Context and scope
Visibility events like a top venue listing can change attention patterns fast, but attention is not the same as usage. This piece treats VANRY as a governance and utility asset inside an infrastructure stack and evaluates it with a systems lens: what the chain is building, what is already live, what adoption signals exist, what the developer surface looks like, how the economic design works, and what the main risks are. Follow @undefined for primary updates.
1. What Vanar Chain is building at the base layer
Step 1: Identify the execution environment
Vanar positions itself as an EVM compatible layer one, with its public node software described as a fork of the Go Ethereum client and aligned to the broader Ethereum execution model. That matters because it reduces developer migration friction: Solidity tooling, common RPC patterns, and standard node operations are more transferable than on a novel VM.
Step 2: Confirm network accessibility for builders
The published network parameters show a single mainnet identity with Chain ID 2040, public RPC and websocket endpoints, and a public explorer URL. This is a practical adoption prerequisite because it allows wallets, indexers, and standard middleware to integrate without custom adapters.
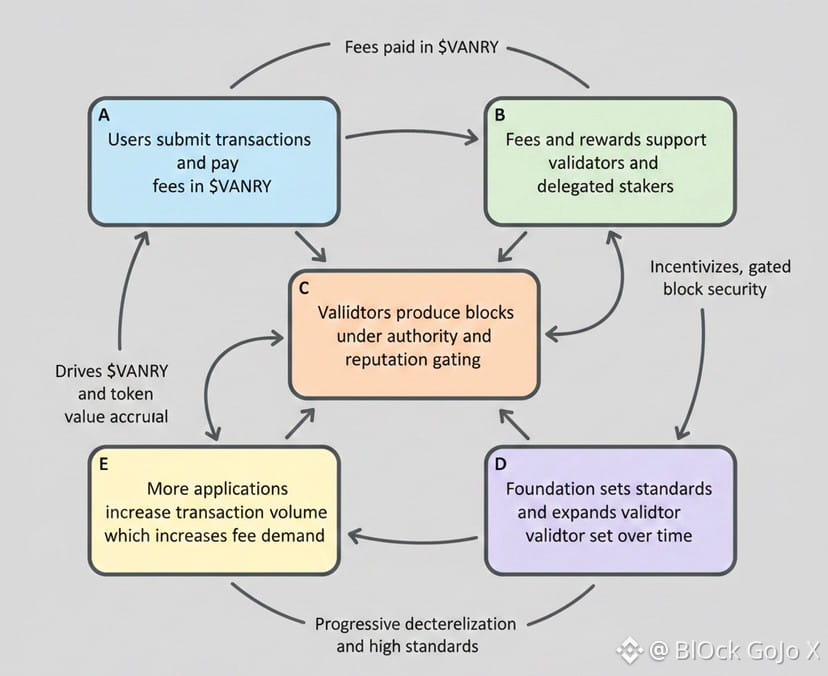
Step 3: Evaluate the consensus and validator admission design
Vanar’s documentation describes a hybrid approach where Proof of Authority is governed by Proof of Reputation, and validator onboarding is mediated through a foundation structure. The implication is straightforward: early network safety can be stronger when validators are known entities, but decentralization depends on transparent criteria and on widening the validator set over time.
2. The five layer stack and why it matters
Vanar’s public positioning is not only a chain, but a broader stack oriented toward AI workloads, described as five layers. The critical analytical question is whether these layers are shipping as product, or remaining as narrative.
Step 1: Map the layers that are explicitly named today
The stack naming visible on the public site includes Vanar Chain plus Neutron and Kayon, with Axon and Flows marked as coming soon.
Step 2: Separate base chain claims from higher layer deliverables
The base chain is measurable through RPC, explorer, staking, and node code. Higher layers require product delivery, developer APIs, and integration case studies. The existence of documentation for Neutron suggests at least a designed product surface, but several pages still read as rollout oriented rather than fully mature.

Step 1: Core infrastructure artifacts that exist today
1. Public documentation hub describing the chain and builder entry points
2. Public node implementation repo with build instructions and dependency requirements
3. Public mainnet connection details and explorer reference
4. Public staking interface, implying an operational validator reward loop
Step 2: Governance structure artifact
The documentation describes a foundation with roles spanning governance oversight, validator selection via Proof of Reputation, ecosystem support, and grants. This is a centralization sensitive area, but it is also a concrete structure that can coordinate early network phases.
4. Adoption signals that matter more than follower counts
Adoption is best measured by usage, not visibility. Without doing full on chain analytics here, there are still indirect signals that can be evaluated logically.
Signal A: Integration readiness
If a chain offers stable RPC endpoints, a public explorer, and clear chain parameters, it is at least integrable by wallets and apps. Vanar provides these basics, which reduces activation energy for third party developers and tooling providers.
Signal B: Token as an operational necessity
When the native asset is required for transaction fees and is also used for staking and validator rewards, organic demand is linked to usage intensity. Vanar’s docs explicitly state gas fee utility plus staking and validator reward roles.
Signal C: Interoperability bridge surface
Docs describe a wrapped representation of the native token on other major EVM networks with a bridge connecting native and wrapped forms. That increases potential liquidity routing and app composability, but it also introduces bridge security as a primary risk surface.
5. Developer trends and what to watch next
Developer traction is rarely captured by slogans. It shows up as documentation quality, repo activity, and programs that create repeatable onboarding.
Step 1: Codebase positioning
The node repo frames the chain as EVM compatible and based on the Go Ethereum codebase, with standard build paths. This indicates the team is using a well understood engineering substrate, which can speed iteration and auditing compared with novel client code.
Step 2: Builder program footprint
A separate public organization exists for a builders program, which is a common mechanism for seeding early apps and tooling. The key evaluation metric is not the program name, but whether it results in maintained repos, deployed contracts, and active contributors months after cohorts end.
Step 3: Higher layer developer surface
Neutron documentation introduces concepts like Seeds and semantic search over connected data sources. If this becomes a stable SDK with clear APIs and pricing assumptions, it could differentiate the stack. If it remains an aspirational layer, it becomes a distraction that dilutes focus from base chain reliability.
6. Economic design of VANRY as a governance token
A useful way to analyze token design is to separate necessity, incentives, and control rights.
Step 1: Necessity
The native token is described as the gas asset for transactions and smart contract operations. This is the most defensible demand driver because it is usage coupled.
Step 2: Incentives
Staking is positioned as a mechanism that supports validators and shares rewards. Whitepaper language ties staking and delegation to network security and aligns validator and delegator incentives.
Step 3: Control rights and governance reality
Governance can be formal in token mechanics but informal in practice if validator admission and protocol direction sit largely with a central body. The foundation is described as setting direction and standards, and governing validator eligibility via reputation. The research question investors should ask is how governance evolves from foundation led to community accountable, and what on chain or off chain checks exist.
7. Challenges and open risks
8. Decentralization trajectory risk
A reputation gated authority model can be pragmatic early, but it must publish transparent selection criteria, clear dispute processes, and measurable milestones for validator expansion. Otherwise, governance premium can compress because control rights are perceived as weak.
9. Bridge and wrapped asset risk
Any bridge introduces smart contract risk and operational risk. If the wrapped asset becomes a major liquidity venue, the bridge becomes system critical. The right framework is to assume the bridge is a primary attack surface and evaluate security posture accordingly.
10. Product execution risk in the AI layers
The stack differentiator depends on shipping Neutron and Kayon as dependable primitives. Documentation shows ambition and conceptual framing, but markets tend to discount promises until APIs, throughput, cost, and privacy guarantees are demonstrated in production at scale.
11. Clarity in economic policy
For long term valuation, supply policy, emission schedule, and validator reward tuning need to be easy to audit. When these variables are opaque or frequently changed, it raises the discount rate applied by sophisticated participants.
12. Future outlook and what would change the thesis
A grounded outlook does not predict price. It defines conditions that would justify revising an assessment.
Upside conditions
1. Stable developer adoption on the base chain measured by persistent contract deployments and active addresses
2. A visibly expanding validator set with transparent reputation criteria and governance accountability
3. Neutron shipping as a usable SDK with clear enterprise and Web3 integration patterns
4. Evidence that application teams choose the stack for reasons beyond low fees, such as data primitives and compliance tooling
Downside conditions
1. Validator set remains narrow with limited community influence on protocol direction
2. Bridge becomes a bottleneck or a security incident risk that dominates perception
3. AI layers remain largely roadmap items, leaving the project competing mainly on generic EVM characteristics
Closing view
The most defensible way to track VANRY is to treat it as a usage coupled utility and governance instrument whose value ultimately depends on two execution lines: base chain reliability and the delivery of differentiated higher layers. If both lines progress with measurable artifacts, governance tokens can graduate from attention driven to fundamentals driven.
