I watched the ledger.
Not a single block had moved yet.
And that was expected.
Dusk’s Layer 1 had paused a new governance action. Staking thresholds weren’t met. Permissions weren’t aligned. The system held. Nothing executed. Not partially. Not tentatively.
Dusk's Modular architecture isolates every operation. One rule fails, one module halts. Others continue. The pause doesn’t ripple outward. Nothing spreads beyond its bounds. You notice it not in alerts, not in dashboards, but in the rhythm, or lack of it, across the system.
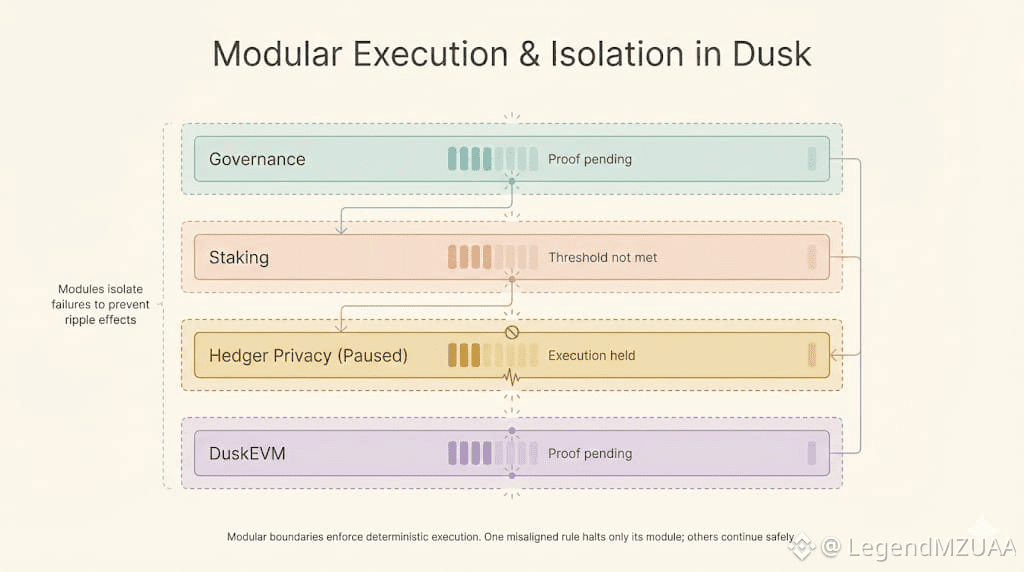
On Dusk, Audit trails recorded the check. Privacy remained intact. Sensitive data never left its silo. Yet every action left evidence. Every alignment, every approval, every stake, traceable without exposure.
I rotated through the governance panel. Institutional-grade applications were queued. The system enforced rules silently. Execution waited for alignment. A validator could not override. A developer could not shortcut. The network demanded adherence before anything could proceed.
One module completed. Another hesitated. The ledger updated only where proofs passed. The rest remained on hold. Predictable. Deterministic. Dusk's reliability doesn’t depend on luck or speed. It depends on enforced boundaries, on the architecture’s discipline.
Sometimes it’s frustrating. Modules sit idle while the rest moves forward. I felt the waiting, the subtle stutter in expected flows. But that pause was intentional. That hesitation prevented mistakes, prevented misalignment. Institutions experience trust not because that Dusk's system is fast, but because it cannot be wrong, at least, not silently.
Governance isn’t advisory. Staking isn’t ceremonial. Both interrupt flows directly. A misaligned threshold freezes execution. Auditability logs every step. Privacy layers enforce the silence around sensitive operations. On Dusk, Everything is visible only where it is meant to be.
Eventually, all proofs aligned. Governance thresholds met. The ledger advanced. But the lesson remained clear: the system teaches reliability through enforced constraint. It moves when it can. Not before.
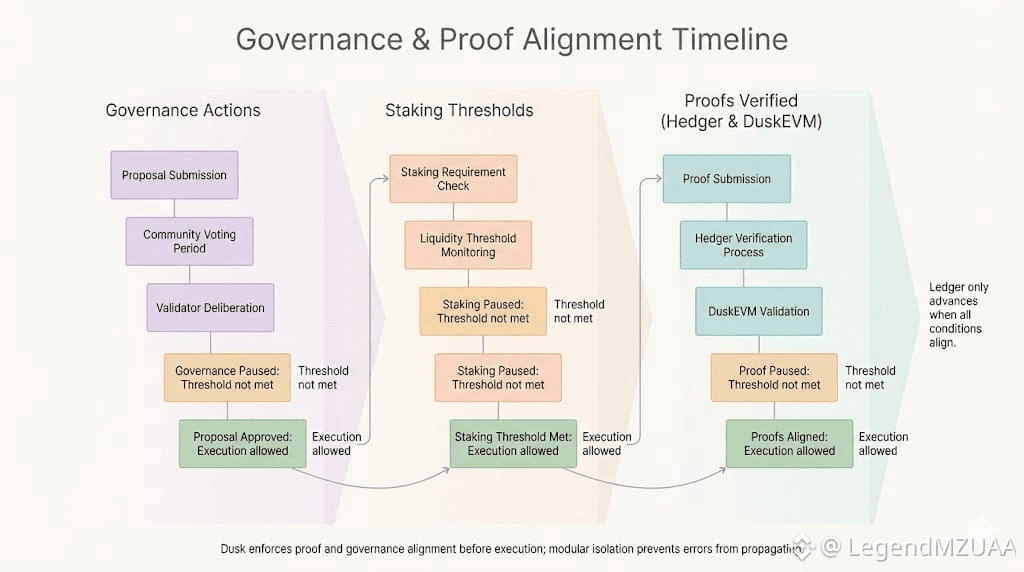
Every module, every check, every governance action works inside its envelope. The Dusk's architecture isolates failures. Institutional-grade applications run with no surprises. Privacy is preserved. Auditability is assured. The network won’t bend, won’t skip, won’t misfire.
And that’s why trust exists here, not because it executes faster, but because it holds, always.
