlement logic is bridged on-chain using external data streams, and the asset pool is expected to expand further as the network matures. This creates a closed loop where issuance, trading, and settlement occur under a unified privacy and compliance framework rather than being fragmented across systems.
Under the hood, the modular stack—Rusk VM, Zedger, and DuskEVM—allows developers to deploy privacy-preserving contracts without abandoning existing tooling. WebAssembly support enables native zero-knowledge verification, reducing friction for builders. The Phoenix model, based on UTXO-style encrypted notes and nullifiers, breaks transaction graph analysis while still preventing double spending. Unlike systems that chase anonymity for its own sake, Dusk reconstructs ownership and balance logic in a way regulators can reason about.
From a valuation perspective, the network sits in an unusual position. With a market capitalization that remains modest relative to the scale of assets already piloted on-chain, its upside is tied less to narrative cycles and more to whether institutional adoption continues to materialize. If tokenized asset volumes grow and settlement activity follows, network effects compound naturally. That said, risks remain. Privacy infrastructure attracts regulatory scrutiny, and cross-chain components introduce potential attack surfaces. Staking economics must continue to align with security assumptions, especially under stress.
What makes Dusk interesting is not that it promises secrecy, but that it formalizes discretion. By moving from unconditional transparency to programmable, selective disclosure, it resolves a contradiction that has stalled RWA adoption for years. This is not a showcase of cryptography for its own sake. It is an attempt to encode the unwritten rules of financial markets—confidentiality, auditability, and trust—directly into the ledger itself.
In that sense, Dusk is less about disrupting finance and more about making distributed settlement usable for it. If regulated on-chain markets are to scale, they will not be built on exposure, but on controlled visibility. Dusk’s zero-knowledge framework offers a coherent path toward that outcome, one where privacy and compliance are not competing forces but complementary properties of the same system.

