One night I opened @Dusk Network explorer just to watch the block rhythm and a few validator addresses doing their quiet work, the kind of habit you develop to calm the nerves, and I caught myself wondering why I still care about something as “dry” as consensus after all these years.
If you’ve lived through enough cycles, you learn that most projects don’t die because they lack memes or a compelling story, they die because the operating layer underneath can’t survive the first day real users show up.
With Dusk, I think the part worth scrutinizing isn’t the “confidential finance” slogan or the usual promises about the future, but how they design validator power and how they reduce the attack surface once the network starts carrying real value. Here, consensus isn’t “a module”, it’s an operational culture.
Dusk describes its consensus as a committee oriented proof of stake mechanism called Succinct Attestation, running in rounds with voting phases before a block is accepted. But what made me slow down wasn’t just the name, it was how they separate roles inside consensus.
In the whitepaper, they talk about Segregated Byzantine Agreement, where the block proposer and the block finalizer are two different roles: the Generator proposes, the Provisioner validates and finalizes. The leader is “drawn” through a dedicated procedure called Proof of Blind Bid, while the Provisioner committee is selected via sortition.
Honestly, I’ve always liked designs that deliberately make power harder to concentrate, because concentration is what the market loves, and what security tends to hate.
There’s something truly ironic here. A lot of chains claim decentralization, yet their mechanisms quietly encourage people to “know in advance who’s steering the wheel”, and once you can predict that, every attack, every lobbying campaign, every backroom deal suddenly has a clear target.
In Dusk’s description, a more private leader selection and a round based committee make the question “who do we hit” harder to answer. I’m not saying it’s a magic shield, but from a security intuition standpoint, it raises the cost of attack by a notch, especially for tactics that target proposers or try to buy off a small, stable group.
But consensus on paper doesn’t save a network if validators in real life operate on “we’ll see today when we get there”. And this is the part I look at through a builder’s lens: economic incentives and operational discipline.
The DUSK token is used both for staking into consensus and for paying network fees, and they describe a multi year emission schedule to keep the security budget alive when fee revenue still isn’t enough.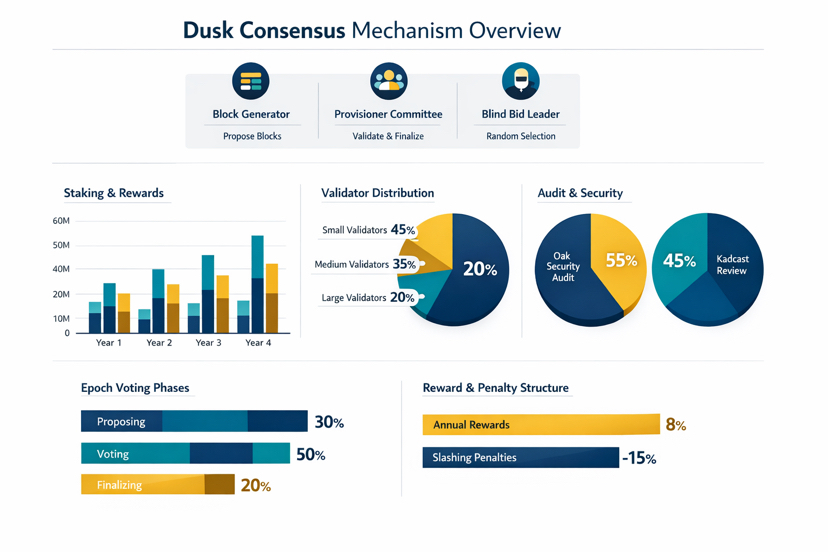
Maybe the most important question isn’t what the APY looks like, but whether the reward and penalty structure can form a validator set that’s wide enough and durable enough that the system doesn’t end up relying on a handful of “too big” operators. I’ve watched too many networks fall into the same trap: high rewards attract participation when there’s no volume, then once volume arrives, power has already concentrated, and governance becomes mostly theater.
On the security side, I no longer believe in the feeling of “we write great code”. What I believe in is process and audits, because even great engineers get tired, get complacent, and eventually have a day when they miss something.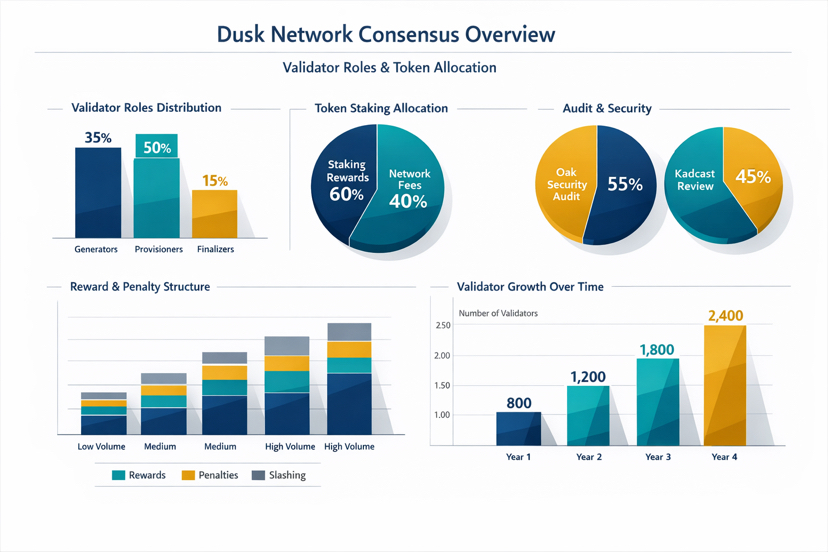
Dusk has published that their consensus and economic protocol were audited by Oak Security. They have published materials and audits with regards to Kadcast, which is related to data propagation. This is something that most people don’t think about until the network is congested and every “synchronous” assumption is broken. It’s surprising that something as simple as propagation or votes slowing down can cause an otherwise beautiful system to become a terrible user experience. A terrible user experience leads to terrible capital.
The biggest thing Dusk reminds me to keep in mind is that in crypto, security is not just cryptography or algorithms, security is how you manage uncertainty. Security is how you separate, how you form committees, how hard you make targeted attacks, and most importantly, security is how you grow a validator layer that survives boring times. And if you remove all narrative, what is left to give you trust is operational security in consensus and maturity in your validator set, and so how will Dusk keep that operational security when it finally faces real loads and real pressures.