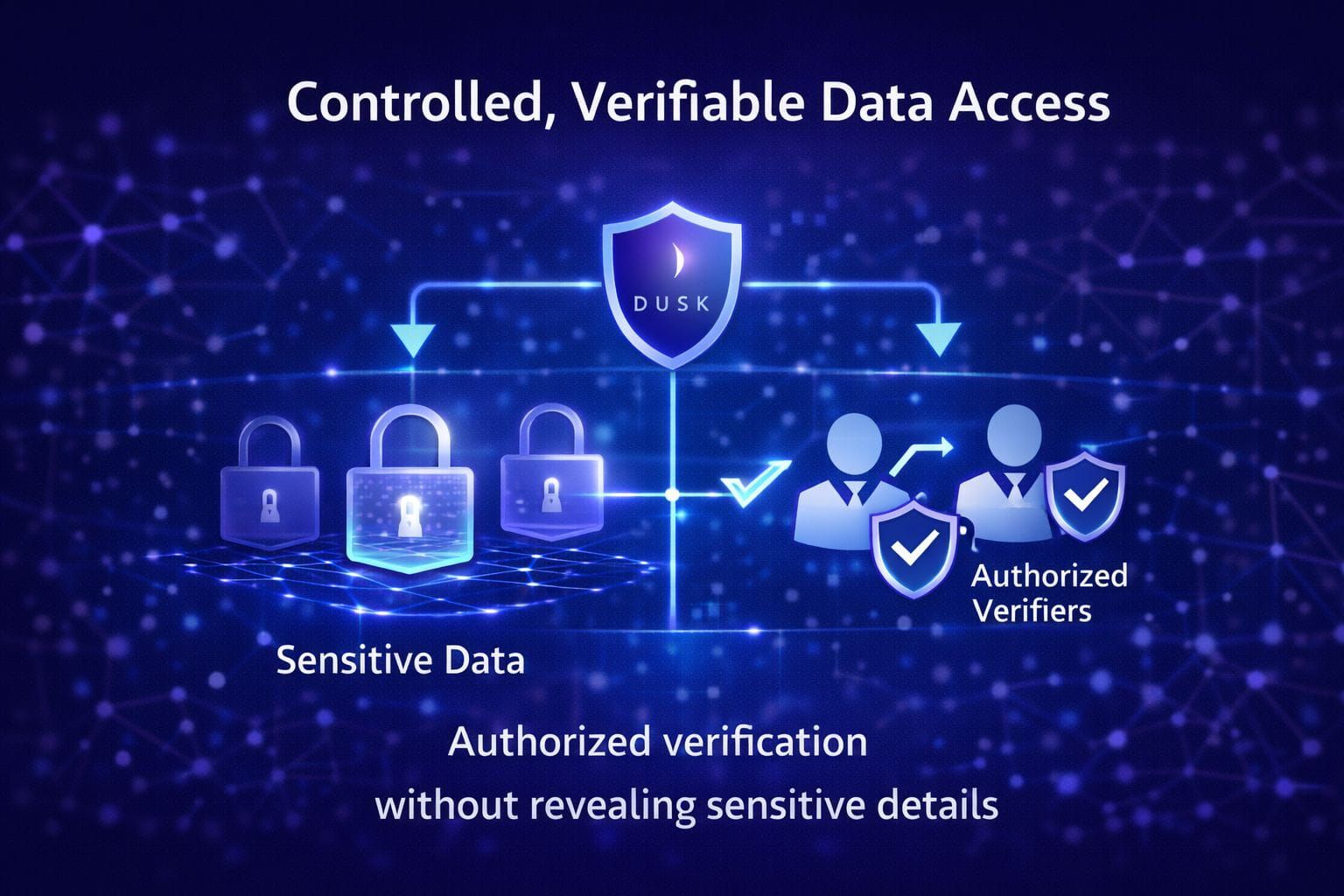
Institutions cannot expose sensitive information while maintaining verifiable operations. DUSK enforces selective data access at the protocol level, allowing authorized parties to verify transactions without revealing confidential details. Every node processes transactions identically, ensuring consistency and reproducibility.
This controlled verification reduces the need for manual reconciliation and simplifies audit processes. Compliance teams can rely on repeatable, verifiable outcomes, while automated workflows continue uninterrupted. Historical transactions can be replayed or validated without exposing internal strategies.
By combining deterministic execution with modular compliance and selective data visibility, DUSK provides predictable, auditable, and secure on-chain workflows. Enterprises can deploy regulated applications with confidence, knowing privacy, verification, and reliability are enforced by design.
