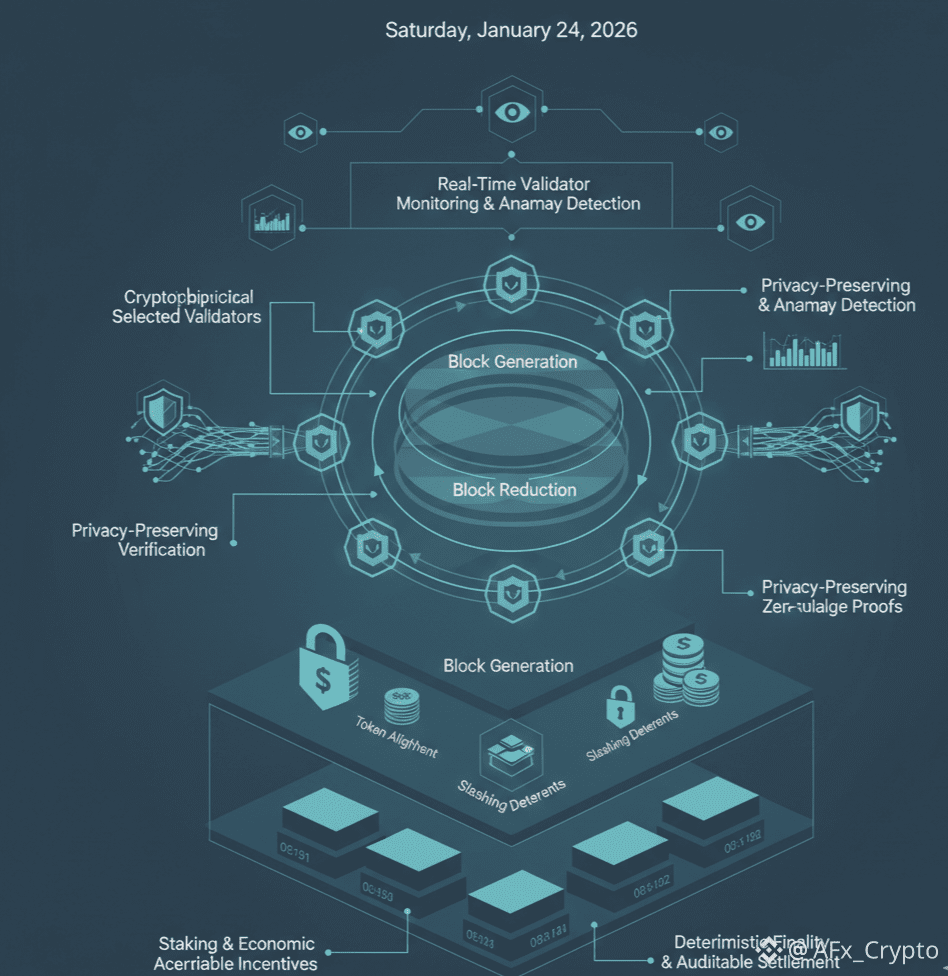
Dusk Network integrates a multi-layered approach to security, designed to detect and respond to unusual validator behavior in real-time while maintaining privacy and deterministic finality. By combining a unique consensus protocol with economic incentives and cryptographic verification, Dusk provides a secure and trustworthy environment for financial-grade decentralized applications.
Segregated Byzantine Agreement (SBA) Protocol
At the core of Dusk Network is the Segregated Byzantine Agreement (SBA), an advanced consensus mechanism that extends traditional Proof-of-Stake protocols. SBA is structured to enhance both decentralization and security by privately and randomly selecting validators for each block through cryptographic sortition. This method makes it extremely difficult for attackers to target specific nodes or form colluding cartels.
The consensus process occurs in three distinct phases: Block Generation, Block Reduction, and Block Agreement. Each phase verifies block validity, validator honesty, and fairness, ensuring that blocks are produced with integrity and that no single participant can dominate the process. By combining cryptographic randomness with structured verification, SBA strengthens resilience against malicious behavior while promoting distributed governance.
Economic Security through Staking
Dusk enforces economic security by requiring validators to stake DUSK tokens. This stake aligns validator incentives with network integrity: honest behavior is rewarded, whereas misbehavior triggers penalties. Validators attempting to manipulate blocks, censor transactions, or engage in other attacks face slashing of their staked tokens, creating a financial deterrent against fraud. This combination of technical and economic safeguards underpins the network’s reliability and trustworthiness for financial use cases.
Finality by Design
For institutions and financial applications, certainty and irreversibility are critical. Dusk achieves this through finality by design, meaning once a block is finalized, it cannot be reverted. This removes the risk of chain reorganizations (reorgs) and ensures that settlements are deterministic and auditable. By eliminating ambiguity, Dusk provides the stability needed for regulated environments and high-value transactions.
Privacy-Preserving Verification
Dusk’s privacy-first approach allows validators to confirm the correctness of transactions without accessing sensitive information, such as user balances or identities. This is accomplished through zero-knowledge proofs (ZKPs), which verify compliance with protocol rules without revealing underlying data. By limiting the information available to validators, the network reduces the attack surface and prevents targeted exploits, even from malicious nodes.
Continuous Monitoring and Incentive Alignment
The network continuously monitors validator behavior, detecting anomalies and preventing malicious actions, such as double-spending or invalid block proposals. In tandem, the DUSK token incentivizes honest participation: validators receive rewards for following protocol rules and penalties for deviations. This real-time monitoring combined with economic incentives ensures that the network maintains a robust, secure, and self-regulating ecosystem.
Conclusion
Dusk Network exemplifies the integration of advanced consensus, economic alignment, privacy, and real-time monitoring to secure decentralized financial systems. The SBA protocol, combined with staking-based economic security, finality by design, and zero-knowledge verification, provides a layered defense against malicious validators while preserving user confidentiality. By proactively detecting irregular behavior and enforcing incentives for honesty, Dusk positions itself as a privacy-conscious, institution-ready blockchain, capable of supporting high-integrity DeFi applications, confidential smart contracts, and regulated on-chain settlements.