In many Proof-of-Stake systems, slashing is framed as a threat. Misbehave and you lose funds. The logic is blunt, mechanical, and often detached from how real systems fail. Dusk Network takes a noticeably different approach. Slashing in Dusk is not designed as a reflexive punishment. It is designed as a governance instrument—a way to preserve systemic integrity without turning the network into a hostile environment for honest participants.
This distinction matters more than it appears.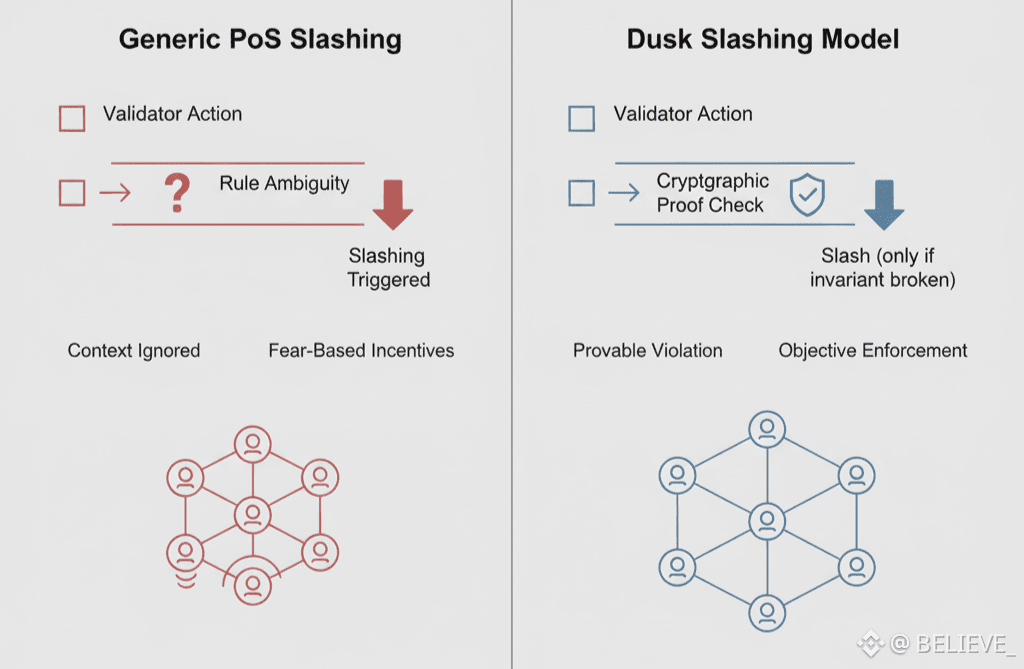
In most networks, slashing rules are rigid and binary. Either an action is slashable or it is not. Context rarely matters. This creates perverse incentives. Validators become overly cautious, avoid participation during uncertain network conditions, or centralize operations to minimize risk. The network becomes safer on paper and weaker in reality.
Dusk avoids this trap by tightly coupling slashing to provable, protocol-level violations, not ambiguous behavior. A slashable offense is not “you might have caused harm.” It is “you cryptographically demonstrated behavior that breaks consensus guarantees.” This removes guesswork from enforcement.
More importantly, slashing in Dusk is externally verifiable. Any participant can submit evidence. There is no privileged enforcer. This transforms slashing from a top-down threat into a collective integrity mechanism. The network polices itself using proofs, not politics.
This design choice reshapes incentives. Provisioners are not constantly guessing whether they are safe. They know exactly which actions cross the line. As long as they stay within protocol rules, they are protected—even if outcomes are unfavorable due to network conditions or adversarial behavior elsewhere.
From a professional systems perspective, this mirrors how fault tolerance works in serious infrastructure. You are not penalized for accidents. You are penalized for violating invariant rules that keep the system coherent.
There is also a subtle but important economic effect. Because slashing is rare, precise, and provable, it retains deterrent power. In networks where slashing happens frequently or arbitrarily, it becomes noise. Participants price it in as an operational cost. In Dusk, slashing remains exceptional—which makes it meaningful.
Another overlooked aspect is who benefits from slashing. In Dusk, reporting a valid slashable offense is incentivized. This creates a decentralized watchdog role without relying on altruism. The reward is not just punishment for the offender; it is compensation for the network’s monitoring effort.
This incentive alignment turns vigilance into a rational activity. Participants are encouraged to care about network health because they are rewarded for defending it. That is a far more sustainable model than hoping everyone behaves out of goodwill.
Crucially, slashing is not tied to identity exposure. Even in a privacy-preserving environment, misbehavior can be proven without revealing unrelated information. This maintains Dusk’s confidentiality guarantees while still enforcing accountability.
This balance is rare. Many privacy-focused systems struggle to enforce penalties without breaking anonymity. Dusk avoids that tension by anchoring enforcement to cryptographic evidence rather than surveillance.
Slashing also plays a role in long-term decentralization. When penalties are predictable and fair, smaller operators can participate without disproportionate fear. They do not need expensive legal teams or custom infrastructure to manage undefined risk. This keeps participation broad rather than concentrated.
The DUSK token’s role here is structural, not speculative. Stake is not just collateral. It is a bond of correctness. When a participant locks DUSK, they are signaling willingness to be governed by protocol rules—not by subjective judgment.
Over time, this creates a culture where correctness is valued more than aggressiveness. Validators are rewarded for steady, rule-compliant participation rather than risky optimization. That kind of culture is difficult to retrofit after launch. It must be designed from the beginning.
What ultimately sets Dusk apart is its refusal to weaponize slashing. It does not use penalties to scare participants into compliance. It uses them to anchor trust in objective proof.
In decentralized systems, trust is not built by assuming everyone is honest.
It is built by making dishonesty expensive, provable, and rare.
Dusk’s slashing model reflects that understanding. It enforces rules without creating fear, accountability without exposure, and governance without central authority.
That is not just good cryptography.
It is good system design.
