 MEV is not a bug. It’s a consequence of visibility.
MEV is not a bug. It’s a consequence of visibility.
Most blockchains treat transaction transparency as a virtue. Mempools are public, execution paths are observable, and ordering logic is predictable. This openness enables composability but it also creates a permanent extraction layer.
Front-running, sandwich attacks, priority gas auctions these are not exploits. They are rational behaviors in systems where future state is visible before it is finalized.
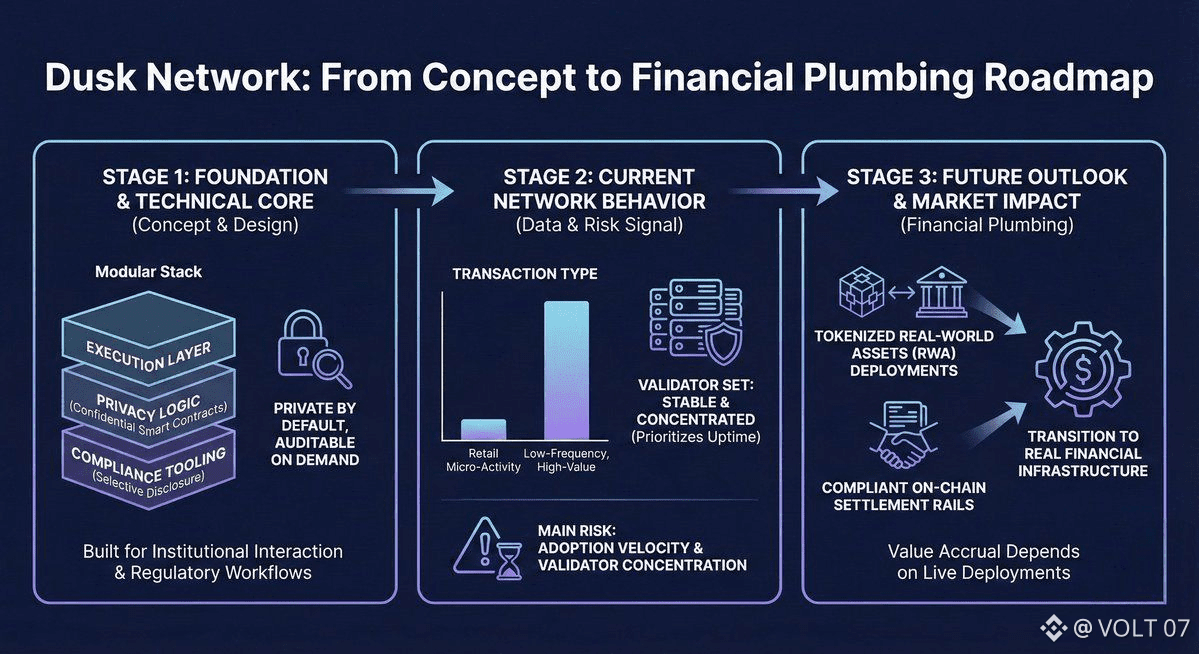
Dusk Network approaches the problem from a different angle:
If value is extracted because information is visible, what happens when that information never exists in the first place?
Why MEV exists in transparent execution environments
MEV thrives on three signals:
visible pending transactions,
predictable execution ordering,
observable state transitions.
When validators or searchers can see what will happen before it happens, they can reorder, insert, or censor transactions to extract profit.
No amount of moral framing changes this.
As long as the signals exist, MEV will exist.
Privacy removes the raw material MEV depends on
Dusk does not try to regulate MEV behavior. It removes the conditions that make it possible.
In Dusk’s privacy-preserving design:
transaction contents are hidden,
execution logic is shielded,
state transitions are not publicly inferable,
validator participation is opaque.
Without visibility into intent or outcome, front-running becomes guesswork not strategy.
MEV dies not by enforcement, but by information starvation.
Front-running fails when intent is unknowable
Front-running depends on knowing what a transaction will do:
Is it a large swap?
Will it move price?
Does it unlock arbitrage?
In Dusk:
transaction parameters are private,
contract logic executes confidentially,
intermediate states never appear in the clear.
Even if a validator wanted to front-run, they lack the informational edge required to do so. The economic incentive collapses.
Why private execution matters more than private settlement
Some chains hide balances but expose execution. That only shifts MEV upstream.
Dusk treats execution itself as the sensitive surface:
smart contract logic runs inside a privacy boundary,
proofs attest to correctness without revealing steps,
finality reveals that a valid transition occurred not how.
This is critical. MEV is extracted during execution, not after settlement.
MEV resistance without auctions, committees, or trust
Many MEV-mitigation strategies introduce new complexity:
off-chain order flow auctions,
trusted sequencers,
committee-based ordering,
social norms enforced by governance.
These approaches relocate trust they don’t eliminate extraction.
Dusk’s approach is simpler and more robust:
no visible order flow,
no interpretable intent,
no extractable advantage.
When there is nothing to see, there is nothing to exploit.
Why this protects users, not just protocols
MEV is often framed as a validator problem. In reality, it’s a user tax:
worse execution prices,
unpredictable outcomes,
hidden fees embedded in ordering,
loss of fairness for non-insiders.
By removing MEV at the design level, Dusk restores a basic property users expect from financial systems:
the outcome of a transaction does not depend on who sees it first.
Privacy changes the economic game, not just the UX
In transparent systems, rational actors optimize extraction.
In privacy-preserving systems, rational actors optimize correctness.
Dusk aligns incentives so that:
validators gain nothing from manipulation,
searchers have no signal to exploit,
users are not competing against unseen adversaries.
This is not idealism. It is incentive engineering under constrained information.
Why this matters as DeFi grows up
As DeFi moves toward:
institutional participation,
regulated financial instruments,
predictable execution guarantees,
MEV stops being a tolerated nuisance and becomes a deal-breaker.
No serious financial system accepts a market where intermediaries can see and reorder intent for profit. Privacy-preserving execution is not optional at that stage it is foundational.
Dusk is built for that future.
Most chains try to manage MEV. Dusk prevents it from forming.
Managing MEV assumes extraction is inevitable.
Dusk chooses the harder path: removing the conditions.
I stopped asking how MEV is mitigated. I started asking what MEV can still see.
On Dusk, the answer is simple: almost nothing that matters.
That is why privacy-preserving design is not just about confidentiality. It is about fairness, predictability, and restoring user trust in execution.

