The @Dusk network makes use of a decentralized and privacy-oriented digital currency that evolves the CryptoNote protocol through the groundbreaking discoveries in the field of Byzantine consensus and pseudo-random functions of world renown cryptographers such as Silvio Micali, Michael Rabin, Alexander Yampolskiy and Evgeniy Dodis.
Dusk radically departs from any other blockchain by employing an adaptive consensus mechanism, called Segregated Byzantine Agreement (SBA), which does not require the computational intensity of proof-of-work and is a fairer alternative to proof-of-stake.
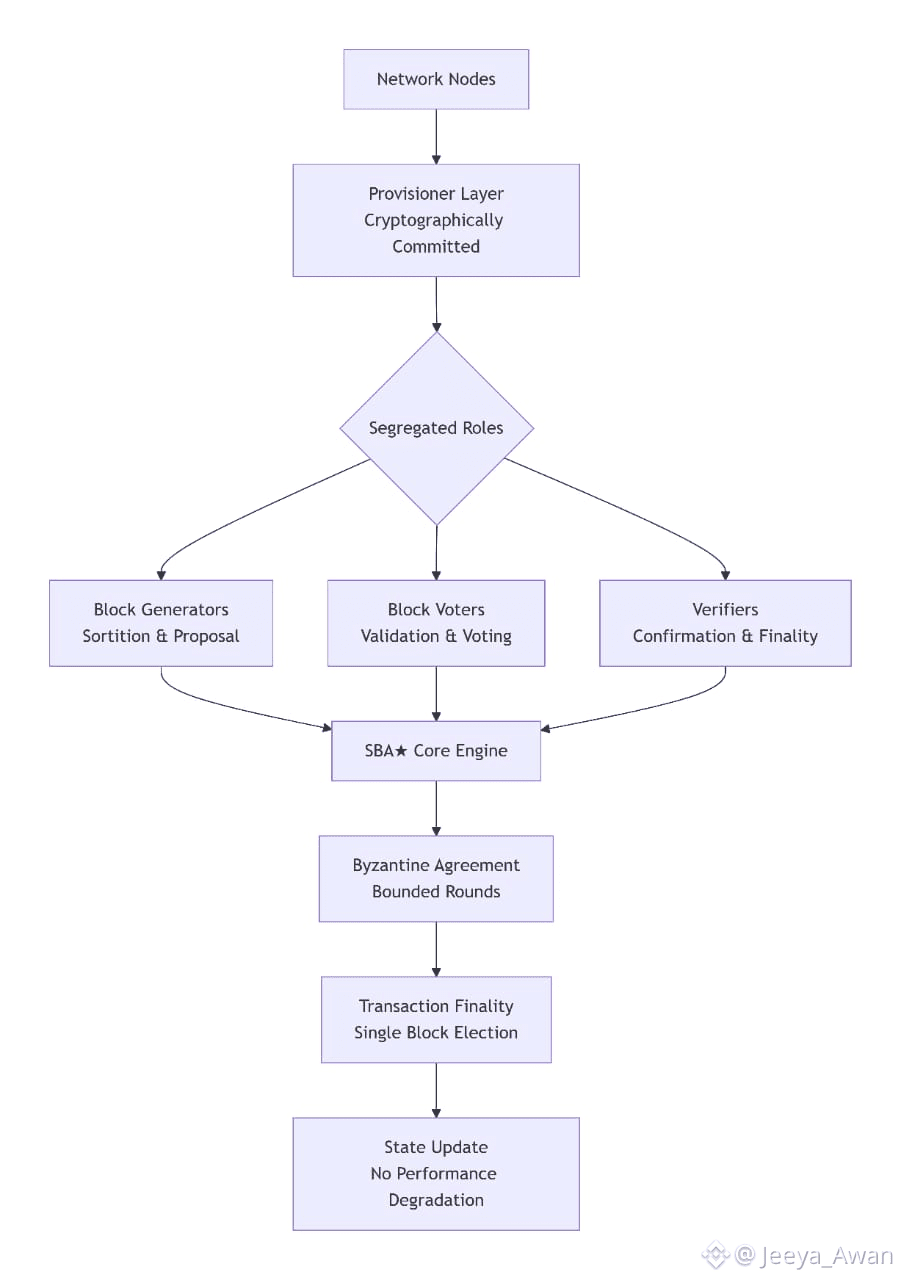
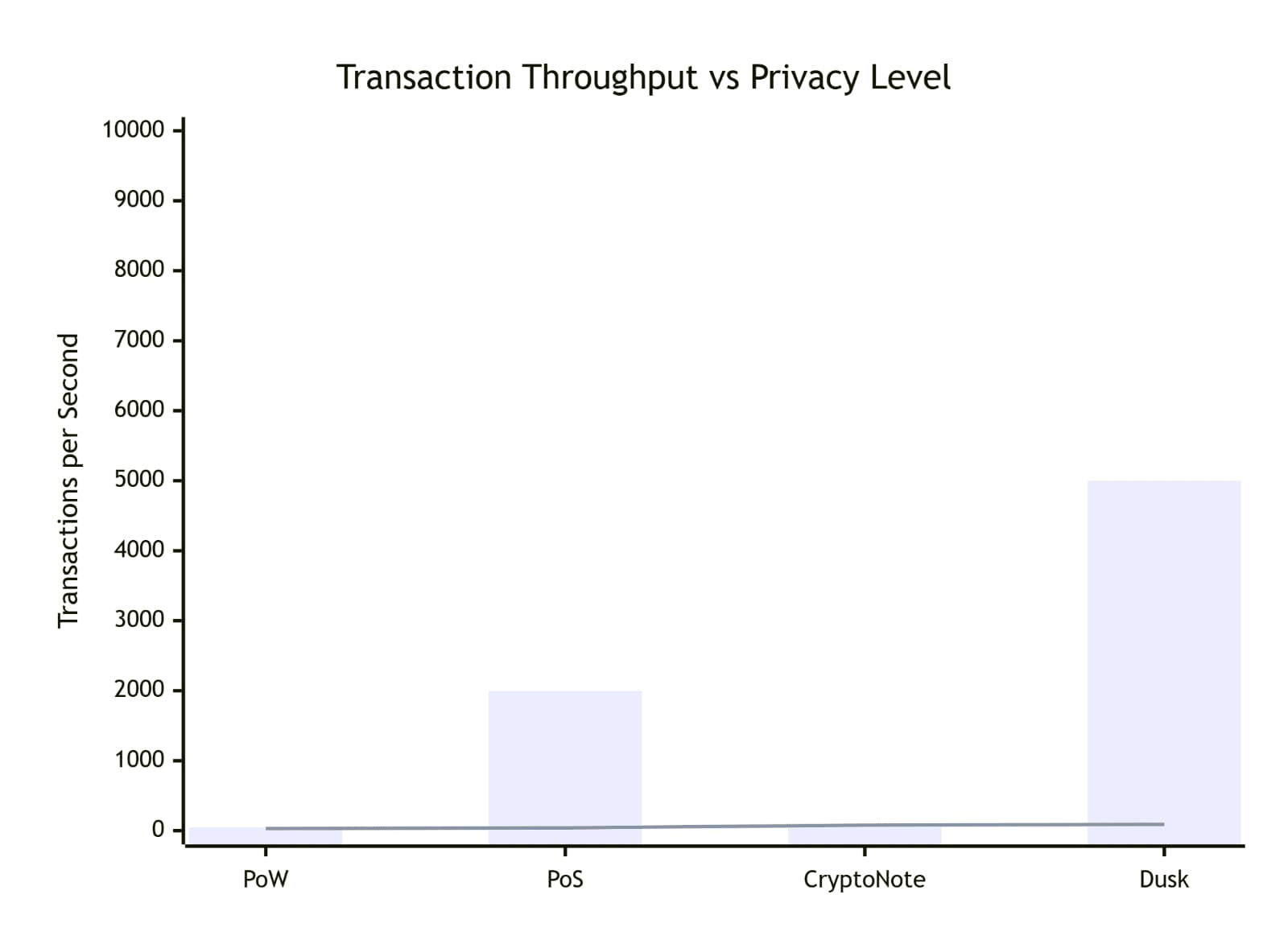
Built on such consensus algorithm, Dusk is poised to be the first to simultaneously achieve previously conflicting goals of guaranteeing transaction untraceability and unlinkability, safeguarding user privacy, reaching transactional finality after a bound number of rounds within a single block election and achieving virtually unbounded user scalability without any significant performance degradation.
The #Dusk network requires a heightened security setup designed specifically to:
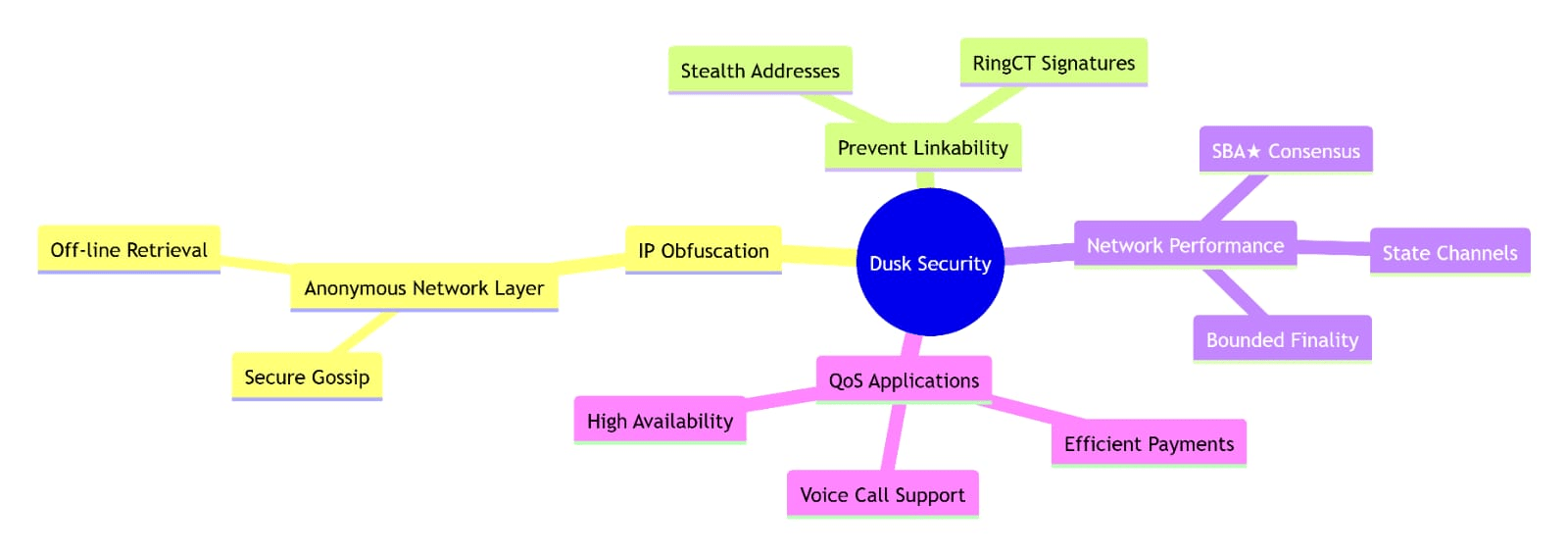
(1) Obfuscate IP addresses of the communicating peers
(2) Prevent linkability and traceability of accounts
(3) Guarantee network performance
(4) Implement efficient payment mechanism for high QoS applications such as secure and anonymous voice calls.
An important difference with CryptoNote, is that Dusk doesnot make use of proof-of-work mining and therefore drops completely CryptoNight and deviates substantially from the hashing algorithms therein adopted.
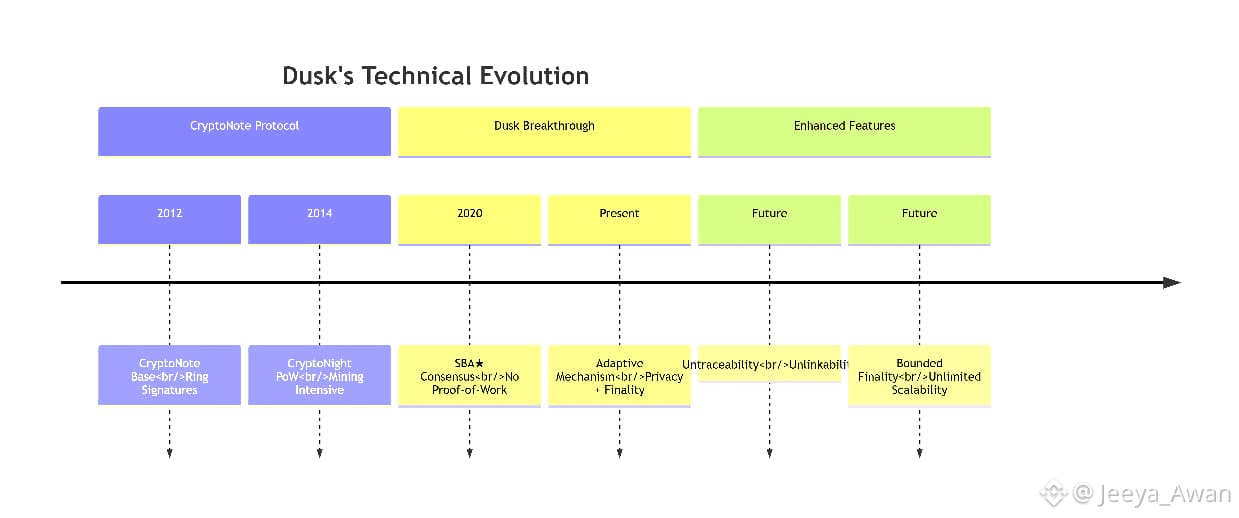
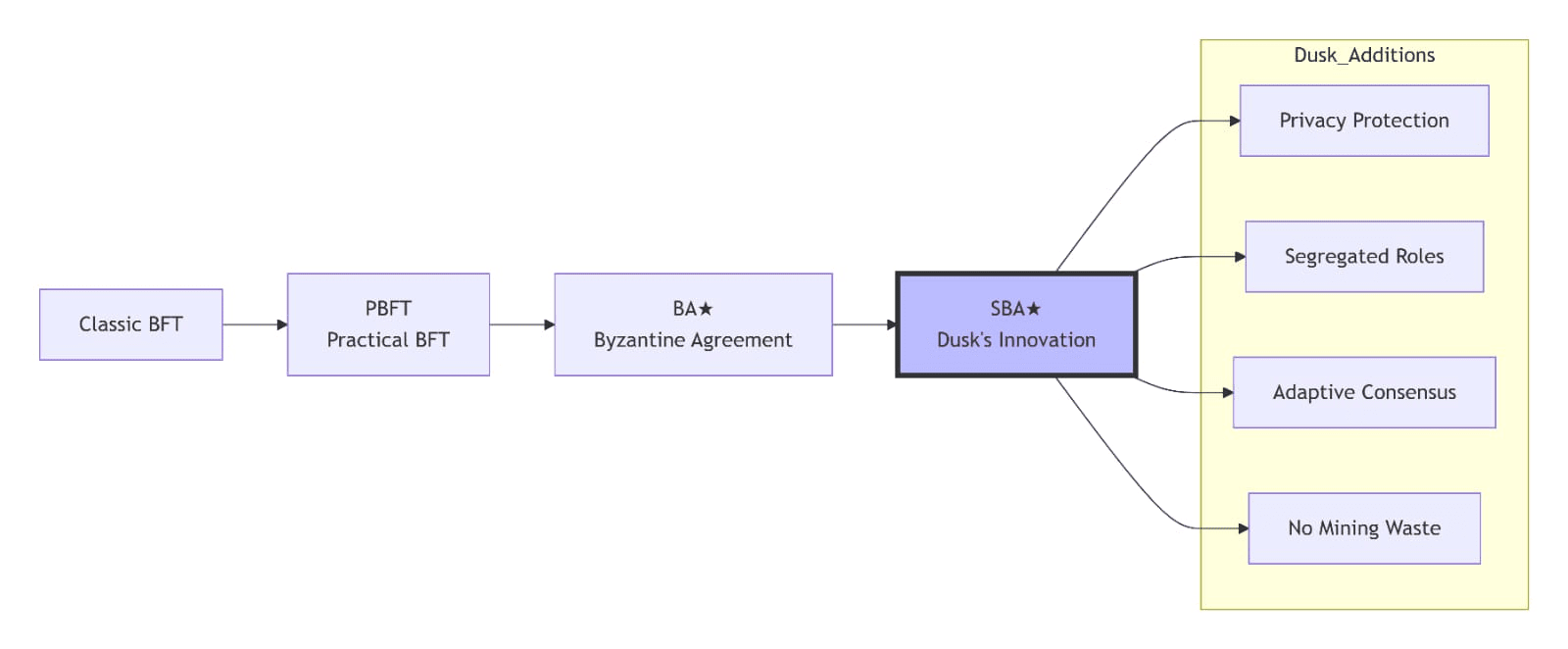
In particular, Dusk uses what we call Segregated Byzantine Agreement (SBA) protocol which enhances classic BA by implementing specific measures to protect peer privacy. SBA has been developed specifically to power the Dusk Blockchain and help meeting the aforementioned requirements.
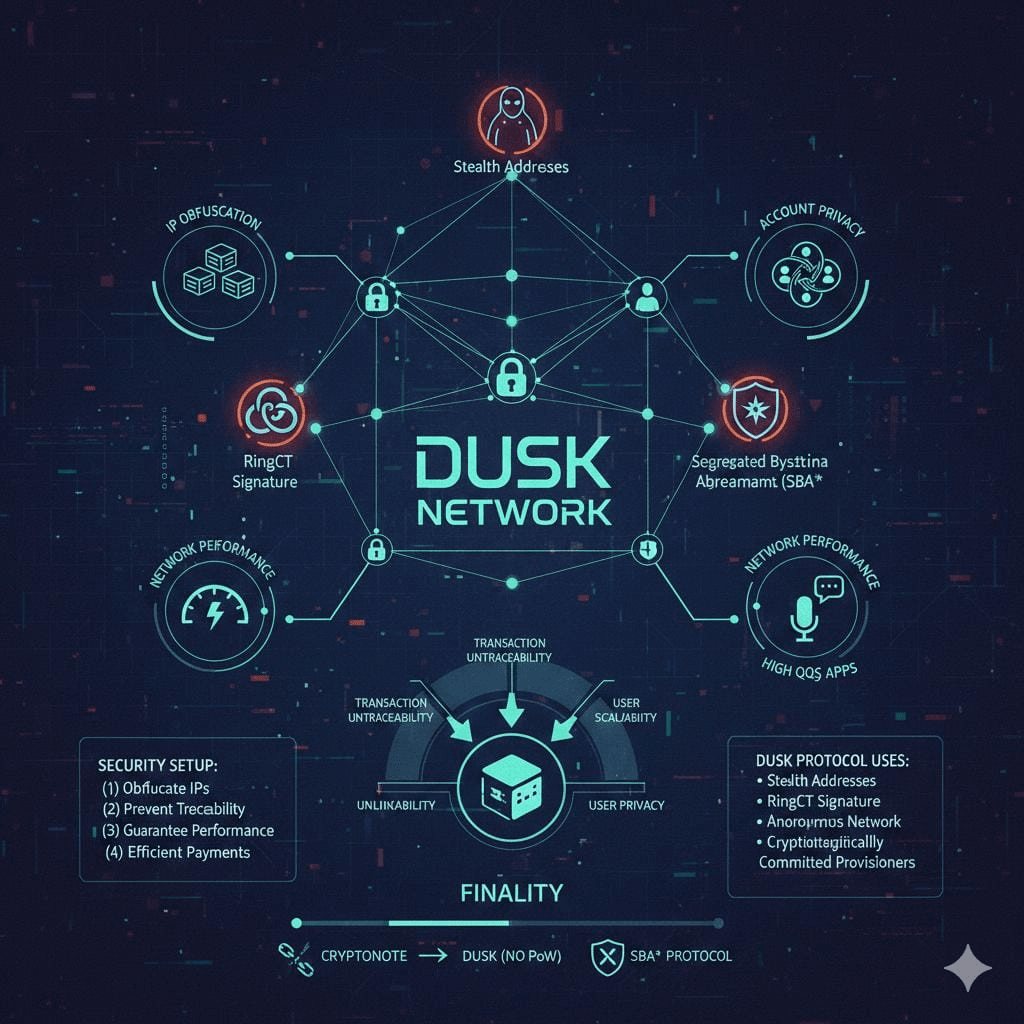
These efforts do not solely relate to the application layer but extend to the networking layer as well. This is why the Dusk protocol makes use of:
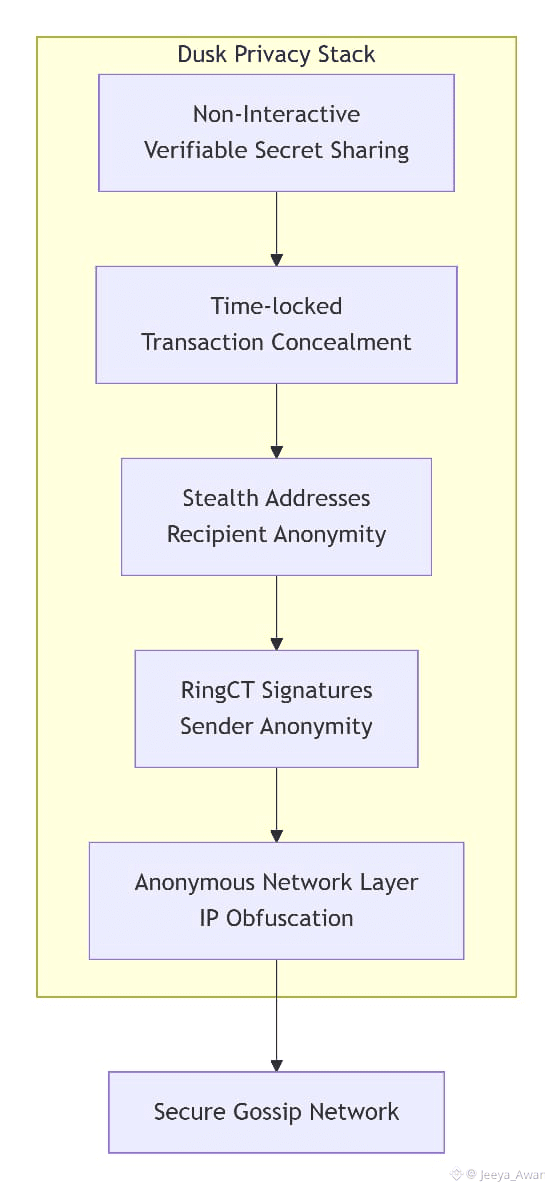
• Stealth addresses: to protect transaction recipient anonymity
• RingCT signature: to protect transaction sender’s identity
• Anonymous Network Layer: to protect the IP address of the network peers; to provide secure data transfer mechanism; to implement off-line data retrieval strategy; to power the anonymous gossip network for transaction propagation and verification.
• Non-Interactive Verifiable Secret Sharing Scheme: to conceal all but highest priority time-locked transactions from the participants to the Block Generation sortition
• Cryptographically Committed Provisioners: to protect the information about stake; to implement a division of responsibilities between Block Generators and the electable
• Block Voters and Verifiers; to boost network efficiency by acting as state channel guarantors; to incentivise participation to the network; to protect the balance information of
• transacting nodes; to prepare SBA for future expansion with non-balance and non-payment related weights such as storage contributed to the network (as in proof-of-storage), availability expressed in elapsed time since joining the network (as in proof-of-idle), etc.