Auditors and risk teams are already asking whether a Walrus blob on Sui comes with an onchain chain of custody for availability, instead of a log export that only the storage operator can vouch for. Walrus fits that demand because Proof of Availability ties each blob commitment to a custody trail expressed in Sui state. In Walrus, PoA-related records on Sui can function as the custody log that institutions can verify independently, even when the blob payload stays encrypted and offchain.
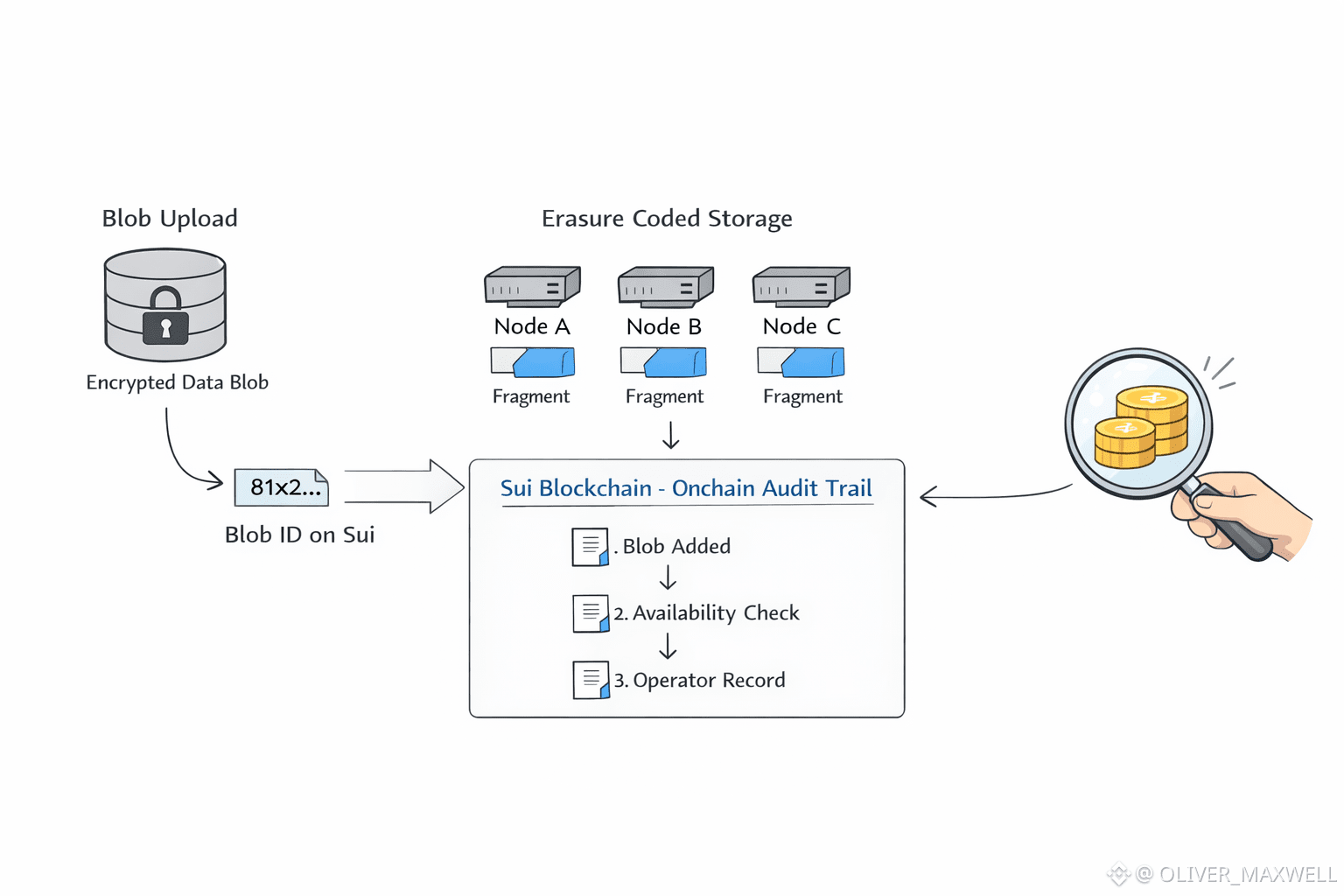
In Walrus, stored means a blob identifier anchored on Sui, erasure-coded fragments held by operators, and a Proof of Availability record that indicates whether the blob remained available under protocol rules. A Walrus blob is split by erasure coding across operators, while a single blob identifier on Sui anchors the custody trail through reassignments and repairs. Walrus leaves payload privacy to application-side encryption, while Walrus exposes cryptographic commitments and PoA-linked availability records on Sui. For Walrus custody, the auditable object is the blob identifier, the operator responsibility around it, and the PoA record that tracks availability over time.
Proof of Availability is where Walrus becomes usable for auditors, because it yields onchain records on Sui that can be checked without relying on operator dashboards. Walrus can require operators, via protocol rules, to produce availability proofs tied to specific blobs, and Walrus can record the resulting proof outcomes on Sui as an ordered history. That history is verifiable from Sui state because Walrus can express custody evidence as onchain commitments and PoA states rather than private compliance reports. WAL staking can tie operator participation and economic commitment to the same custody record that PoA produces, which is what makes availability read like auditable custody behavior instead of a soft service promise.
Erasure coding pushes Walrus to treat fragments, repairs, and redundancy as protocol-level operations that can leave traces in the PoA custody record. Walrus can spread fragments across multiple operators to avoid a single custodian, while the blob commitment on Sui keeps the custody trail coherent across those operators. Because the blob identifier and PoA-linked records live on Sui, Walrus can preserve custody continuity even when individual nodes rotate out, provided the protocol keeps identifiers stable across upgrades. Custody becomes contestable in Walrus when a counterparty can point to the Sui records for a blob and verify whether PoA obligations were met at the times claimed.
This is where Walrus starts behaving like a custody layer, because the audit trail is produced by protocol state, not by an operator’s reporting system. Walrus custody records only serve chain-of-custody workflows when the blob ID, timestamped PoA records, and whatever the protocol reveals about operator responsibility are sufficient for an audit check. In a dispute, Walrus can let parties rely on Sui state for what was committed, when it was committed, and how PoA status evolved, without asking storage operators to certify their own performance. Service agreements can reference PoA records on Sui as evidence of availability windows rather than opaque uptime dashboards.
A public PoA trail on Sui can leak metadata such as timing, blob identifiers, and operator responsibility patterns even if the payload is encrypted. Walrus can reduce that leakage by keeping onchain entries to cryptographic commitments and minimizing descriptive labels, but the visibility of a custody trail remains a design choice. That choice is central to Walrus, because regulated custody demands public evidence even when payload privacy is mandatory. Walrus will be tested at the boundary where application confidentiality rules meet Sui-level custody evidence, especially for teams that must produce audit artifacts without exposing sensitive business context.
For Walrus, the custody label depends on whether PoA stays hard to game under real network stress. PoA must remain meaningful under churn, partitions, and adversarial operators, otherwise the Sui trail becomes a record of claims rather than a record of enforced availability. Repairs and re-encoding in Walrus have to preserve the blob’s Sui identifier and keep PoA obligations tied to the same commitment across fragment reshuffles. Because WAL supports staking and governance, Walrus can attach operator participation to stake-backed commitments that appear in the custody record, and any enforcement evolution will need to show up as protocol rule changes rather than as private policy.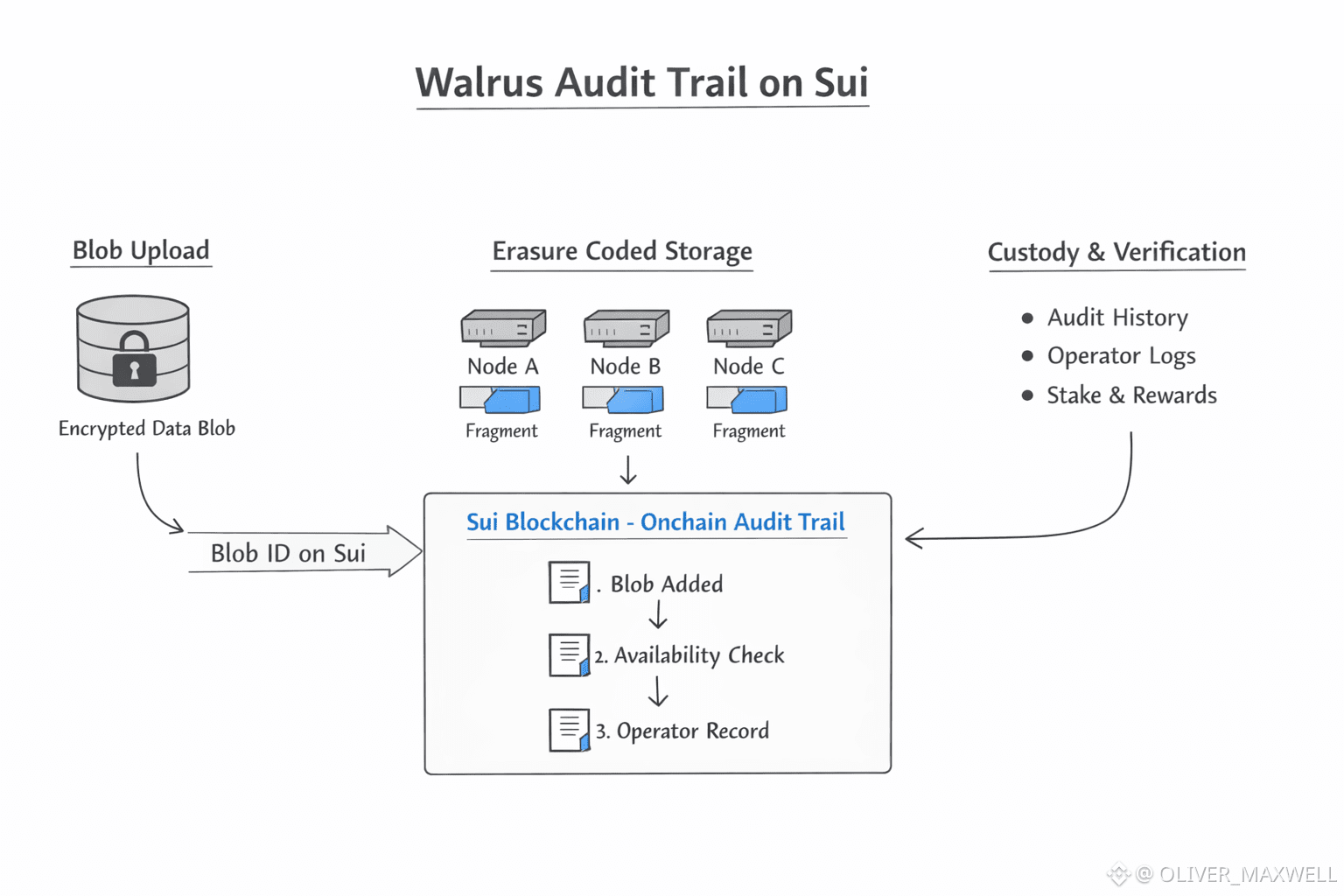
My read is that Walrus looks less like a distributed disk and more like an onchain warehouse receipt for a blob ID on Sui, with Proof of Availability acting as the receipt’s running status. Walrus can show custody as a sequence of Sui commitments and PoA states tied to specific blobs, so an institution can audit availability without granting special access to operators. Because the PoA record is produced by the same protocol rules that shape operator behavior and staking incentives, the audit trail is harder to revise after the fact than a conventional incident report.
As Walrus expands enterprise usage, the differentiator will be whether PoA on Sui reduces audit friction by making custody evidence directly queryable. For regulated applications on Sui, Walrus can offer a blob ID plus a PoA history that supports availability attestations while keeping payload privacy in the application layer, and WAL staking can keep operators economically committed to those attestations over time. Walrus earns its place as infrastructure when its Sui-based PoA trail is strong enough to stand as custody evidence that counterparties can verify and governance can enforce through WAL rules.

