Dusk has been around since 2018, and it feels like it was built by people who’ve seen how regulated finance actually behaves: quietly, carefully, and with a strong preference for not turning sensitive activity into a public broadcast. Real markets aren’t private because they’re hiding—they’re private because information moves prices, positions reveal strategy, and client data is not a spectator sport. At the same time, regulated systems can’t live on “trust me.” They live on audits, controls, and proofs. Dusk’s whole identity is trying to make those two instincts—confidentiality and accountability—stop arguing.
On its base layer, DuskDS, privacy isn’t treated like a bolt-on cloak. It’s treated like a built-in choice. The network supports two native transaction styles: one that’s openly readable and one that’s shielded using zero-knowledge proofs, both settling to the same ledger. That matters because regulated finance is rarely “all public” or “all private.” It’s mixed, depending on what’s being moved, who’s involved, and what the rules require. Dusk’s design is basically saying: you can keep the details quiet without breaking the system’s ability to settle truth.
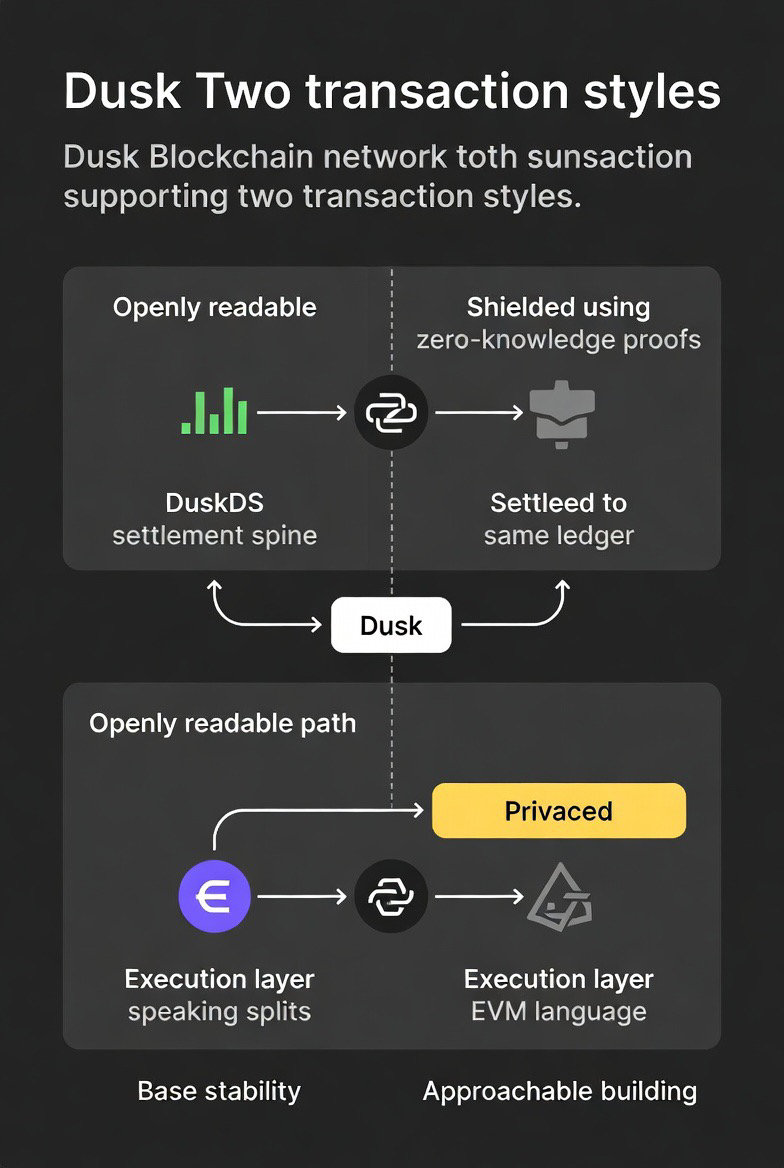
What makes the architecture feel serious is the way Dusk separates responsibilities. DuskDS is positioned as the settlement spine—finality, consensus, data—and above it sits an execution layer that speaks the EVM language developers already know. That modular split is not just technical neatness; it’s a social strategy. Institutions don’t want a fragile foundation, and developers don’t want to abandon familiar tooling. Dusk’s stack tries to keep the base stable while making the “build” layer approachable.
The interesting part is that Dusk’s privacy story doesn’t stop at transfers. In finance, the sensitive thing is often the logic: eligibility rules, restrictions, conditional outcomes, disclosures. Dusk’s confidentiality engine direction for the EVM world is an attempt to let contracts keep inputs protected while still producing verifiable evidence that the contract ran correctly. It’s the same principle repeated in a new form: keep secrets, but don’t lose the receipts.
Identity gets the same treatment. Regulated systems need to know participants are eligible, but it’s risky to scatter raw personal data across every app and platform. Dusk’s ZK-based identity approach aims to let people prove they meet requirements without handing over their whole personal file each time. It’s less “upload everything,” more “prove what’s needed.”
Recent updates show how this mindset plays out when things get inconvenient. In January 2026, Dusk paused bridge services after unusual activity tied to bridge operations while emphasizing the base chain itself wasn’t impacted. That kind of decision isn’t glamorous, but it’s the behavior you expect from infrastructure: isolate the edge where risk concentrates, protect the settlement core, and harden the system before reopening traffic.
If you want a simple mental image for Dusk, picture a building made of smart glass. From the outside, you can verify the structure and the rules. Inside, sensitive financial activity doesn’t have to be exposed to the world. And when legitimate oversight is required, visibility can be granted precisely—only what’s necessary, only to authorized parties—so privacy doesn’t become a loophole and auditability doesn’t become surveillance.
