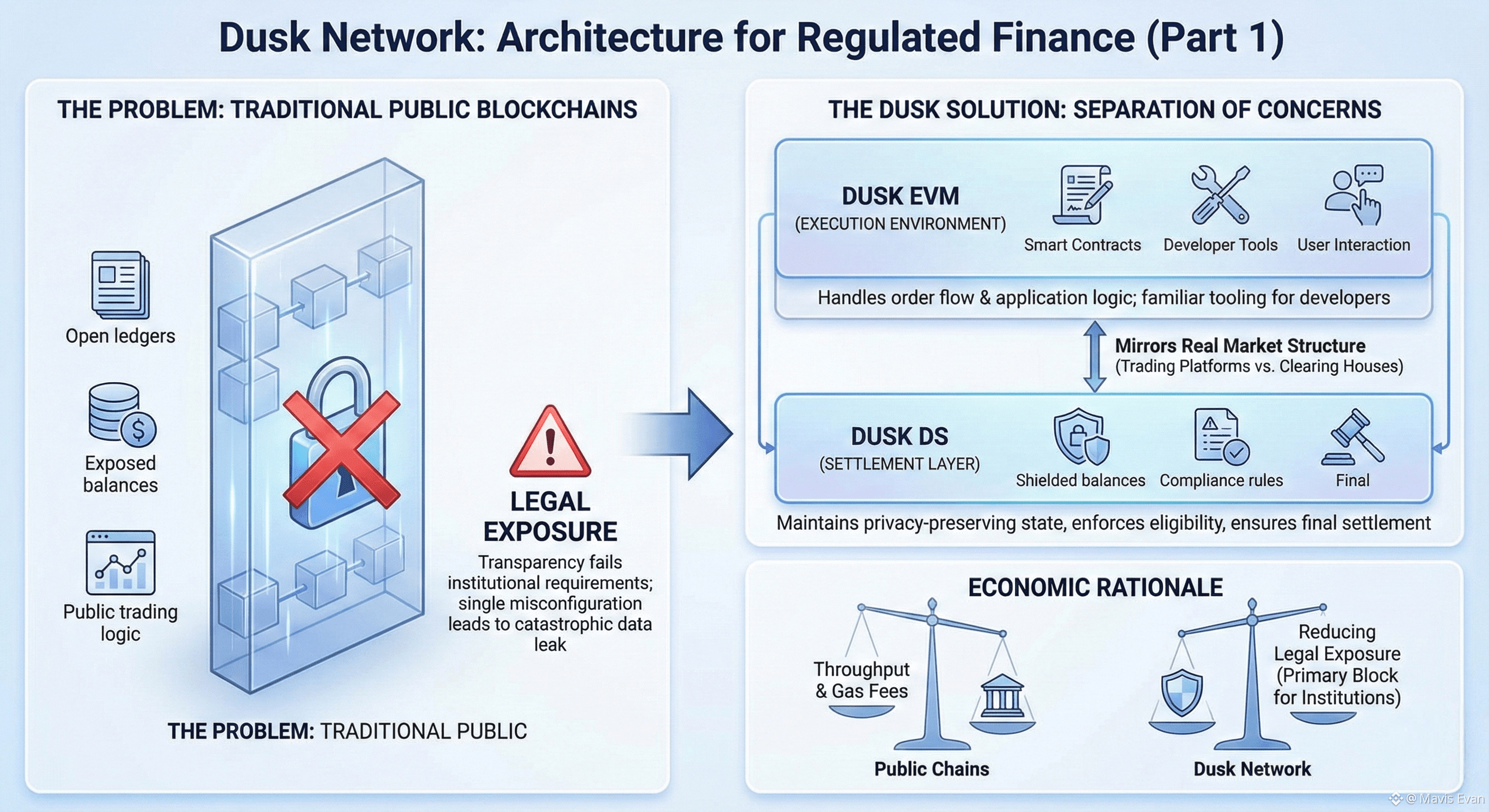
Public blockchains were not built with regulated finance in mind. They were designed to be transparent, open, and adversarial, which works for censorship resistance but fails almost every test that modern financial markets rely on. Institutions cannot expose balances, trading logic, or client relationships to the entire world. At the same time, they cannot retreat into closed systems that sacrifice auditability. Dusk exists in that narrow space where privacy and compliance are not competing goals but structural requirements.
The first design choice that reveals this intent is the separation between execution and settlement. Instead of forcing all logic into a single environment, Dusk places sensitive financial state into a dedicated settlement layer called DuskDS, while application logic runs in a parallel execution environment called DuskEVM. This mirrors how real markets operate. Trading platforms handle order flow and user interaction, while clearing houses manage final ownership, rule enforcement, and record keeping. By adopting this structure at the protocol level, Dusk acknowledges that regulated finance is not a single workload but a system of interlocking responsibilities.
This split is not cosmetic. It allows developers to write familiar smart contracts in the EVM-equivalent layer without handling confidential balances, identity constraints, or asset lifecycle rules directly. Those obligations are absorbed by DuskDS, which is responsible for maintaining privacy-preserving account states, enforcing who can hold or transfer assets, and ensuring final settlement is legally auditable. The developer experience stays close to existing tooling, but the financial semantics change beneath the surface.
The economic reasoning is subtle. Institutions are not primarily blocked by throughput or gas fees. They are blocked by legal exposure. On most public chains, a single misconfigured contract can leak sensitive data permanently. Dusk’s architecture assumes that financial applications will make mistakes and builds guardrails into the settlement layer so that exposure is not catastrophic. Privacy is not a feature developers add later. It is the default condition of state.
A practical example makes this clearer. Imagine a firm issuing a tokenized security that can only be held by verified participants and whose balances must remain confidential. In Dusk, the trading logic would live in DuskEVM, interacting with users through ordinary smart contracts. But ownership records, eligibility rules, and final transfers would be settled through DuskDS. Traders see what they need to see. Auditors can verify the integrity of the system without seeing private positions. The firm avoids building custom compliance infrastructure from scratch.
This also reshapes how auditability works. Traditional blockchains achieve trust by showing everything. Dusk aims to achieve trust by showing the right things to the right parties. Confidentiality and verification are handled together, not in layers bolted on after the fact. That is why DuskDS is treated as a base-layer system rather than a middleware service.
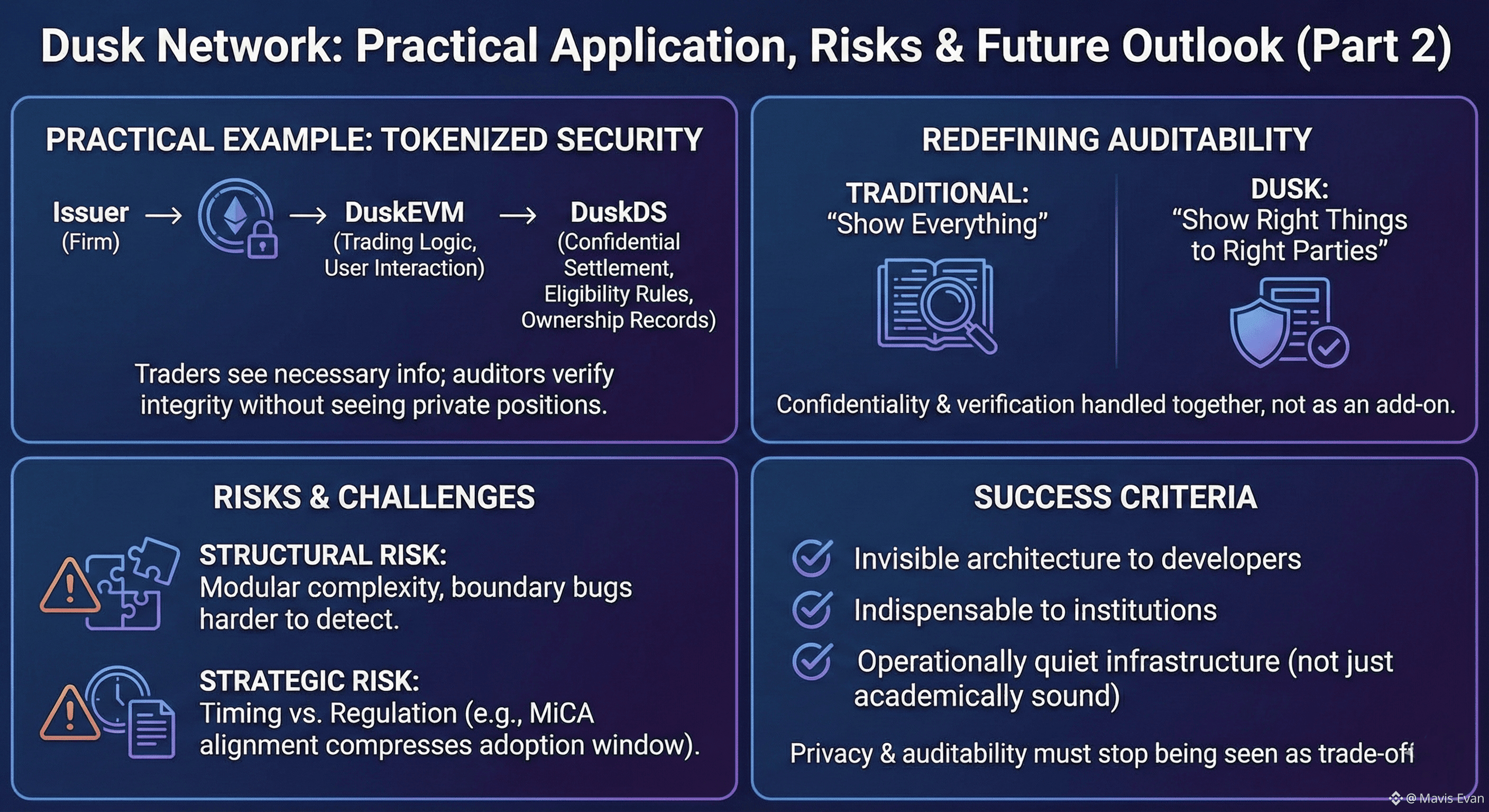
There are structural risks in this approach. A modular stack is harder to reason about than a monolithic chain. Bugs at the boundary between execution and settlement are harder to detect and more expensive to correct. Developers accustomed to open-state models may underestimate the complexity of designing around hidden balances and enforced rules. If tooling or documentation fails to make these constraints intuitive, adoption will stall regardless of technical merit.
There is also a strategic risk tied to timing. Dusk delayed mainnet deployment to align with evolving regulatory frameworks, particularly MiCA in Europe. This compliance-first posture protects institutional credibility, but it also compresses the window in which the network must prove real usage. Being early without users is survivable. Being compliant without adoption is not.
Dusk will succeed if its architecture becomes invisible to developers and indispensable to institutions. That requires more than cryptography. It requires that the separation between execution and settlement feels natural in daily development and that privacy and auditability stop being seen as trade-offs. It will fail if the system remains academically sound but operationally awkward. In regulated finance, infrastructure is not judged by how advanced it is, but by how quietly it works.

