Institutional tokenization and compliant DeFi are now testing whether delegated proving can deliver zero-knowledge privacy without forcing endpoints to generate heavy proofs on consumer phones and thin clients, and Dusk Network is designed around that constraint. On Dusk, privacy is mandatory when counterparties, positions, and cashflow schedules cannot be broadcast, and auditability must still remain defensible. What pushes users away is the computation bill of proving, because the slowest device and the weakest connection become the bottleneck for a private transaction. Dusk’s delegation model matters because it treats the privacy cost as a design input to the user experience, where expensive cryptography is handled as a solvable adoption constraint rather than a hidden tax on every transaction. Dusk’s choice is not a shortcut around security, because a delegated result only helps Dusk if verification remains strict and deterministic on-chain.
Because Dusk bakes privacy and auditability into the base layer, a transaction often carries more than a signature and a balance delta. A privacy-preserving state update must persuade the network that policy rules were satisfied while keeping the underlying facts sealed. Those proof-heavy steps are where Dusk’s UX can fracture, because generating proofs, managing encrypted state, and enforcing selective disclosure can overwhelm typical client devices and stall time-sensitive payment or trading flows. Dusk’s delegation model answers that bottleneck with a simple stance: keep secrets and intent close to the user, move the expensive computation to a delegated execution path, and return an artifact that the chain can verify quickly. Delegation only works on Dusk because validators still verify the returned proof against the transaction’s public commitments before any state update is accepted.
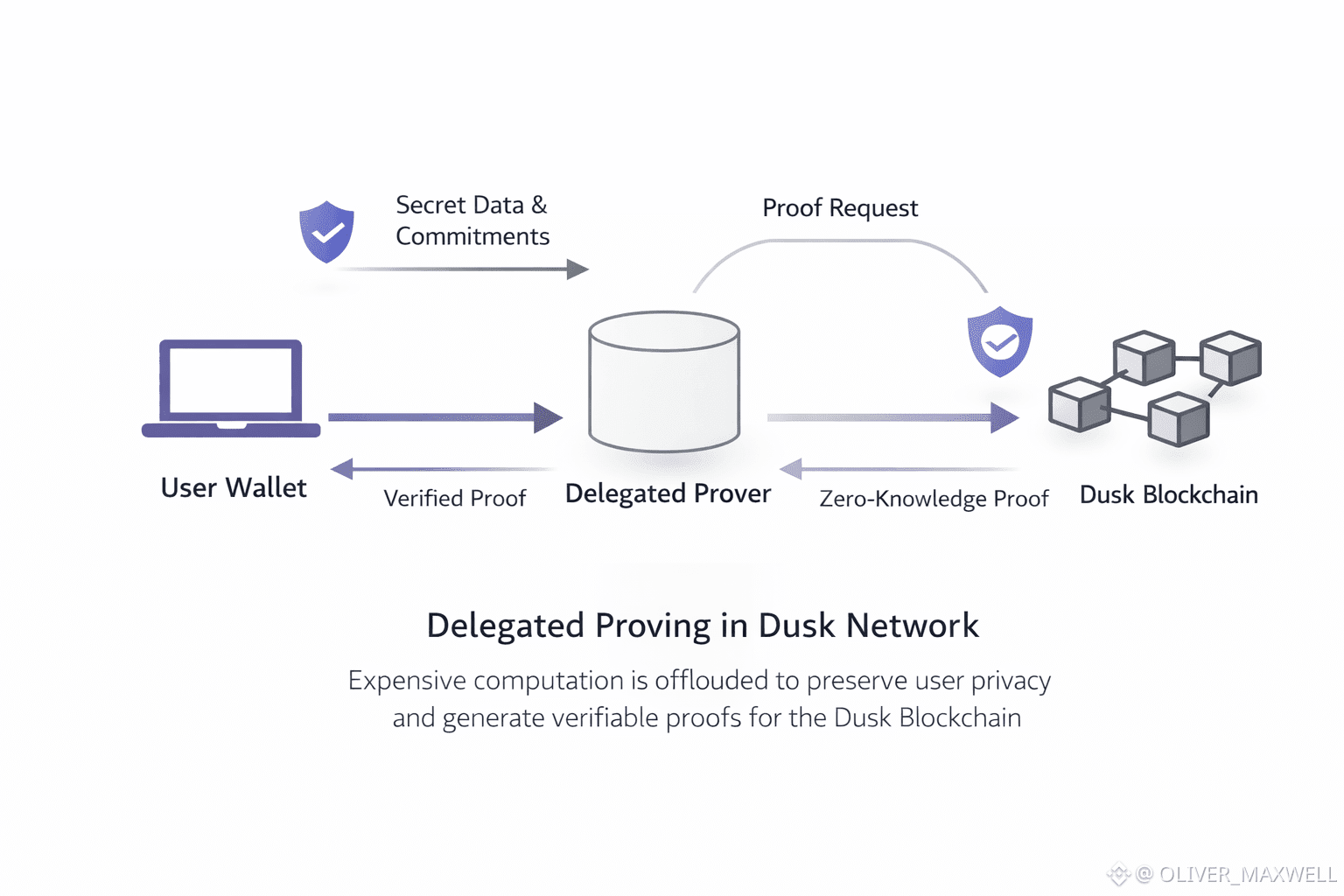
Dusk’s delegation model forces a specific partitioning of responsibility that directly shapes how wallets, institutions, and middleware integrate with the chain. On Dusk, the client can keep the private witness and policy constraints local, then request a delegated prover to compute the heavy zero-knowledge proof over transaction commitments, returning a proof artifact that validators can verify quickly without learning the hidden inputs. The workflow Dusk implies is narrow and strict: the client submits commitments and a proving request outward, receives a proof back, and then broadcasts the proof with the transaction so validation never depends on trusting the prover’s identity. In Dusk, this separation is also what preserves a compliance posture, because auditability can be expressed as selective disclosure rules and verifiable attestations, instead of relying on a blind trust relationship with an off-chain service.
Dusk’s delegation model turns the user experience into an operational question about proof turnaround and recoverability. A Dusk wallet does not need to compute the worst-case proof locally, but it does need predictable behavior when the delegated prover is slow, unavailable, or returns an invalid proof. The moment that matters on Dusk is not a theoretical latency chart, it is what the wallet does after a delegate timeout, how it switches to another prover without re-exposing private state, and how it preserves transaction intent across retries. In Dusk, that usability gain supports the project’s institutional-grade intent, because institutional workflows often depend on predictable latency and operational repeatability, not heroic engineering on every endpoint.
Dusk’s delegation model introduces its own trade-offs, and Dusk cannot pretend those trade-offs are “just implementation details” because they are part of the product surface. In Dusk, delegating expensive computation creates a new trust boundary that must be managed, even when the delegated output is verifiable, because the delegate can still affect availability, pricing, and metadata exposure. In Dusk, a delegated actor can become a de facto gatekeeper if the delegation market is thin, if delegation endpoints are unreliable, or if delegation selection concentrates into a few providers. Dusk’s delegation flow also creates a distinct metadata surface at the handoff point, because wallets must request proofs and receive proofs before submission, and that request-response pattern can leak timing even when the proof reveals nothing. On Dusk, mitigations belong at the wallet and routing layer, including batching requests, padding timing, and rotating delegates, because the privacy budget is spent as much on the handoff behavior as it is on the cryptography.
Dusk’s delegation model is especially interesting under a regulated and privacy-focused mandate because regulated settings already assume the existence of specialized service providers, but Dusk has to prevent that reality from collapsing back into a custodial architecture. In Dusk, delegation should behave like a market for computation that users can switch, replicate, or avoid, rather than a mandatory “privacy server” that quietly centralizes critical path functionality. On Dusk, delegation UX has to include transparent delegate choice and simple failover, otherwise delegated proving becomes a quiet gatekeeper even though validators can verify every proof independently. In Dusk, keeping delegation optional, composable, and verifiable is what keeps the UX solution aligned with the project’s decentralization claims.
My personal read is that Dusk has correctly treated delegation failure modes as part of privacy, not a separate reliability topic. When a Dusk wallet hangs on a prover response, that stall is a user-facing privacy cost because it pressures people into retries, alternate devices, or unsafe shortcuts that leak behavioral patterns. Dusk’s delegation model is valuable because it makes “what happens when the prover is down” a first-order design constraint, rather than an embarrassing edge case that shows up only after launch. Dusk does not get adoption credit for cryptography that works in ideal conditions, and Dusk gets adoption credit when delegated proving remains predictable under failure.
Dusk’s future implications follow directly from this delegation choice, because once Dusk treats computation as a delegated service, Dusk has to standardize how that service is discovered, priced, authenticated, and audited. In Dusk, delegation can become the bridge between compliant DeFi and tokenized real-world assets by making privacy-preserving operations behave like routine API calls rather than rare, fragile events. If delegated proving on Dusk concentrates into a narrow set of providers, operational risk rises in exactly the places regulated deployments tend to watch most closely, such as availability, cost volatility, and continuity planning. Dusk’s delegation model will only stay true to its promise if the prover-client-validator boundary remains verifiable, switchable, and resilient under routine failures, because that boundary is where privacy cost turns into user experience.
