Most blockchains talk about “apps,” but regulated finance is less about apps and more about behavior. What rules must be enforced. What must stay private. What must be provable. And what must settle with certainty.
@Dusk ’s larger vision sits inside that reality. It frames itself as infrastructure for regulated financial applications where privacy is not a workaround and compliance is not an afterthought. In that kind of system, the execution environment matters a lot, because execution is where the rules actually run.
That is why Dusk doesn’t stop at an EVM layer. DuskEVM exists for a clear reason: the world already knows Solidity. The tools are mature. Wallets, integrations, and developer habits are already there. If Dusk wants builders and institutions to ship faster, EVM familiarity is the shortest bridge.
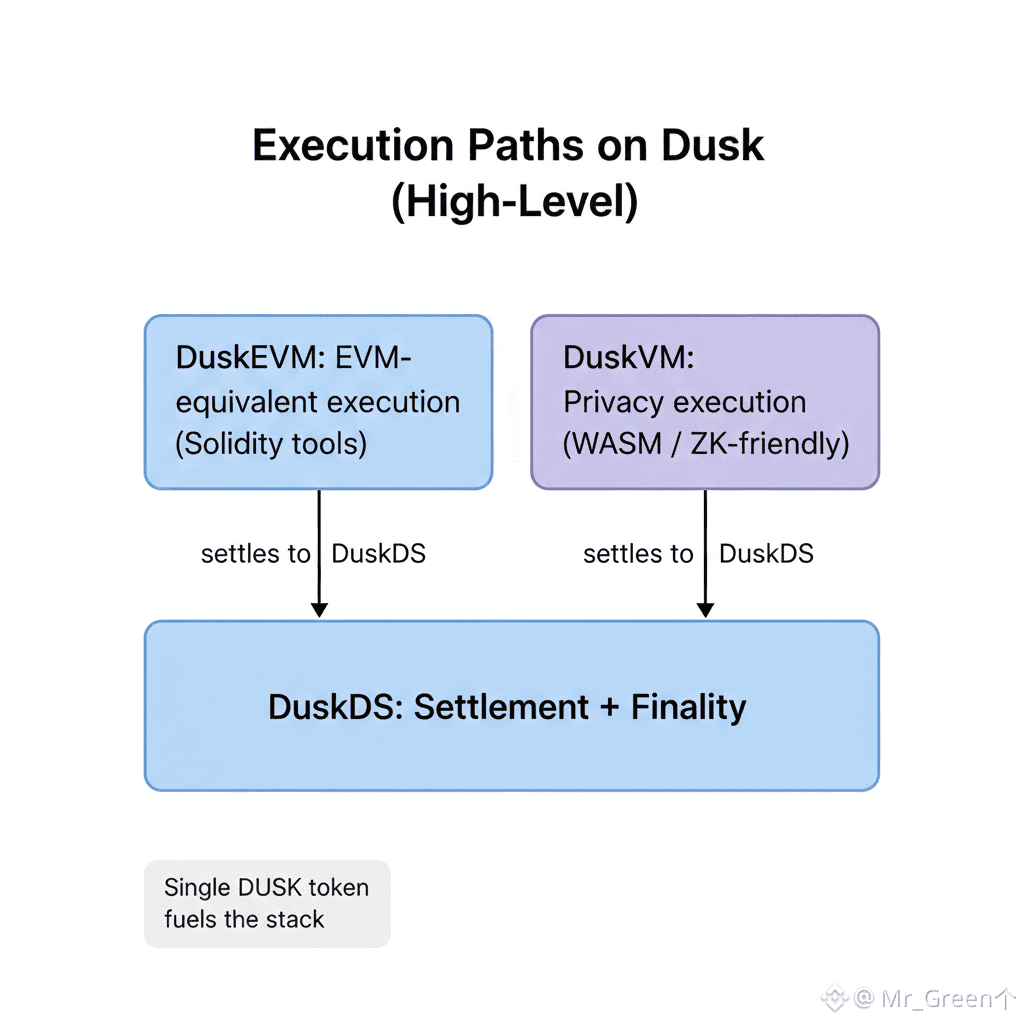
But privacy-heavy finance has a different kind of workload. Sometimes you don’t just need to run a contract. You need to run a contract that can handle privacy logic cleanly, verify cryptographic proofs efficiently, and keep data exposure under control. That’s where Dusk’s “second path” comes in.
This second path is the privacy-focused side of the stack, often described as DuskVM in Dusk’s multilayer architecture. In that architecture, DuskDS is the settlement and data layer, DuskEVM is the EVM execution layer, and DuskVM is a forthcoming privacy application layer. The key idea is separation. Settlement stays stable. Execution can specialize. Privacy gets its own room instead of being squeezed into whatever the EVM happens to allow.
To understand why this matters, it helps to understand what WASM is. WASM, or WebAssembly, is a compact bytecode format designed to run code in a predictable sandbox. Think of it as a common “portable machine language” that many programming languages can compile into. Instead of betting everything on one contract language, WASM lets an ecosystem support contracts that arrive through different front doors, as long as they end up in the same standardized bytecode at runtime.
Dusk’s documentation describes “Dusk VM” as its WASM virtual machine for running Dusk smart contracts, based on the Wasmtime runtime with custom modifications. It also states plainly that the VM expects WASM as the bytecode format, meaning smart contracts must be compiled into WASM to run. The VM provides the standardized execution environment, and the contract handles its own logic and validation inside that environment.
The interesting part is not just that it runs WASM. It’s why. Dusk’s documentation also frames Dusk VM as “ZK-friendly,” and says it can natively support certain zero-knowledge operations such as SNARK verification, while using a different approach to memory handling than many blockchain VMs. That reads like a design aimed at cryptography-heavy workloads, not just everyday token transfers. It suggests Dusk wants an execution environment that is comfortable with proofs, not merely compatible with them.
This is one of the clearest reasons to have both EVM and WASM in the same project. The EVM lane is about compatibility and speed of integration. It’s where you can deploy familiar contracts with familiar tooling and connect to familiar systems. The WASM/privacy lane is about doing the hard work of privacy-native applications in an environment shaped for that job, not forced into it.
Dusk’s multilayer evolution post describes the forthcoming privacy layer as executing complete privacy-preserving applications using the Phoenix output-based transaction model, and it mentions a virtual machine (Piecrust) that was embedded in DuskDS and is being extracted into that privacy layer. The message is consistent even if the internal naming evolves: privacy execution is being separated and treated as a dedicated domain, not a feature toggle.
There is also a practical engineering reason this approach can age well. Regulated finance changes slower than consumer apps, but it changes. New compliance expectations appear. New asset structures become common. New privacy demands emerge when institutions get serious. A modular stack lets Dusk evolve execution environments without constantly disturbing settlement. That’s a mature posture for a system that wants to be used under scrutiny.
And the DUSK token is meant to keep the whole stack coherent while this happens. Dusk’s multilayer architecture post states that a single $DUSK token fuels all three layers, and that a validator-run native bridge moves value between layers without wrapped assets or custodians. In plain terms, DUSK is intended to be the common fuel: staking and security at the settlement layer, and gas for activity in the execution layers. That matters because fragmentation is a hidden tax. If each layer has its own fuel, users hesitate and developers suffer. A single economic thread makes a modular system feel like one system.
So the “why another VM?” question has a clean answer in the Dusk context. Dusk is trying to build regulated financial infrastructure where privacy isn’t a bolt-on. That means it needs a place where privacy-heavy logic can live comfortably, where proof verification and confidential workflows are first-class citizens. The EVM path brings developers and integrations quickly. The WASM/ZK-friendly path is meant to carry the deeper privacy workload with fewer compromises. And DuskDS beneath it all is meant to keep settlement final and legible.
If Dusk succeeds, it won’t be because it picked the “best” VM in abstract. It will be because it matched the right execution environment to the right job, while keeping the system unified enough to be usable.

