The security of a Proof-of-Stake (PoS) blockchain is not a cryptographic equation. It’s a game. The players are rational, profit-seeking actors stakers, validators, provisioners. The rules are encoded in the protocol's incentive mechanisms. The prize is the block reward. The goal for the network architect is to design a game where the single most profitable, rational strategy for every player is also the one that makes the network secure, live, and decentralized.
Dusk Network's security model, centered on its Provisioners, is a masterclass in this kind of mechanism design. It confronts and solves fundamental game-theoretic dilemmas that plague simpler staking systems. It doesn't just ask users to stake; it constructs a sophisticated economic arena where honest participation is continuously reinforced, and malicious or lazy behavior is systematically identified and penalized. This isn't passive staking for yield it's active security provision as a high-skill game.
I. The Provisioner: More Than a Staker
In Dusk’s lexicon, a Provisioner is not a passive token holder. It is an active consensus participant who has locked a minimum stake (currently 1,000 DUSK) and stands ready to perform one of three critical, randomly assigned roles in the Succinct Attestation (SA) protocol:
Block Generator: The sole proposer of a candidate block for a consensus round.
Validator: A member of a committee that cryptographically audits the proposed block.
Ratifier: A member of a final committee that attests to the validity of the validation process itself.
Becoming a Provisioner is a deliberate act with weight. A stake S is defined as (amount, height), where height is the block it was included in. It then enters a maturity period of M = 2 * epoch - (height mod epoch). This means a new stake is ineligible to participate in consensus for the remainder of its arrival epoch plus one full additional epoch (an epoch is 2,160 blocks).
Why this complexity? It creates a commitment latency. An attacker cannot instantly amass stake and attack the chain. They must wait, exposing their capital and intentions. This is the first line of defense a time-lock on influence.
II. Deterministic Sortition: The Fair Lottery of Influence
The core of the game is Deterministic Sortition (DS). This is the algorithm that, for each round and each step (Proposal, Validation, Ratification), selects who gets to play which role. Its design is critical to fairness and security.
How it works (The "Weighted Lottery"):
Imagine all eligible Provisioners are lined up, each holding a "weight" equal to their staked DUSK amount. The protocol generates a random "score" for each selection event, derived from a verifiable random function (VRF) seeded by the previous block's signature.
The algorithm walks down the line:
It compares the score to the first Provisioner's weight.
If the score ≤ weight, that Provisioner is selected and gets 1 "credit" (representing their voting power in a committee). Their weight is then reduced by 1 DUSK for the next credit assignment in that same selection.
If the score > weight, it subtracts that Provisioner's weight from the score and moves to the next, repeating the process.
The Game-Theoretic Elegance:
Proportionality: Selection probability is directly proportional to stake. More stake = more tickets in the lottery.
Diminishing Returns Per Round: The subtraction of 1 DUSK from weight per credit assigned prevents whales from dominating a single committee. It creates a smoother, more equitable distribution of influence within a single consensus action.
Unpredictability & Non-Interactivity: The "score" is derived from the previous block's seed, which is the signature of the previous block's generator. This means future sortition is unpredictable until the exact moment the previous block is produced. There is no way to pre-calculate or bribe future committee members in advance. The game state updates with every block.
This system ensures that influence is purchased with stake, but exercised in a randomized, fair, and unpredictable manner. You buy a share of the network, not a specific seat at the table.
III. The Incentive Labyrinth: Rewarding Cooperation, Not Sabotage
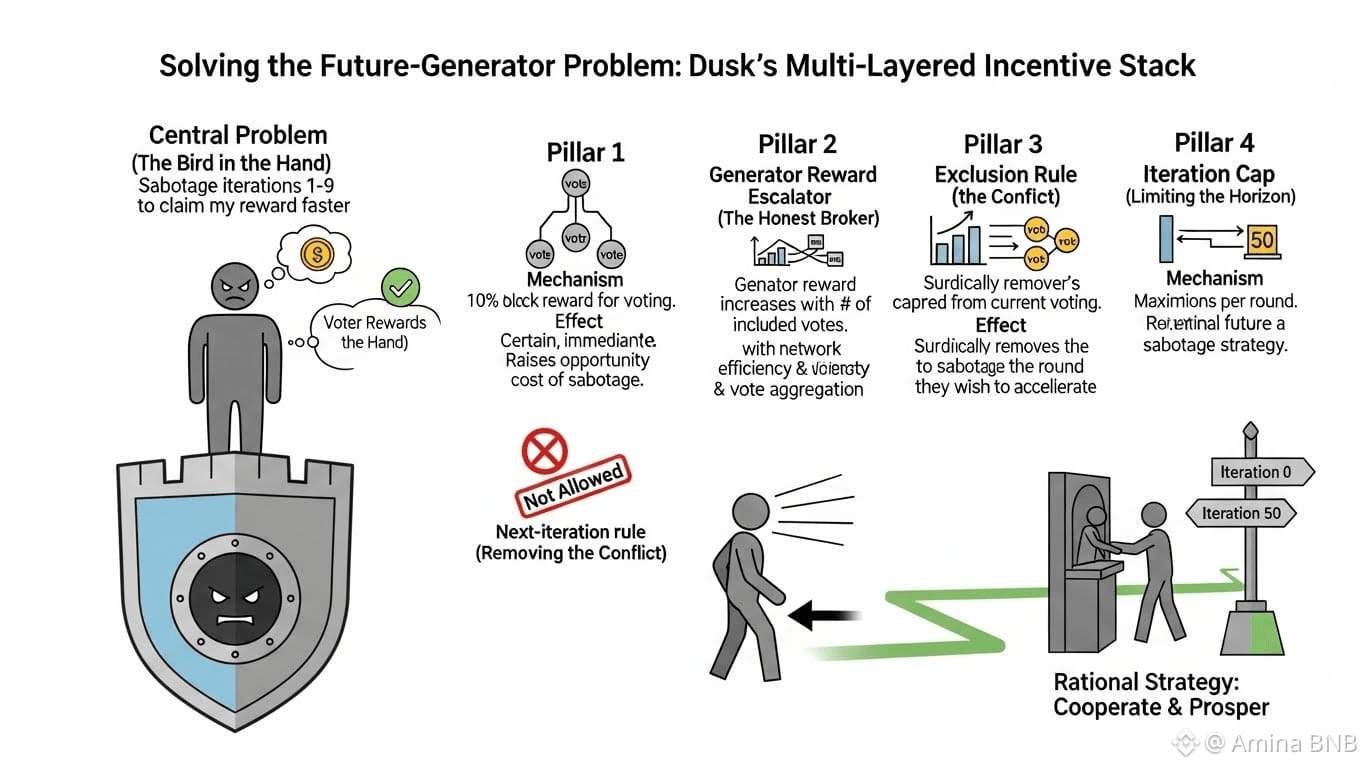
This is where Dusk's model transcends simple "reward for participation." It is engineered to navigate a specific, treacherous incentive trap: The Future-Generator Problem.
The Dilemma: In a round-based system with multiple possible iterations (0 to 50), a Provisioner who knows they are slated to be the Block Generator in a future iteration (e.g., iteration 10) has a perverse incentive. They could sabotage earlier iterations (1-9) by not voting, or even voting Invalid on valid blocks. This would cause earlier rounds to fail, pushing the network to iteration 10 faster, allowing them to claim the larger block generator reward sooner.
If this incentive is left unchecked, the network would be paralyzed by strategic passivity.
Dusk's Multi-Layered Solution (The "Cooperation Engine"):
Voter Rewards – The Bird in the Hand (10% of block reward): A significant portion of each block's reward (new mint + fees) is reserved for the voting committees (Validation & Ratification). This is a certain, immediate reward for simply doing your job as a voter. Choosing to sabotage for a future, uncertain generator reward now has a high opportunity cost.
Generator Reward Tied to Voter Inclusion – The Honest Broker Incentive: The block generator's reward (80% of total) is split. A base 70% is fixed. A variable 10% escalator depends on how many committee votes they include in the block certificate. To maximize their reward, the generator is incentivized to be an efficient message propagator and to include all valid votes, strengthening the attestation. Their profit is aligned with network health.
Exclusion of Next-Iteration Generators – Removing the Conflict: The Provisioner selected to be the next block generator is barred from voting in the current consensus steps. This surgically removes their conflict of interest. They cannot sabotage the current round to advance their own turn.
Iteration Cap (50) – Limiting the Horizon: By capping the maximum number of iterations, the protocol limits how far into the "future" a strategic saboteur could be planning, reducing the potential payoff of such a strategy.
This elegant bundle of mechanisms transforms the game. The most rational, profitable path for a Provisioner is now:
Always be online and ready.
Vote honestly and promptly whenever selected for a committee (to earn voter rewards and maintain a good standing).
If selected as Generator, produce a valid block and include all votes (to maximize the generator escalator).
Never attempt to sabotage, as the costs (lost voter rewards, slashing risk) far outweigh the dubious benefit of maybe generating a block sooner.
The protocol manufactures cooperation through exquisite incentive design.
IV. The Carrot and the Stick: Slashing as a Precision Instrument
Incentives aren't just about rewards. They are about consequences. Dusk's penalty system, or slashing, is not a blunt weapon. It's a calibrated, escalating system of justice that distinguishes between negligence and malice.
Minor Faults (The "Soft" Penalty):
Example: A selected Block Generator fails to produce and broadcast a candidate block within the timeout.
Penalty – Suspension & Soft Slashing: The Provisioner is suspended from participation for a number of epochs. Additionally, a portion of their stake is locked (soft slashed). This locked stake still counts toward their total for weight calculation but is temporarily illiquid and at risk. It reduces their influence and earning potential without destroying capital for a non-malicious fault.
Major Faults (The "Hard" Penalty):
Examples:
Equivocation: Signing two different candidate blocks for the same iteration.
Double Voting: Casting more than one vote in the same committee step.
Proposing an Invalid Block: A Generator creates a block that violates protocol rules.
Penalty – Hard Slashing: A portion of the Provisioner's staked DUSK is permanently burned. This is a direct, capital-destructive penalty. The amount burned escalates with the severity and recurrence of the offense.
The Psychological Impact: This graduated system is crucial. A simple "offline = burn" rule would deter participation due to fear of normal technical glitches (power outage, internet drop). Dusk's model says: "We understand accidents happen, and you'll be benched for a while. But if you actively attack the network, we will burn your capital."
It creates a safe environment for honest operators while maintaining a terrifying deterrent for attackers.
V. The Provisioner's Calculus: Modeling Risk and Reward
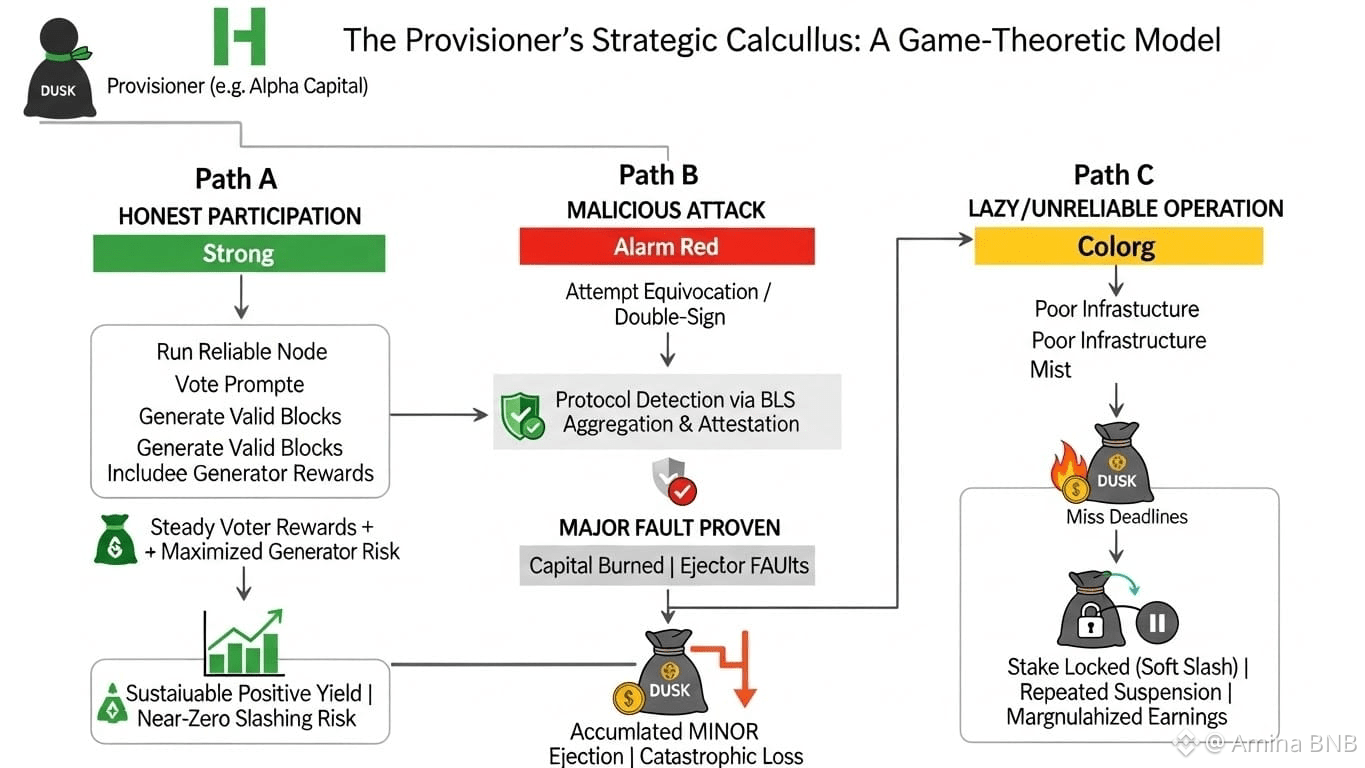
Let's put a hypothetical Provisioner, "Alpha Capital," through the game-theoretic wringer. They have staked 50,000 DUSK.
Scenario A: Honest Participation
They run reliable infrastructure.
When selected as a voter (frequent), they earn a steady stream of Voter Rewards, proportional to their credit weight.
If selected as Generator (rare but lucrative), they work to include all votes to claim the full 80% reward escalator.
Expected Value: Steady, positive yield from voting + occasional large generator rewards. Risk of slashing is near-zero.
Scenario B: Malicious Attack (Equivocation)
To try and double-spend or cause a fork, they attempt to sign two different blocks.
The protocol's BLS signature aggregation and attestation system would detect this with high probability.
Result: A Major Fault is proven. A significant portion of their 50,000 DUSK stake is burned. They are likely permanently ejected from the Provisioner set. The attack fails, and they suffer catastrophic loss.
Scenario C: Lazy/Unreliable Operation
They run poor infrastructure and often miss their turns to vote or generate.
They accumulate Minor Faults, leading to repeated suspensions and soft slashing (stake lock).
Result: Their effective stake weight decreases due to locks. Their earning opportunities plummet during suspensions. They become an unprofitable participant and are naturally marginalized by the system. The network's active set remains robust.
The game theory is clear. Scenario A dominates. It is the only strategy with a positive, sustainable expected value. Scenarios B and C are dominated strategies that lead to loss.
Conclusion: Security as an Emergent Property of a Well-Designed Game
Dusk Network's security does not rest on the hope of altruism or the fear of a vague "reputation loss." It is engineered security, emerging from a closed economic system where the Nash Equilibrium the stable state where no player can unilaterally improve their outcome is a network that is live, secure, and decentralized.
The Provisioner is not a mere stakeholder; they are a player in a high-stakes, high-reward game where the house rules are transparent, the penalties for cheating are severe and certain, and the rewards for cooperation are rich and layered.
This is how you build a blockchain for finance: you assume everyone is rational and self-interested, and then you design a world where their self-interest compels them to build the very fortress that protects everyone's assets. In the end, Dusk's most profound innovation might not be a cryptographic proof or a consensus step, but the invisible hand of its incentive design, quietly guiding its participants to secure the network, block by attested block.
