The core problem with public ledgers isn’t speed or cost. It’s visibility. They never learned how to separate the right to verify from the right to see. Every time a regulated asset moves on a transparent EVM chain, the entire business context leaks with it. Balances, timing, counterparties, even intent. You prove honesty by exposing strategy. For institutions, that trade-off is unacceptable, and Dusk exists precisely because of that failure.
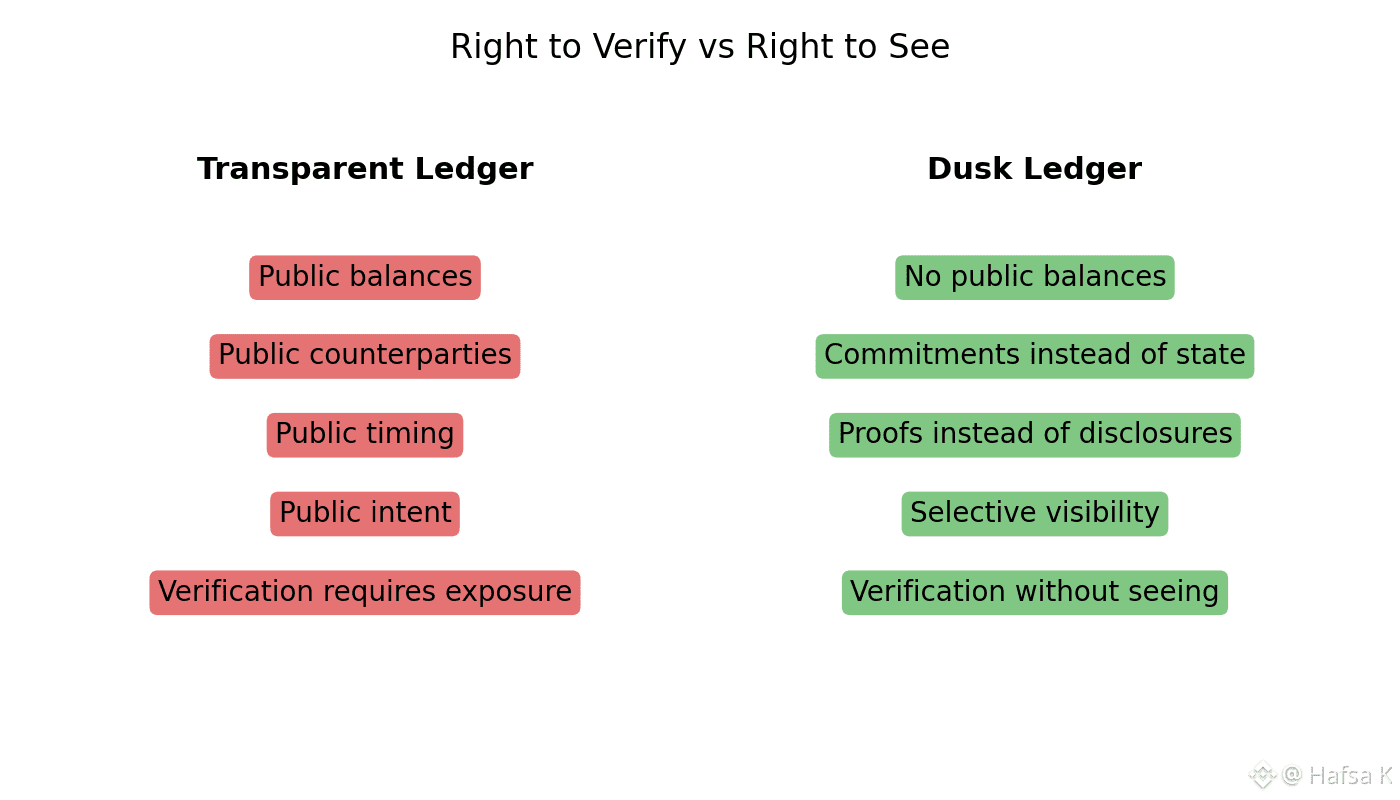
On Dusk, the question isn’t “how do we hide data later?” It’s “how do we prevent sensitive data from ever entering public state?” That distinction drives everything. Phoenix doesn’t wrap a public balance in encryption. It removes the idea of public balances entirely. Ownership becomes a cryptographic commitment. When a Phoenix transaction happens, validators don’t see amounts, identities, or asset movements. They only see a proof that a valid commitment was spent and replaced correctly. No state is revealed because no readable state exists.
I noticed this most clearly earlier today while sitting in a café, watching a barista handle prepaid coffee cards. She never checks how much money someone has overall. She only checks whether the card is valid for the drink being ordered. That’s it. If coffee cards worked like ERC-20s, everyone in line would see each customer’s entire spending history flash on a screen. Absurd in real life. Normalized in crypto. Dusk fixes that by design.
This philosophy runs straight through DuskDS. It doesn’t just store state. It controls who can know what about that state. Because Dusk is built for regulated assets, privacy alone isn’t enough. Moonlight turns compliance itself into a zero-knowledge problem. A transaction can prove that a holder is eligible, accredited, or jurisdiction-compliant without revealing who they are or what else they own. The proof is the permit. The validator verifies math, not identity.
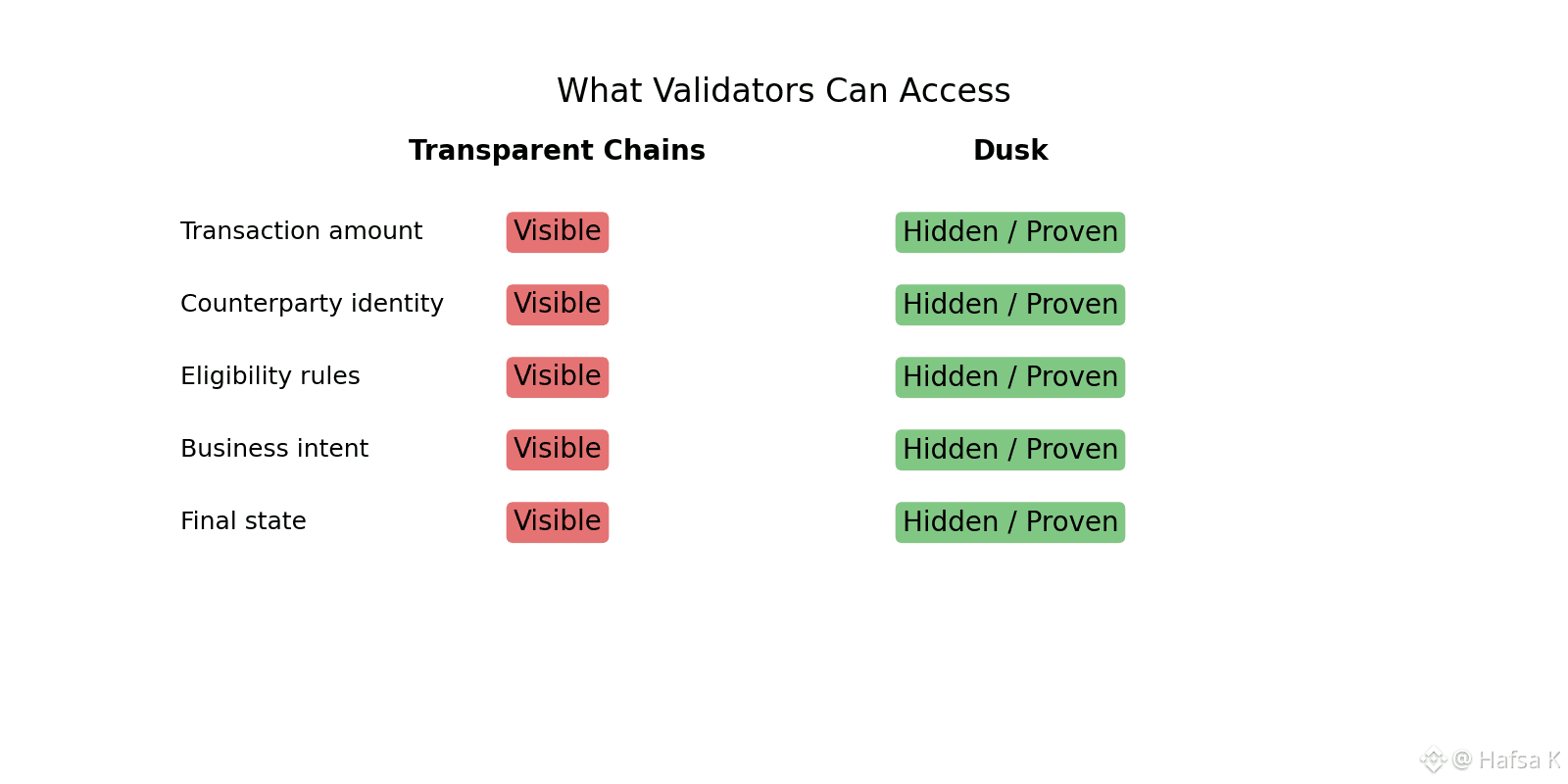
Take a regulated bond issued on Dusk. The issuer defines constraints at deployment: who can hold it, concentration limits, transfer conditions. On a transparent chain, those rules sit in a visible whitelist that anyone can scrape. On Dusk, they live inside the zero-knowledge circuit. When a secondary trade happens, the buyer submits a proof that they satisfy all constraints. Validators check the proof and move on. Regulators can later confirm that every trade was compliant, but they never see the trading graph unless legally required.
What makes this work in practice is Hedger. Hedger sits between DuskEVM execution and the settlement layer, translating smart contract logic into proofs that Phoenix and Moonlight can enforce privately. Validators never see mempool intent. They never see trade size. They never see liquidation thresholds. They verify correctness and finalize state. That blindness matters. On transparent PoS chains, validators and searchers extract value precisely because they can see everything. On Dusk, there’s nothing to extract.
I was reminded of this last week watching a liquidation cascade on another chain. Large positions were visible hours before they blew up. Bots lined up. Front-running became inevitable. The exploit wasn’t clever. It was structural. On Dusk, that scenario simply doesn’t materialize. The data required to run those strategies never appears in public memory.
This invisibility isn’t free. Proof generation costs real computation. Users and developers feel it first. A Phoenix transaction isn’t just a signature; it’s cryptography. Devices do more work. Contracts require careful circuit design. Developers coming from copy-paste Solidity environments hit a wall quickly. On Dusk, you aren’t just writing logic. You’re defining what the world is allowed to know.
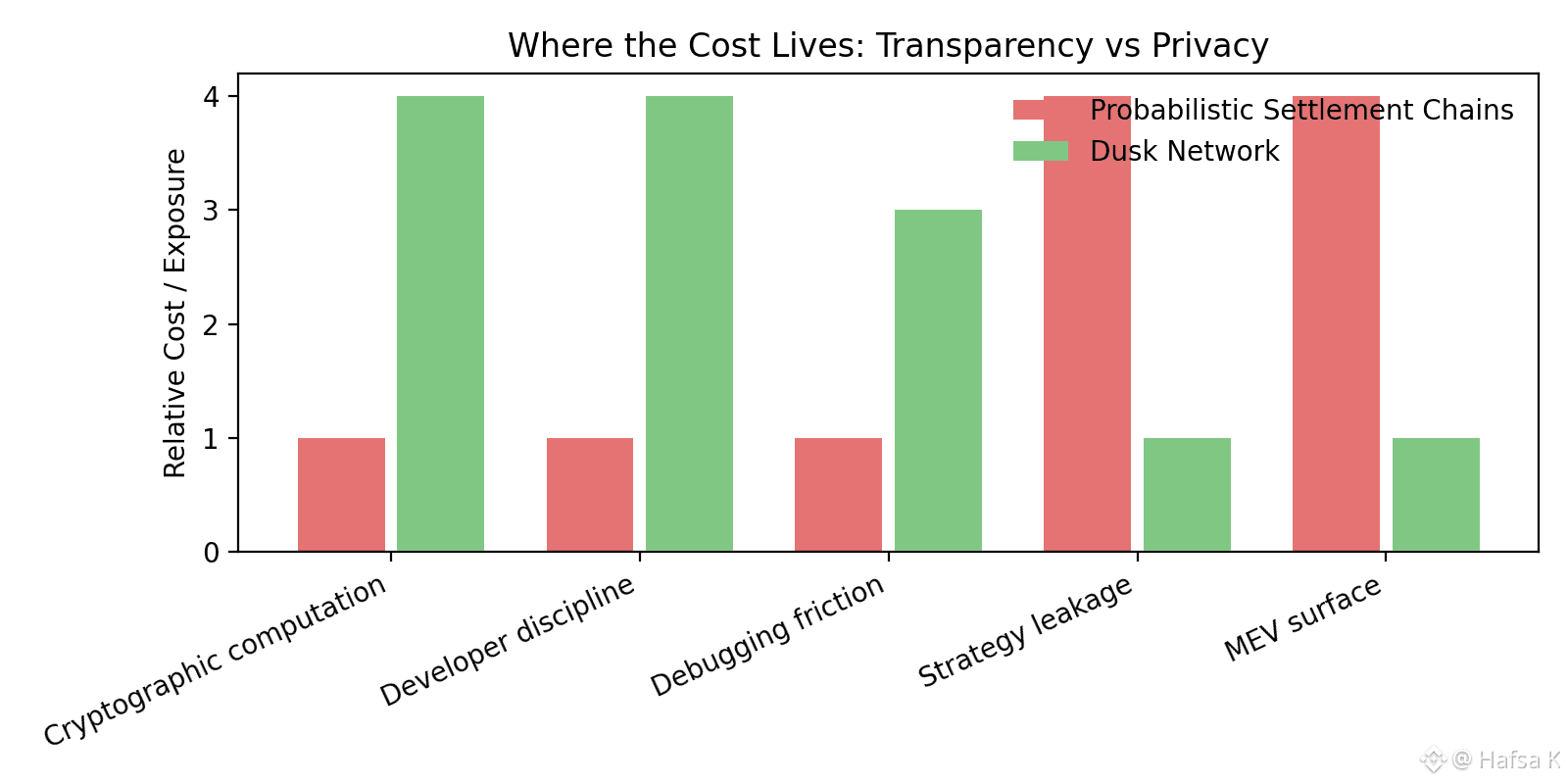
There’s another trade-off too. Debugging feels different. You can’t inspect state directly because state isn’t visible. Tooling is improving, but it demands a mindset shift. I’ve watched capable developers struggle at first, then adapt, then refuse to go back once they realize they no longer leak strategies just to test functionality.
From a validator’s perspective, the architecture is equally strict. DuskDS combined with Phoenix means validators operate in the dark by default. They participate in consensus, verify proofs, and finalize blocks without understanding transaction content. That removes MEV at the root. It also raises the bar for validator reliability. You can’t cut corners when finality and privacy are coupled.
For auditors and custodians, this is where Dusk becomes practical rather than theoretical. They don’t need to trust off-chain agreements or legal wrappers to keep data confidential. Viewing keys allow selective disclosure after the fact. A regulator can inspect exactly what they’re entitled to, no more, no less. The chain itself never becomes a permanent data leak.
Most systems try to patch transparency with policy. Dusk changes the ledger itself. Sensitive information never enters public state. There’s nothing to redact later. Nothing to hide retroactively. The protocol refuses to write secrets to disk in the first place.
As the day winds down, that distinction keeps resurfacing. We’ve spent years assuming trustlessness requires total exposure. Dusk quietly argues the opposite. That trust, especially in regulated finance, comes from math that lets verification happen without visibility.
The ledger doesn’t need to see everything. It just needs to know what is true.