The Dusk Network has been flying under the radar over the past few months but has more recently been generating quite a bit of interest.
It is flying hot off the heels of a recent Binance listing and trading volumes reflect this. The project is trying to take the concept of privacy based blockchains and bring it to the world of digital securities and STOs.
Yet, is all this hype overdone?
In this Dusk Network review, I will give you everything you need to know about the project. I will also look at the long term potential and use cases for DUSK tokens.
What is the Dusk Network?
The Dusk Network is a privacy blockchain that is focused on the issuance of digital securities, aiming to make trading compliance automatic, while maintaining individual user privacy and auditability. According to Jelle Pol, business lead of the project:
Dusk Network was created to digitize regulated (financial) markets. Built from the ground up to tackle the challenge at the deepest layer
The protocol combines a custom-built consensus mechanism and zero-knowledge cryptography to provide both compliance and confidentiality. The goal is to create a platform that removes the expensive middlemen found in traditionally regulated markets but still maintain regulatory approval.
The Dusk Network has recently moved to a public testnet and has plans on becoming a blockchain protocol that allows for easy deployment of Zero-Knowledge dApps, which would make it the backbone of a global, permissionless dApp ecosystem.
The Dusk Network Goals
Dusk was created for use in the financial industry, with a combination of necessary privacy and compliance with regulations.
While there are several potential use cases for the Dusk Network, the primary initial adoption strategy is focused on the Security Token (STO) market, which they feel will benefit from the addition of a privacy and compliance-focused blockchain built specifically for the needs and challenges of the STO space.
In order to become the primary blockchain used for STOs, it is critical for the team to provide for both the privacy of transactions and compliance requirements. Privacy of transactions is one of the key elements of regulated markets.
Consider the following example: Any large movements of Bitcoin from various whale wallets can cause huge spikes in Bitcoin volatility, either upwards if there is a large purchase, or downwards when there is a large sale. If Bitcoin were a regulated asset like a stock, the transparency of the blockchain and transactions would be not only discouraged by regulators but could also be considered as leading to market manipulation, a practice that is illegal in any regulated market.
Benefits of Dusk Network. Image via Dusk Website
While the privacy of transactions is important in maintaining an orderly market, compliance is equally important in legal market trading. This means checks for traders such as KYC and AML, which combat money laundering, as well as restrictions on the country of residence, amount of assets being issued, whether assets can be fractional, and other details of a healthy asset market.
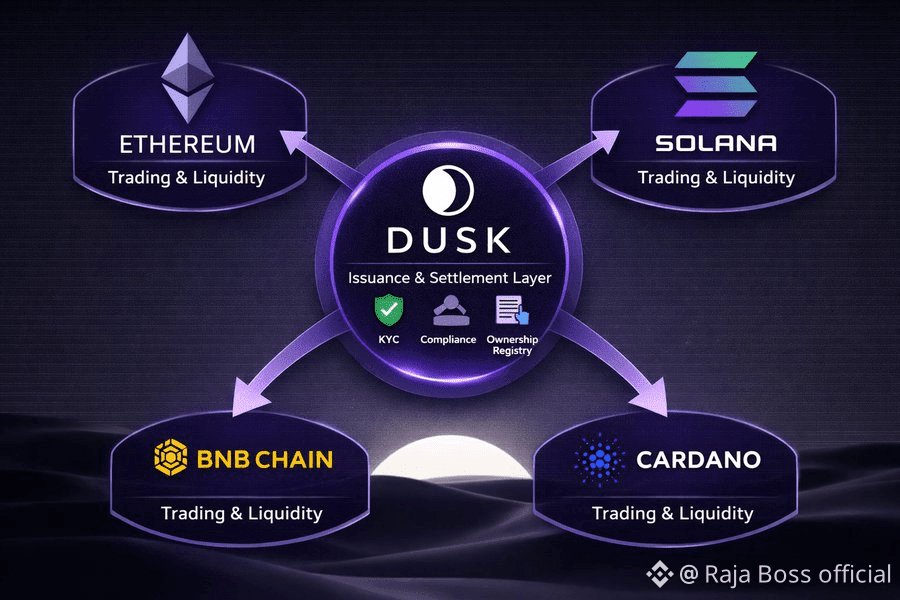
It’s important to know that as a layer 0 protocol the Dusk Network differs from other similar solutions such as PolyMath which acts like a for-profit middleman in the STO market, which need to charge fees and make money to be successful.
When you use those platforms you must also pay the fees, which can run into the hundreds of thousands of dollars for new STO campaigns. In contrast, the Dusk Network is a protocol which makes their security token standard open to all, just like the ERC-20 standard on Ethereum was open to all for use in their ICOs.
That makes Dusk free to use, which is a vast improvement for projects looking to launch an STO.
Dusk Network and Zero-Knowledge
The Dusk Network makes use of Zero-Knowledge cryptography as a means for validating a wide variety of network operations. This includes transactions, right to access a service, right to participate in blind bidding auctions and much more.
In addition, using zero-knowledge cryptography means users can participate without revealing their identity or any details of transactions while providing proof of correct computation in a trustless manner. All of these verifications are handled by browser nodes.
Blind Bind on the Dusk Network. Image via Blog.
These nodes compete with each other by staking an undisclosed amount of Dusk tokens to participate in the block selection process. This generates compliance to the process as it generates the zero-knowledge proof that transactions in the block have occurred.
The shifting of the workload of verifying (and eventually generating) zero-knowledge proofs allow the community to add computational power, thus leveraging game theory principles and bringing Dusk one step closer to becoming fully browser-based.
Privacy Features
Dusk uses a wide variety of technologies to maintain privacy in the network while also minimizing the potential for data breaches or transaction and account detection. The list of features used includes:
Stealth Addresses;
Ring Confidential Transaction Signatures;
An Anonymous Network Layer;
Non-Interactive Verifiable Secret Sharing;
Cryptographically Committed Provisioners;
A Segregated Byzantine Agreement (SBA) consensus algorithm.
All of which is incorporated into a low-latency gossip network using garlic routing and a non-repliable datagram to prevent occurrences of IP address propagation.
The entire network is secured with the Segregated Byzantine Agreement consensus protocol. The SBA protocol is a permission-less algorithm that includes statistical block finality.
Overview of the Dusk Network Consensus
It also includes the unique Proof of Stake consensus known as Proof of Blind Bid, which allows block generators to stake tokens anonymously. SBA compliments many of the ideas first introduced by the Byzantine Agreement consensus including the concept of stealth time-locked transactions to protect from Sybil attacks.

