Where Infrastructure Wins Quietly
A recurring pattern in crypto infrastructure is that popularity and positioning diverge. Popularity shows up as short term attention, social velocity, and crowded narratives. Positioning is slower. It is about whether a network is built to satisfy a specific set of constraints that real users actually have, especially users who cannot tolerate ambiguous settlement, opaque compliance boundaries, or fragile privacy assumptions.
This is the lens that best explains the strategic posture of Dusk today. Instead of optimizing for the widest possible developer surface area first, the project has leaned into a narrower target domain where privacy, auditability, and regulated asset flows can coexist. That choice reduces immediate viral spread, but it may improve long run defensibility if the market continues to move toward asset tokenization, identity constrained finance, and institution compatible rails.
This analysis walks step by step through the technical base, ecosystem signals, developer activity, economic design, open challenges, and what to monitor next.
Section 1 Why positioning beats popularity in infrastructure
Infrastructure networks tend to be judged on noisy metrics early, like community size and short term liquidity. Those metrics matter, but they are not the core selection criteria when an infrastructure network is used for assets that come with legal constraints, audit requirements, and reputational risk.
For that class of use, the selection criteria shift:
1 Privacy must be selective, not absolute. Some data must be hidden, but some facts must remain provable.
2 Finality and settlement assurances matter more than peak theoretical throughput.
3 Upgrades and governance must be legible and controlled, because protocol drift becomes an operational risk.
4 Developer tooling must support predictable deployment and monitoring, not just fast prototyping.
This is where positioning comes in. A network that is positioned for these constraints can be less popular and still win meaningful adoption. Conversely, a popular network can fail to convert attention into durable usage if it cannot meet the constraints of its target users.
Dusk is implicitly making the bet that compliance oriented privacy is a durable niche that expands over time, rather than a marketing angle. That bet is visible in its core architecture choices, its documentation focus, and its economic protocol framing.
Section 2 Ecosystem updates that signal execution pace
Infrastructure investing is mostly execution tracking. The question is not whether a vision sounds right. The question is whether the project is shipping components that reduce integration cost and improve reliability.
Two updates are particularly relevant:
First, the transition into a live network phase in early 2025 is widely referenced as the point where the roadmap moved from extended test iterations into production reality.
Second, the steady stream of node and protocol releases in late 2025 indicates a focus on operational maturity rather than headline features. Recent release notes show practical additions like GraphQL pagination, metadata endpoints, and transaction data support, all of which are the kinds of changes that make infrastructure easier to integrate and operate at scale.
These are not glamorous updates. They are the substrate work that turns a protocol from a concept into a platform that other teams can depend on without constant hand holding.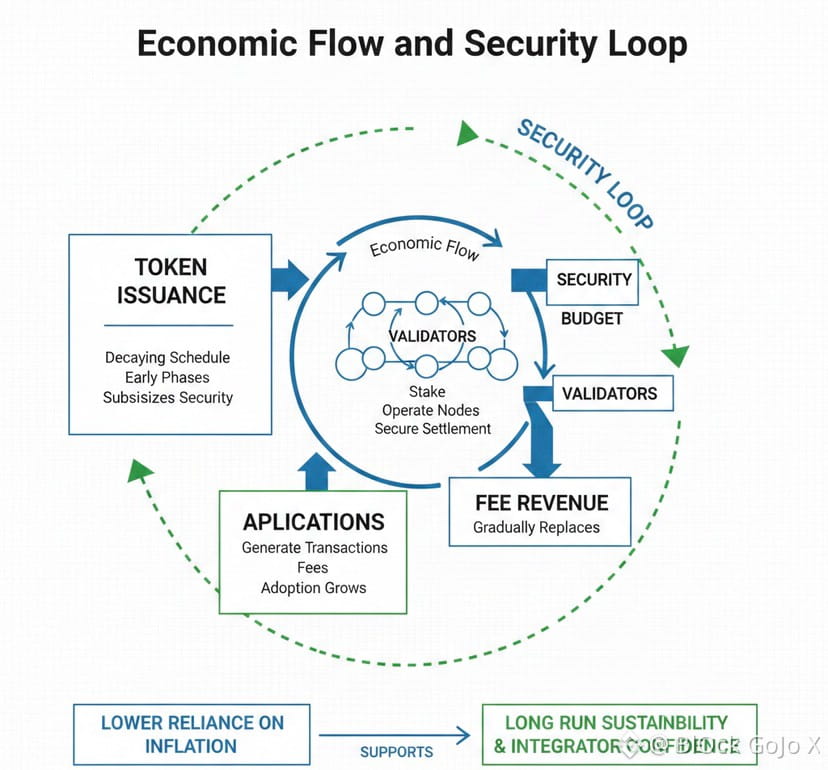
Section 3 Technical foundations and why they map to the target domain
To evaluate positioning, start with what the chain is optimized for. Dusk is built around a proof of stake model with a consensus design described as Segregated Byzantine Agreement, with participants split into distinct roles for block proposal and validation, aiming for fast settlement with statistical finality properties.
That matters because in regulated and asset heavy environments, probabilistic settlement with long reorg risk is a non starter. Statistical finality can be acceptable if the risk profile is well understood, bounded, and operationally monitored.
The second pillar is privacy with auditability. In practice, the most valuable privacy for real assets is not total opacity. It is the ability to hide sensitive fields while still proving compliance relevant facts, such as eligibility, balances, or transfer constraints. The project documentation and whitepaper framing consistently emphasize this combined privacy and programmability direction.
Step by step, the logic is:
Step 1 Real assets and identity bound finance require confidentiality for counterparties, positions, and sometimes pricing.
Step 2 The same assets require audit trails, dispute resolution hooks, and rule enforcement.
Step 3 Therefore the platform must support proof based confidentiality rather than blanket secrecy.
Step 4 That requirement shapes the VM, contract model, and the node interfaces that auditors and integrators use.
This is why it is reasonable to treat Dusk as purpose built infrastructure rather than a general narrative chain. It is also why popularity metrics can understate its potential. Broad attention usually clusters around general purpose environments, while specialized environments are adopted by teams with clearer constraints.
Section 4 Adoption signals that matter more than social volume
When a chain targets a specialized domain, adoption rarely shows up first as retail user counts. It shows up as integration behaviors.
There are several adoption signals to monitor:
Network operations signals
Look for growth in nodes that are reliably maintained, version updates that roll out without drama, and expanding operational documentation. A documentation revamp aimed at developers and node operators is a positive sign because it suggests the team is reducing friction for outsiders who want to run infrastructure.
Integration surface signals
Release notes that add query capabilities, contract metadata access, and event pagination suggest that indexers, explorers, compliance tooling, and dashboards are being treated as first class needs.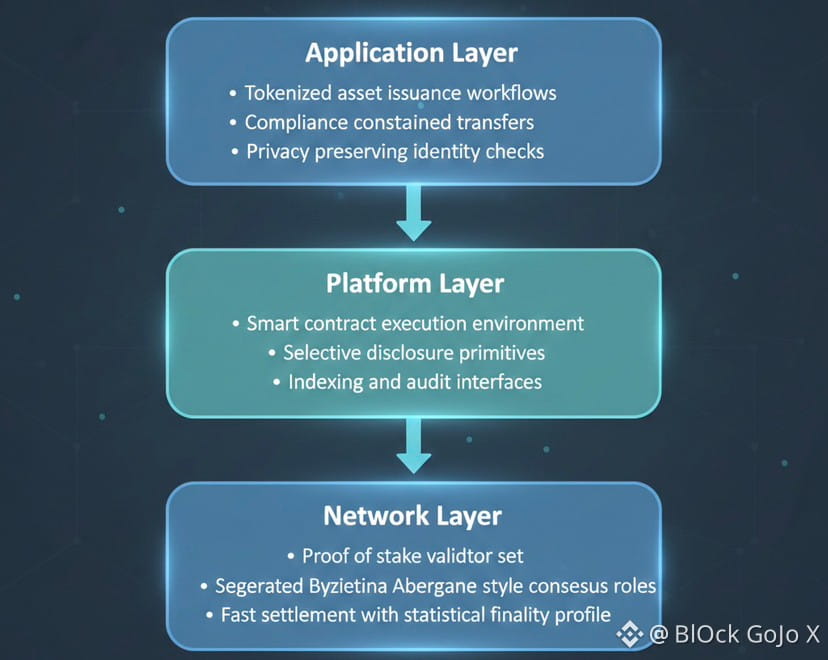
Asset and application signals
The most meaningful sign will be whether tokenization oriented applications appear with credible volume, not just pilots. If the network can support issuance, transfer restrictions, and selective disclosure, then the application layer should increasingly look like specialized asset rails rather than generalized DeFi clones.
A practical approach is to treat adoption as a ladder:
Level 1 Devs can deploy and test reliably
Level 2 Nodes and indexers run smoothly for weeks
Level 3 Applications integrate compliance friendly privacy primitives
Level 4 Real asset issuers and regulated intermediaries build repeatable processes
Level 5 Secondary markets and payments become routine, not exceptional
Most chains never climb past Level 2. The ones that do usually had the unglamorous interfaces and tooling in place early.
Section 5 Developer trends and what the codebase implies
Developer trend analysis should prioritize objective signals over sentiment. The most useful signals are release cadence, interface stabilization, and documentation clarity.
Recent core node release notes show an emphasis on:
API completeness, including endpoints for contract metadata
Indexing friendliness, including GraphQL improvements
Transaction data extensibility, suggesting future proofing for new payload types
This pattern implies that the project is currently optimizing for a stable platform layer, not just for feature announcements. That is aligned with the positioning thesis. A chain targeting institution adjacent workflows needs reliable interfaces more than it needs constant breaking innovation.
From a developer adoption standpoint, the key question is whether the platform offers:
A coherent smart contract workflow
Tooling that supports testing and deterministic builds
Operational guides that non core teams can follow
Clear economic incentives for validators and application operators
The official documentation set explicitly frames node setup, identity primitives, and an economic protocol, which indicates that the ecosystem is being shaped around repeatable building blocks rather than ad hoc apps.
Section 6 Economic design and how it supports long run security
Infrastructure economics should be read as security policy. The goal is not to make a token look attractive. The goal is to sustain validator participation, resist capture, and gradually shift from inflation reliance to usage based fees as adoption grows.
Dusk documentation describes an emission schedule based on geometric decay, with emissions reducing over fixed multi year intervals to balance ongoing issuance with inflation control.
Step by step, the economic reasoning looks like this:
Step 1 Early networks need issuance to subsidize security and bootstrap participation.
Step 2 If issuance stays high forever, the token becomes structurally inflationary and depends on constant new demand.
Step 3 A decaying schedule reduces long run dilution and forces the ecosystem to transition toward fee supported security.
Step 4 A predictable schedule also helps integrators model costs and risks, which matters for serious asset flows.
The implication is that adoption must eventually translate into meaningful fee revenue, or the network will face a gap when issuance declines. That gap is the same challenge every proof of stake network faces, but it is particularly important for a chain that wants to be trusted for high value settlement.
Section 7 The core challenges that could limit the positioning thesis
A positioning advantage only matters if it is paired with execution and ecosystem pull. The main challenges are concrete:
Challenge 1 Narrow market education
Compliance capable privacy is hard to explain without sounding like marketing. The risk is that potential builders assume the problem is either solved elsewhere or not worth solving. The remedy is reference integrations and clear technical demos that show selective disclosure and enforceable constraints in action.
Challenge 2 Developer mindshare versus general purpose ecosystems
General purpose environments have larger developer pools. Dusk will need to win by being easier for its target workflows, not by trying to out compete on breadth. That means superior docs, templates, audit tooling, and predictable runtime behavior.
Challenge 3 Liquidity and market structure
Specialized chains can struggle with deep liquidity and composability. If asset tokenization apps cannot access trading venues or bridges with acceptable risk, adoption slows. The project will need robust settlement guarantees and integration standards that reduce counterparty risk.
Challenge 4 Privacy and compliance tradeoffs
Selective privacy requires careful defaults. Too much privacy and you invite regulatory pushback. Too little and you lose the core value proposition. The platform must make it straightforward for builders to choose compliant configurations without building custom cryptography expertise.
Challenge 5 Upgrade risk
Institution adjacent users are conservative. Frequent hard changes create operational risk. A stable and well signaled upgrade process becomes a product feature, not just governance hygiene.
Section 8 Future outlook and what to monitor next
A reasonable outlook is not a price prediction. It is a checklist of conditions that would validate or falsify the positioning bet over the next several quarters.
Validation indicators
1 Continued release cadence focused on tooling, indexing, and contract interfaces, with fewer breaking changes
2 At least a small set of applications that use privacy plus auditability in a way that is visible and measurable
3 Evidence of repeated issuance and transfer workflows for tokenized assets, not just one off pilots
4 Growth in node operators and third party infrastructure providers, showing that running the network is becoming commoditized
5 Fee activity that trends upward relative to issuance, even if slowly, indicating a move toward usage supported security
Invalidation indicators
1 Long stalls in core releases or unclear roadmap execution
2 Developer tooling that remains niche and difficult to use
3 Privacy features that are either too rigid or too complex for builders to apply
4 No meaningful applications beyond internal demos
5 Economic pressure when emissions decay without compensating fee growth
If the project is positioned correctly, it should not need popularity to survive. It should need a small number of serious integrations that expand over time.
Closing note
The most defensible infrastructure tends to be the kind that looks boring while it is being built. If Dusk continues to invest in the interfaces that real asset workflows require, then its primary edge is not that it is louder than competitors. Its edge is that it is designed for constraints that will likely become more common as on chain finance matures.
For readers tracking the project, the most useful habit is to ignore short term popularity signals and instead watch whether the platform keeps reducing integration friction while real applications start using privacy with auditability as a default.
