Introduction
Dusk Network was founded in 2018 to build regulated, privacy-focused financial infrastructure. As decentralized systems mature, one challenge keeps resurfacing: how to scale storage without sacrificing security or decentralization. Traditional decentralized storage networks often bundle data storage and control logic into a single layer. This tight coupling creates bottlenecks, raises attack surfaces, and limits performance.
A newer architectural approach separates data storage from control logic. Instead of forcing one system to do everything, storage networks specialize in holding and retrieving data, while blockchains act as neutral coordination and verification layers. This separation mirrors how modern internet infrastructure evolved—distinct layers optimized for distinct tasks. For decentralized finance and institutional applications, this modularity is not optional; it is foundational.
Problem with the Traditional Monolithic Model
In monolithic decentralized systems, storage and control logic share the same execution environment. Every node is responsible for validating transactions, executing smart contracts, and storing large volumes of data. While this design simplifies early development, it becomes inefficient at scale.
First, performance suffers. When nodes must replicate and verify massive datasets, network throughput drops. Storage-heavy workloads compete with computation-heavy tasks, creating congestion and higher operational costs. This is especially problematic for institutional financial applications that require predictable latency and reliability.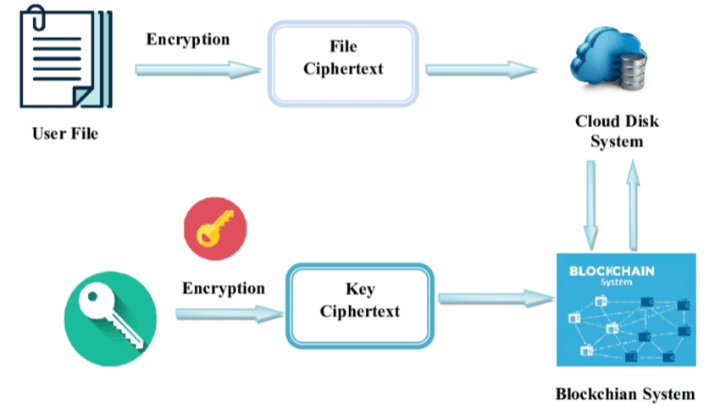
Second, security risks compound. A monolithic architecture concentrates responsibilities in a single layer. If vulnerabilities appear in storage handling or execution logic, attackers gain broader leverage over the system. The lack of separation also makes auditing harder, since storage and logic interactions are deeply intertwined.
Finally, decentralization weakens over time. As hardware requirements increase, fewer participants can operate full nodes. This leads to implicit centralization, where only well-funded operators can maintain infrastructure. For regulated and privacy-sensitive ecosystems like those envisioned by Dusk, such centralization undermines both trust and compliance.
Benefits of Separating Data Storage and Control Logic
Decoupling storage from control logic introduces architectural clarity. Each layer can be optimized independently, producing measurable gains in scalability, security, and operational resilience.
From a scalability perspective, specialized storage networks can focus on efficient data distribution techniques such as erasure coding and sharding. Meanwhile, the control layer processes transactions and verification without being burdened by heavy storage replication. This division allows throughput to scale horizontally: storage capacity grows with dedicated storage nodes, while computation scales with validator nodes.
Security also improves through isolation. By limiting the responsibilities of each layer, the system reduces the blast radius of potential failures. Storage faults do not automatically compromise consensus logic, and vice versa. This modularity simplifies auditing and enables targeted upgrades without destabilizing the entire network.
In real-world deployments, separation enhances robustness. Enterprises can integrate decentralized storage while maintaining strict performance guarantees. Privacy-preserving financial applications benefit from clearer trust boundaries, where sensitive computation occurs under controlled conditions and storage remains verifiable yet distributed. The result is an infrastructure stack better aligned with institutional requirements and long-term sustainability.
Role of Blockchain as a Neutral Control Authority
In a separated architecture, the blockchain functions less as a storage engine and more as a neutral coordination authority. Its primary responsibilities include consensus, verification, and access control rather than bulk data retention.
This shift is significant. By minimizing on-chain storage, the blockchain maintains lean state sizes, enabling more participants to run validating nodes. A smaller state footprint supports decentralization by lowering hardware barriers to entry. At the same time, cryptographic commitments link off-chain data to on-chain records, preserving integrity without duplicating entire datasets.
For platforms like Dusk, which target compliant financial infrastructure, this model offers an elegant balance. The blockchain enforces rules, auditability, and privacy guarantees, while external storage layers handle scale. Smart contracts reference data through verifiable proofs, ensuring that applications remain both efficient and trustworthy.
Conceptually, the blockchain becomes a global referee. It does not store every detail, but it certifies that the rules are followed. This role aligns with the needs of regulated markets, where neutrality, transparency, and verifiability are essential.
Asynchronous Challenges and Security
Asynchronous challenge mechanisms add another layer of protection and scalability to separated architectures. Instead of forcing immediate validation of every storage operation, the system allows participants to challenge suspicious behavior within defined time windows.
This model distributes verification over time. Storage providers commit to holding data and can be audited through cryptographic proofs. If inconsistencies arise, challengers submit evidence to the control layer, triggering penalties or corrections. Because challenges occur asynchronously, the network avoids constant heavy verification overhead.
The security benefits are twofold. First, malicious actors face economic and reputational risks, discouraging data tampering. Second, honest participants can verify integrity without synchronizing every action globally. This reduces latency and improves throughput while preserving strong guarantees.
Asynchronous challenges also increase resilience. Networks can tolerate temporary outages or delays without collapsing consensus. For large-scale financial systems, where uptime and reliability are critical, this flexibility is essential. It enables decentralized storage to operate at internet scale while maintaining cryptographic accountability.
Conclusion
Separating data storage from control logic marks a decisive evolution in decentralized infrastructure design. By assigning clear roles to specialized layers, systems achieve higher scalability, stronger security boundaries, and deeper decentralization. For privacy-focused financial platforms such as Dusk, this architecture supports institutional demands without sacrificing the core principles of distributed networks.
As decentralized storage continues to mature, modular design will likely become the default rather than the exception. The future of blockchain infrastructure depends not on forcing a single layer to do everything, but on orchestrating multiple optimized layers into a coherent, verifiable whole.