Smart contract developers live in a prison of their own success. The WebAssembly (WASM) virtual machine the near-universal runtime for blockchain smart contracts was a breakthrough. It provided sandboxed security, deterministic execution, and language agnosticism. But it came with a life sentence to computational purgatory. For the most critical workloads in modern blockchain zero-knowledge proofs, advanced cryptography, complex hashing WASM is a ball and chain, imposing performance penalties of 2x to 3.5x compared to native execution.
This isn't just an inconvenience; it's an existential barrier. A blockchain like Dusk, whose entire value proposition hinges on efficient, private computations (ZK proofs for Phoenix, attestations for SA), cannot afford to have its smart contracts its application layer bogged down in a slow-motion simulator.
Dusk's answer is Piecrust, a virtual machine that performs a daring jailbreak. It doesn't just run WASM; it integrates a system of Host Functions that allow smart contracts to directly call optimized, native machine code for critical operations. This isn't an optimization it's a architectural revolution that redefines the relationship between a smart contract and the underlying chain. It turns the chain from a passive computer into an active co-processor, unlocking a new class of cryptography-intensive dApps that were previously unimaginable.
I. The WASM Wall: Why Your Smart Contract is Running in Quicksand
To understand the breakthrough, we must diagnose the disease. Why is WASM slow for cryptography?
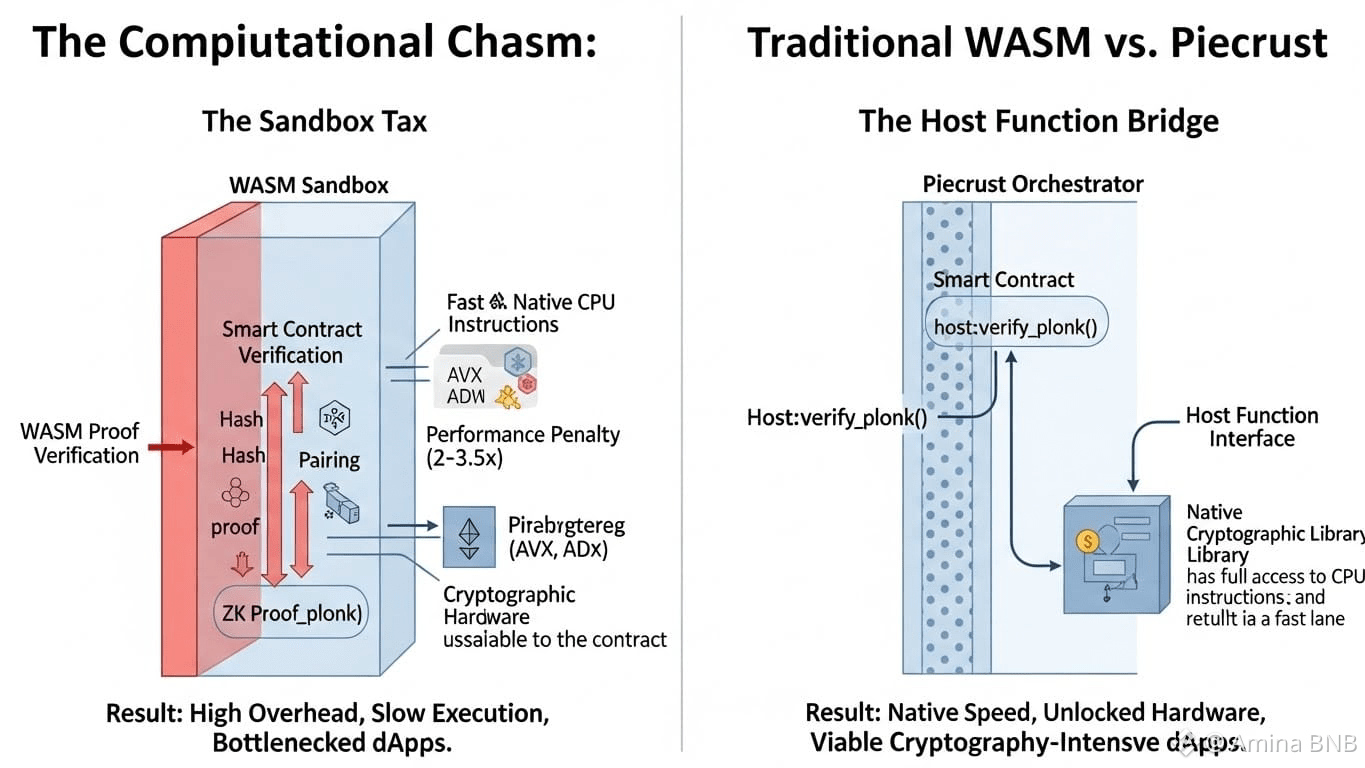
The Sandbox Tax: WASM's primary virtue is security through isolation. It runs in a virtualized, memory-safe sandbox. Every interaction between the contract and the "outside world" (like the blockchain state or system libraries) must go through a narrow, heavily checked interface. This adds overhead for every call.
The Interpretation/Compilation Overhead: While modern WASM engines use Just-In-Time (JIT) compilation, they still start from a platform-agnostic bytecode. Converting this to optimized native machine code takes time and memory, a cost paid during execution. For short, cryptographic functions called thousands of times per block, this overhead dominates.
Lack of Hardware Access: Cryptographic operations like pairing checks (for BLS signatures) or prime field multiplications (for ZK proofs) can be accelerated by specific CPU instructions (e.g., ADX, BMI2) or even hardware security modules. A sandboxed WASM runtime has no direct access to these.
The Result: A study cited in Dusk's whitepaper notes WASM execution can be 45-255% slower than native code for complex applications. For a ZK proof verification that might take 50ms natively, WASM could add another 25-125ms of pure overhead. In a blockchain targeting sub-second finality, this is the difference between viability and impossibility.
II. The Piecrust Paradigm: The VM as a Conductor, Not a Performer
Piecrust reimagines the VM's role. Instead of being the sole, isolated executor of all logic, it becomes an orchestrator or conductor. It manages the high-level business logic of the smart contract (written in Rust and compiled to WASM), but when the contract needs to perform a heavy, standardized cryptographic lift, it doesn't struggle in the sandbox. It calls out to the host.
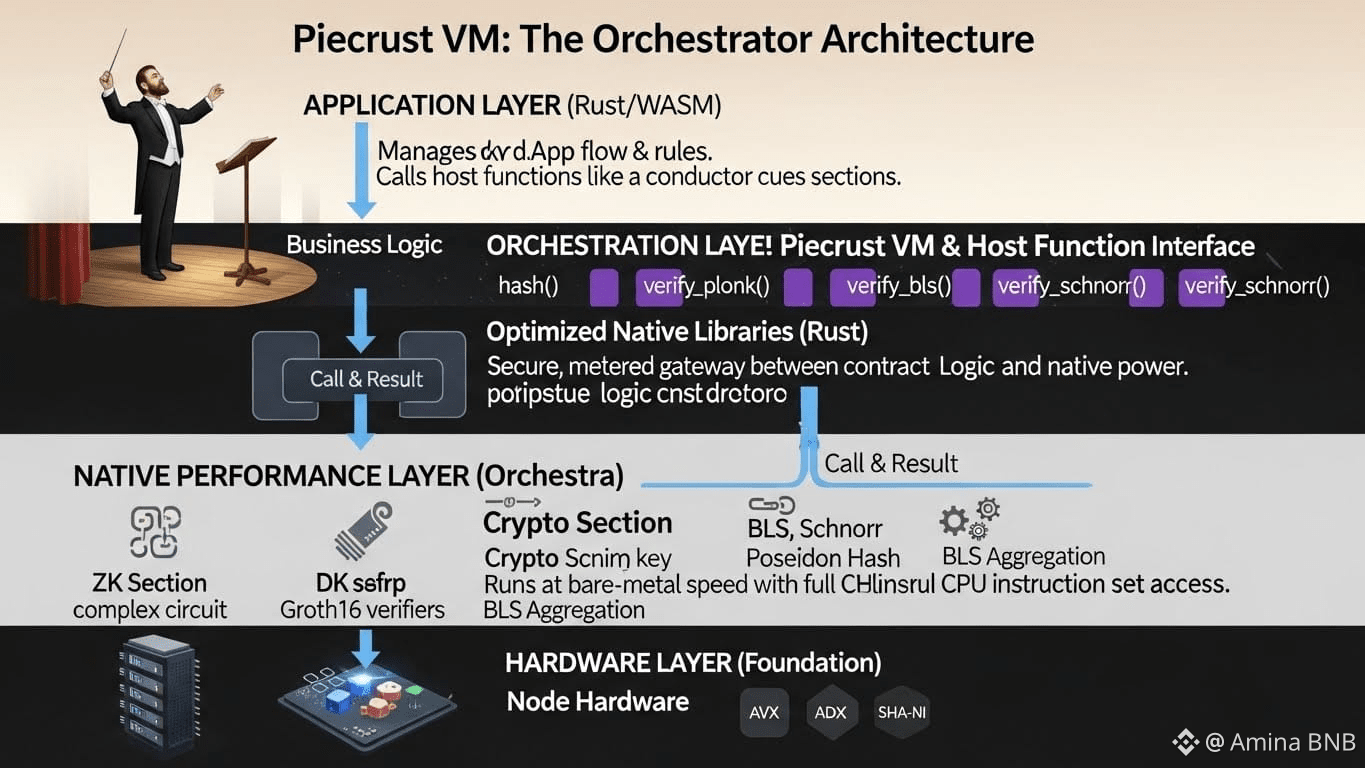
The smart contract (WASM Module) calls a function like verify_plonk(). This is not a WASM function. It's a Host Function a pre-defined gateway that exits the WASM sandbox and transfers control to the node's native, optimized cryptographic library. The library executes at native speed, using all available CPU optimizations, and returns the result directly to the contract's memory space.
The Mental Shift: It's the difference between a chef painstakingly grinding flour by hand to make pasta (WASM) and a chef using a high-powered, certified kitchen appliance to do it instantly and perfectly (Host Function). The chef's creativity (the contract logic) is unchanged, but their capability is exponentially greater.
III. The Host-Function Arsenal: A Toolkit for Financial Cryptography
Dusk's host functions aren't random. They are a curated, battle-hardened arsenal for building financial-grade, privacy-preserving applications. Let's examine the key tools:
hash(data) → scalar: Provides direct access to the Blake2b and Poseidon hash functions, returning a truncated scalar. Poseidon is a ZK-friendly hash, essential for efficient circuit construction in Phoenix. Calling it natively avoids the massive overhead of implementing it within the WASM sandbox.
verify_plonk(proof, circuit, public_inputs) → bool: This is the ZK workhorse. PLONK is a universal, updatable ZK-SNARK system. A Zedger contract for confidential securities can use this to verify, in native time, that a complex transfer (involving whitelist checks, balance conservation) is valid, without learning any of the private inputs (amounts, identities).
verify_groth16_bn254(proof, vk, public_inputs) → bool: Offers Groth16 verification in the BN254 pairing-friendly curve setting. This provides compatibility with a vast ecosystem of existing ZK tools and circuits (like many from Ethereum's ecosystem), allowing for cross-chain or cross-protocol privacy applications.
verify_schnorr(signature, public_key, message) → bool & verify_bls(signature, public_keys[], message) → bool: These are the consensus enablers. Schnorr signatures are efficient and widely used. BLS signature aggregation is the cryptographic magic behind SA consensus, where thousands of committee votes are compressed into one verifiable attestation. A staking contract or governance module can verify these signatures natively, at the speed of the chain itself.
The Implication: A developer building a dark pool on Dusk can write a contract where the core logic matching orders is in clear, manageable Rust/WASM. But the moment a trade is matched, it calls a host function to verify a ZK proof that the trader has sufficient confidential funds (via Phoenix), and another to aggregate BLS signatures for a multi-party settlement attestation. The heavy crypto is offloaded, and the contract remains simple, secure, and fast.
IV. The Security Paradox: Unleashing Native Power Without Sacrificing Safety
The immediate objection is security: "You're letting contracts run native code! That's unsafe!" This is where Piecrust's design is genius. The security model shifts but does not break.
Determinism & Gas Metering: Host functions are not arbitrary native code. They are a fixed, audited set of functions compiled into the node client itself. Their execution is deterministic the same input on any Dusk node, anywhere, produces the same output. Crucially, they are also integrated into the gas metering system. The contract pays gas for the host function call, with the gas cost reflecting the true, native computational cost of the operation. No one gets free, unbounded computation.
Sandboxing at the Node Level: The threat model changes from "protecting the node from the contract" to "protecting the chain from a malicious node." A host function is part of the node's client software. If a node operator modifies it to return an incorrect result, they break consensus. The BFT consensus protocol (SA) is designed to tolerate and slash such Byzantine behavior. The security guarantee becomes: "The network of honest nodes will reject blocks containing invalid results from host functions."
Auditability & Upgrade Path: The set of host functions is a core part of the protocol specification. They are open-source, auditable, and versioned. Upgrading them requires a network fork, just like upgrading the consensus rules. This provides a controlled, governance-based path for evolution, not a free-for-all.
In essence, security moves up the stack. It relies less on the VM's isolation and more on the cryptographic correctness and economic incentives of the consensus layer to ensure honest execution. For a chain like Dusk with a robust BFT consensus and slashing机制, this is a more appropriate and powerful security model.
V. The New Frontier: What Host Functions Unlock
This architecture is not an incremental gain. It enables new categories of applications:
Real-Time Confidential DeFi: Complex financial instruments like options or swaps can be settled privately. The payoff logic (WASM) can verify a ZK proof (host function) that the underlying Phoenix-based asset moved, all within a single block finality window.
On-Chain Identity & Reputation Systems: The Citadel protocol for licenses can use native BLS multi-signatures for decentralized attestations, making on-chain KYC/AML checks fast and cheap enough for per-transaction use.
Light Client Verifiability: Because ZK proof verification is so cheap, light clients can verify the entire state transition of a complex application (like a Zedger security token) by checking a single, small proof, enabling trustless mobile trading of private securities.
Cross-Chain Privacy Bridges: Efficient native verification of proofs (e.g., using Groth16 for Ethereum-state proofs) allows for trust-minimized bridges where assets can be moved onto Dusk and instantly wrapped in Phoenix confidentiality.
Conclusion: The End of the Compromise
For years, blockchain architects have faced a brutal compromise: generality vs. performance. You could have a general-purpose VM (flexibility) or a domain-specific chain (speed). You couldn't have both without sacrificing security.
Piecrust and its host-function model shatter this compromise. It offers a hybrid architecture: the generality and developer familiarity of a WASM-based, Turing-complete smart contract environment, married to the raw, native performance of a domain-specific processor for cryptography.
For Dusk, this is the final piece of the puzzle. Phoenix provides private value transfer. SA Consensus provides fast, final settlement. Zedger provides compliant financial logic. And Piecrust is the high-performance runtime that makes it all execute not just correctly, but with the speed and efficiency that global finance requires. It’s the proof that in the next generation of blockchain, the most critical optimization won't be in the consensus algorithm, but in freeing the smart contract from its own virtual machine.